Contents:
Security researchers from Clearsky have recently revealed that Iranian threat actor Siamesekitten (a.k.a. Lyceum) has been targeting Israeli organizations through job offer-related lures.
According to the analysts, the campaign occurred between May and June 2021, and the Siamesekitten group was observed targeting IT and communication companies in Israel, most likely to facilitate supply chain attacks.
This campaign is similar to the North Korean “Job seekers” campaign, employing what has become a widely used attack vector in recent years – impersonation. Many attack groups are executing this type of campaign, such as the North Korean Lazarus campaign we exposed in the summer of 2020 (Dream Job) and the Iranian OilRig campaign (APT34) that targeted Middle Eastern victims in the first quarter of 2021.
Attack Chain
The attack sequence of Siamesekitten includes the following phases:
- Identifying the potential victim (employee).
- Identifying the HR department employee who may be impersonated.
- Establishing a phishing website that impersonates the targeted organization.
- Creating lure files compatible with the impersonated organization.
- Setting up a fraudulent profile on LinkedIn and impersonating the mentioned HR department employee.
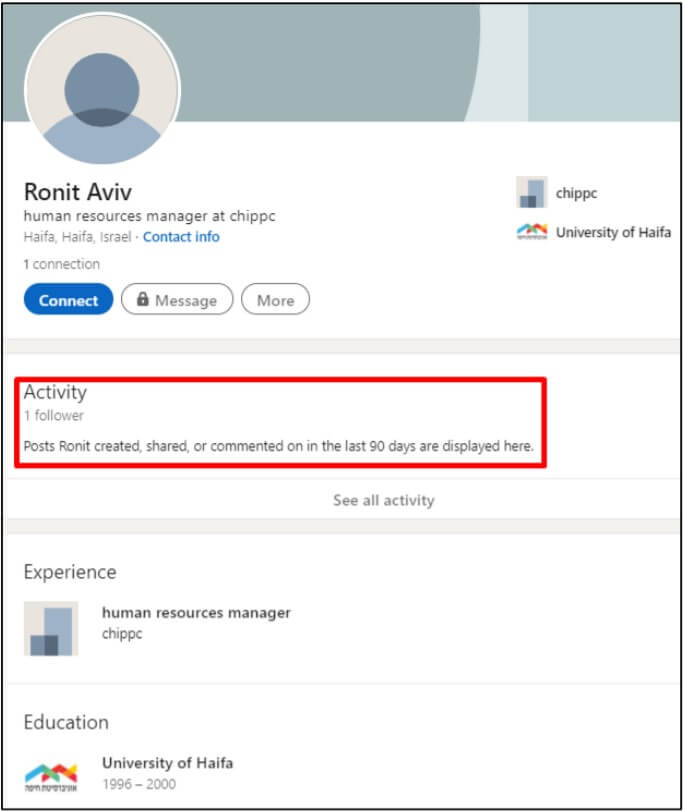
- Contacting potential victims with an “alluring” job offer, detailing a position in the impersonated company.
- Sending the victim to a phishing website with a lure file, including Excel files that provide details about the job offers and the company.
- The Milan backdoor malware infects the computer or server after one or more lure files are downloaded.
- The DanBot RAT is downloaded to the infected system.
- Through the infected machine, the group gathers data, conducts espionage, and attempts to spread within the network.
