Contents:
In a blog post published yesterday, Google said that in 2021, it sent approximately 50.000 alerts to users whose accounts had been compromised by government-backed hacker gangs conducting phishing and malware campaigns.
The same post showed that it was a considerable increase in the number of warnings compared to the previous year.
Google Security Engineer Ajax Bash wrote:
So far in 2021, we’ve sent over 50,000 warnings, a nearly 33% increase from this time in 2020.
On any given day, TAG is tracking more than 270 targeted or government-backed attacker groups from more than 50 countries. This means that there is typically more than one threat actor behind the warnings.
An alert does not necessarily imply that your Google account has been compromised. Some attacks, such as phishing attempts, brute-force attacks, and malware delivery efforts, are successfully stopped by Google. The company sends the alerts when it has identified you as a target.
The security engineer stated that the company deliberately sends the warnings in batches to all users who may be targeted, rather than at the moment they notice the threat itself to prevent cybercriminals from tracking their defense strategies.
Google started to send alerts to its users when a state-sponsored cybercriminal attempted to access their accounts in 2012. According to BleepingComputer, the alert system has been “redesigned in 2017 and revamped with added info on the potential attack vector as seen in recent alerts sent in September.”
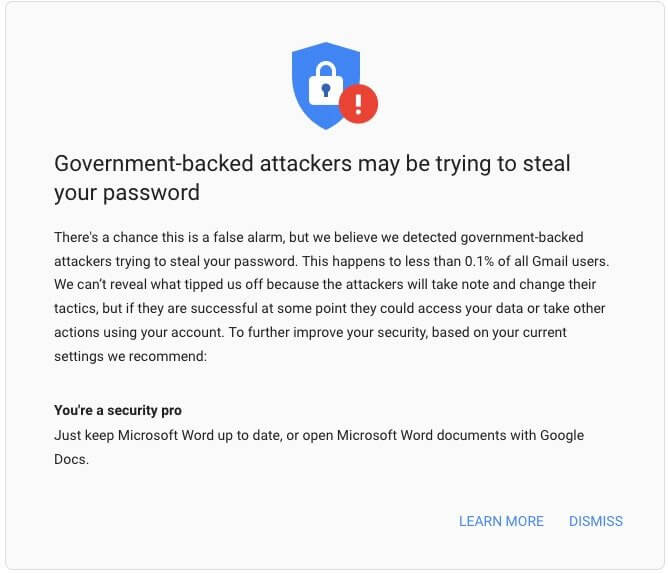
Hacking Groups APT 28 & APT 35 Are the Main Characters
The Russian-backed APT28 (aka Fancy Bear) hacking gang, which is connected to the GRU Russian military intelligence agency, and APT35 (aka Charming Kitten), an Iranian threat actor functioning since at least 2014, organized the most significant operations against Google users in 2021.
14.000 Gmail Users Targeted in Phishing Campaign
At the end of September, Google discovered that a large number of Gmail users from a wide range of businesses were being targeted by the APT28 hacking gang, a threat actor that has been operational starting with 2004.
Following the discovery of phishing emails, Google has immediately blocked them and alerted over 14,000 Gmail users about a phishing campaign targeting them.
Shane Huntley, Director of Google’s Threat Analysis Group (TAG) said this week that “this particular campaign comprised 86% of the batch of warnings we sent for this month.”
He notes that these warnings suggest recipient targeting rather than a breach of their Gmail account.
As we said in the article about this incident, Huntley declared that these warnings are normal for activists, reporters, government representatives, and individuals who work in national security systems as government-backed organizations usually go after them.
The second one, Charming Kitten, an Advanced Persistent Threat (APT) group believed to be Iran-based, also known as TA453, APT35, Ajax Security Team, NewsBeef, Newscaster, and Phosphorus is as dangerous as APT28.
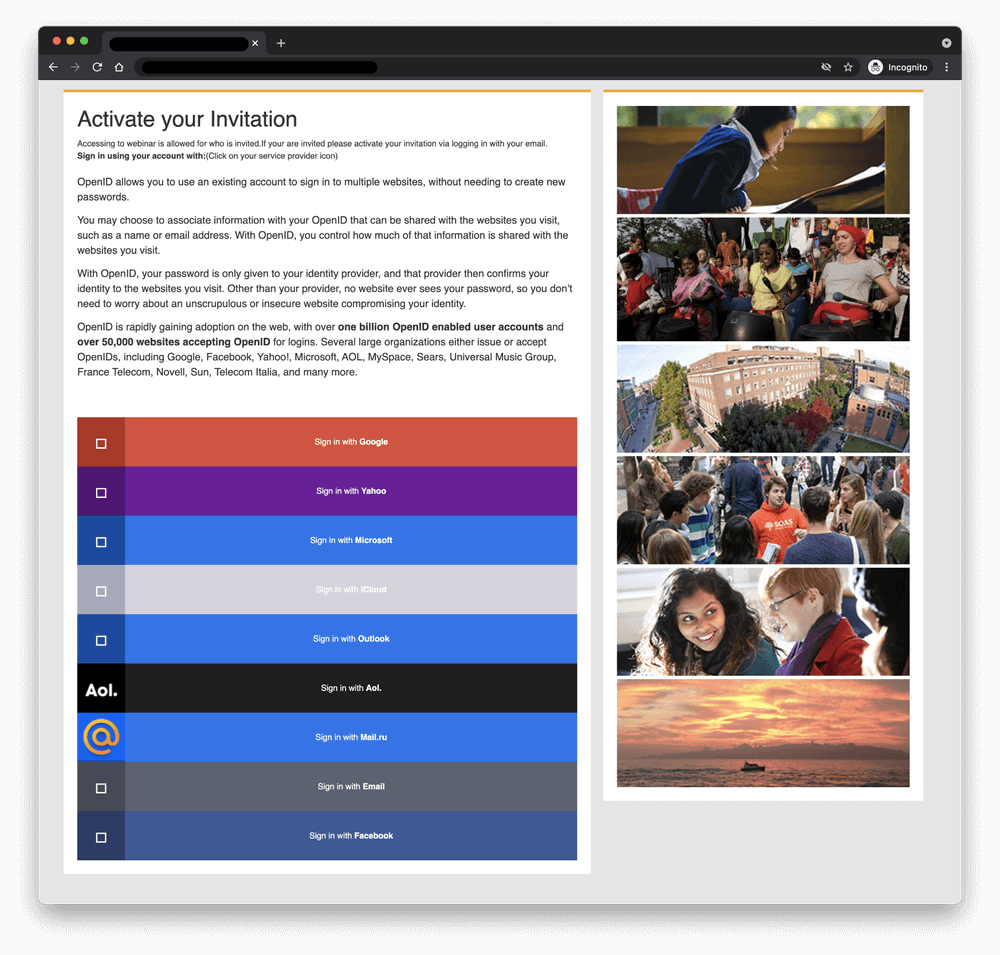
In a spear-phishing campaign that is believed to have started around January this year, APT35 was looking to get sensitive information as it impersonated U.K. academics focused on Middle Eastern affairs. According to researchers at Proofpoint, it was one of the most sophisticated campaigns conducted by the ever-evolving APT Charming Kitten.
The operation included impersonating British scholars working with the University of London’s School of Oriental and African Studies while engaging in conversations with victims and linking to the website of a legitimate, world-class, already compromised academic institution in order to collect credentials.
Users are encouraged to take these warnings seriously and consider enrolling in the Advanced Protection Program or enabling two-factor authentication if they haven’t already.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










