Contents:
During the weekend of 16th -17th October, a hacking competition took place in China, more specifically in Chengdu’s Sichuan province. The most prestigious and biggest competition in this sense in the country is called Tianfu Cup, basically a Chinese version of Pwn2Own.
16 Popular Software were targeted in the hacking contest and all, but three of them could be breached by the ethical hackers who took part in the competition.
What Was Targeted and What Eventually Was Hacked?
The targets were announced back in July to give participants three to four months’ time to prepare and come at the competition with original exploits with the possibility of a prize if successful. The participant ethical hackers could successfully breach Windows 10, Adobe PDF Reader, Ubuntu 20, Parallels VM, iOS15, Apple Safari, Google Chrome, ASUS AX56U router, Docker CE, VMWare ESXi, VMWare Workstation, qemu VM, and Microsoft Exchange.
Basically, the participants managed to hack all the proposed targets, except for 3 which were: Synology DS220j NAS, the smartphone Xiaomi Mi 11, and a Chinese electric vehicle (there is no information on the brand whatsoever).
In the figure below you can see how many times the targeted software were successfully hacked.

The Tianfu Cup Rules
The TianfuCup competition rules were clear: the ethical hackers had a time limit of 5 minutes to breach all the targets. They should make use of an original exploit and then breach the targets to demonstrate its functionality. For the attacks’ legitimacy, three five-minutes attempts were granted. It’s worth mentioning the prize pool which raised to nearly $2 million.
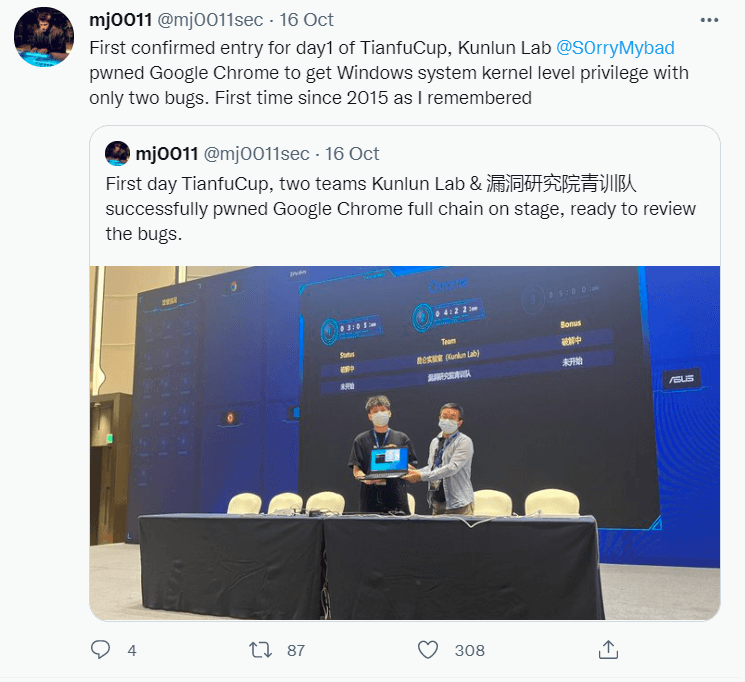
Kunlun Lab’s researchers were the ones who won this big competition owning a prize of $654,500, according to theRecord.media.
Two Hacks Stood Out
Out of all the hacks, two were remarkable. As HackRead explains:
- One cyberattack targeted an entirely patched iOS 15 that was running on iPhone 13. The vulnerability exploited there lied in the Safari mobile browser. The attack was basically a no-interaction RCE (remote code execution) and was conducted by the Pangu Team, known for their activity in jailbreaking mobile phones.
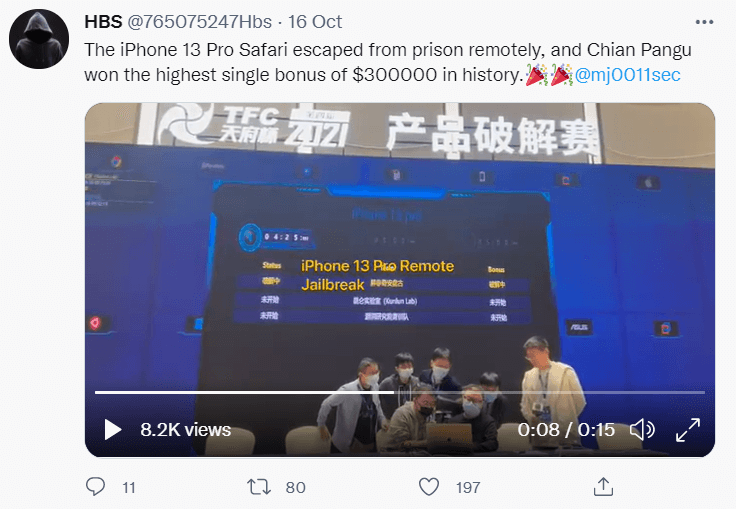
- The other remarkable attack was also a remote code execution one, this time against Google Chrome, which unfolded in 2 steps.
Hacking Competitions: Good or Not?
George Papamargaritis, the Obrela Security Industries’s security service director emphasized the positive aspects of a hacking competition:
The security researchers involved in these schemes can be an addition to existing security teams and provide additional eyes on an organisation’s products, meaning bugs will be unearthed and disclosed before cybercriminals get a chance to discover them and exploit them maliciously.
Another senior security intelligence engineer, by her name Kristina Balaam, told Forbes, that in terms of the negative aspects of a hacking competition one fact to be mentioned is the risk that participants might sell or exploit the vulnerabilities they found outside the contest.
However, it is known that there is a certain etiquette where is generally understood that the hackers’ exploits and vulnerabilities found will not be disclosed until vendors patch them.
What Did Microsoft and Google Say About It?
According to the same publication mentioned above, a Microsoft’s spokesperson declared that “all vulnerabilities reported as part of the contest are disclosed responsibly and confidentially. Solutions to verified security issues that meet our criteria for immediate servicing are normally released via our monthly Update Tuesday cadence.”
On the other hand, Google confirmed that patches will come out when a detailed investigation is finalized.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