Siamesekitten Attack Tools
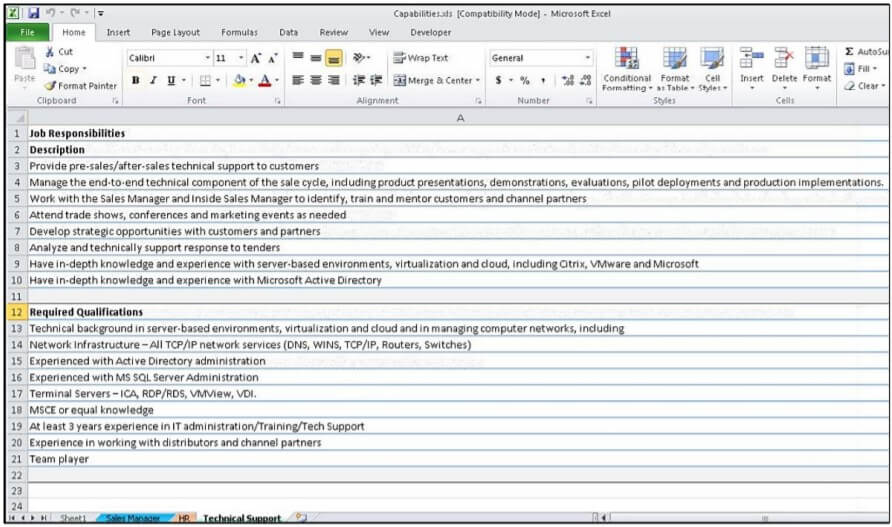
Back in May, the threat actors used an Excel spreadsheet with embedded macros. Named “Capabilities.xls”, it contained information concerning the different positions and their job requirements. The file would download Milan, a backdoor malware written in C++, on the infected computer.
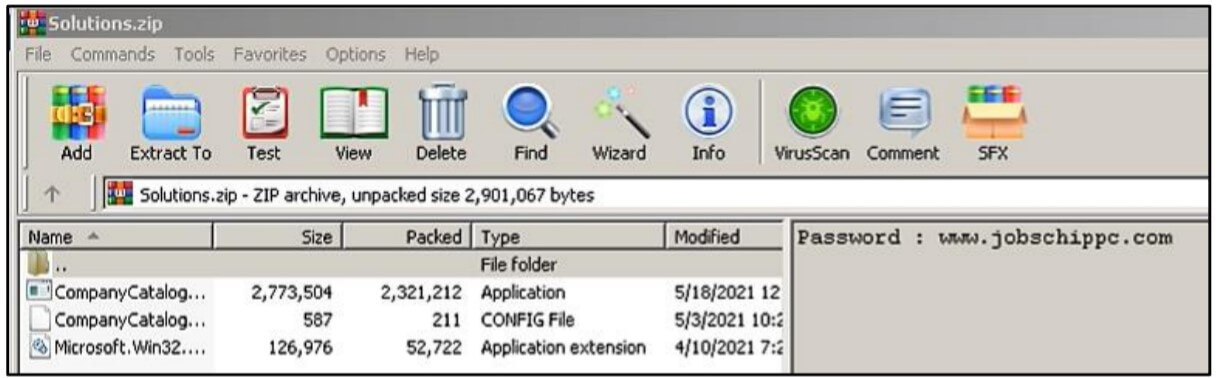
A new addition to the group’s methods was the executable file. The website contains a password-protected ZIP archive (the password is the domain impersonating the legitimate company) as well as the Excel file.
The archive contains three additional files:
- An executable named “companycatalog”.
- A configuration file named “companycatalog.exe.config”.
- A dynamic library that generates a scheduled task to execute the malware.
In the same campaign, the researchers identified a file that included two versions of the DanBot malware. The first file was named ‘UltraVNC.exe’ and the second ‘WINVNC.exe’. These two files are two versions of a remote control technique called Virtual Network Computing, a remote access software that has been converted to RAT.
In the July 2021 attacks, the researchers observed that the Milan backdoor was replaced with another new .NET backdoor dubbed Shark.
The malware requires the use of a parameter that contains part of the executed file’s name. The malware will generate a Mutex with the file’s name as its value to make sure that the malware does not run on the infected machine more than once. Executing the malware is also conditioned by the screen width being more than 600 pixels.
In the past, Siamesekitten has been known for targeting oil, gas, and telecom companies in the Middle East and Africa.
In 2019, the malicious group has disseminated numerous spear-phishing emails to high-profile targets in the oil and gas industry. The emails in question contained a malicious .xlsm file, which was rigged with an Auto-run macro to deploy DanBot. The malware was used to capture keystrokes, monitor network traffic, and steal credentials.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security