Contents:
Researchers have discovered 14 bugs and stated them in a report, known as INFRA:HALT vulnerabilities. Their target is none other than a popular proprietary TCP/IP stack. More exactly the NicheStack variants that rank below 4.3 are subjects to threat. Who uses this kind of library? The industrial sector, counting over 200 vendors.
How Can an Attack Due to INFRA:HALT Vulnerabilities Work?
All vulnerabilities were CVE classified. The ones who discovered them are the researchers from Forescout Labs and JFrog, the Forescout researchers having a project named Project Memoria that handles these issues.
According to Bleeping Computer, one of them, by his name Stanislav Dashevskyi, made a demonstration by taking one of the INFRA:HALT vulnerabilities and demonstrating how can it be exploited.
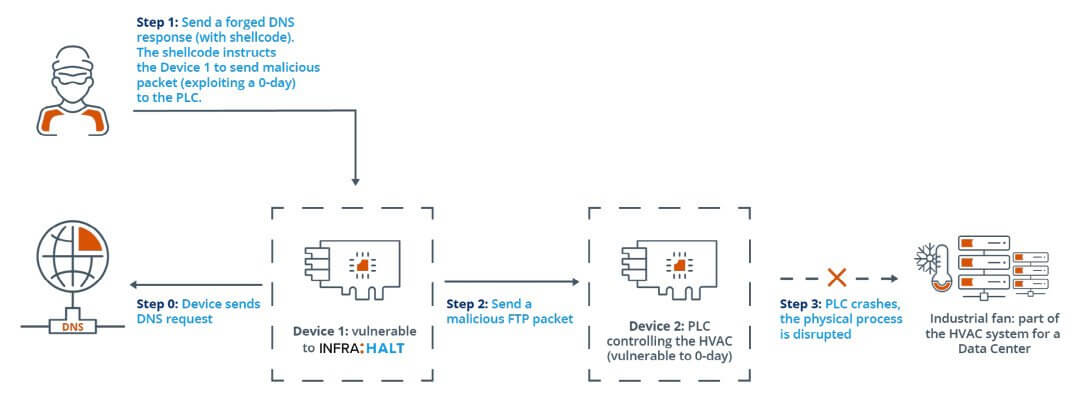
- He took CVE-2020-25928.
- What he did is to attack the PLC (programmable logical controller) that controls an industrial fan.
- The vulnerable device transmits, as usual, a DNS request to the DNS server.
- Though the DNS that responds to this request is controlled by the attacker, so it’s compromised with a bad shellcode.
- Then it’s time for the device to take action: it analyses the DNS response it receives.
- This is the time when the threat actors could execute remote control over the appliance.
- The hacker will make the affected machine initiate a TCP connection with another device, the inside PLC will then be linked with an HVAC.
- The compromised device sends then an FTP packet to exploit the found vulnerability in that PLC.
- The result? The PLC has no power to make the fan active anymore.
The 14 Vulnerabilities: What They Do and How Dangerous They Are
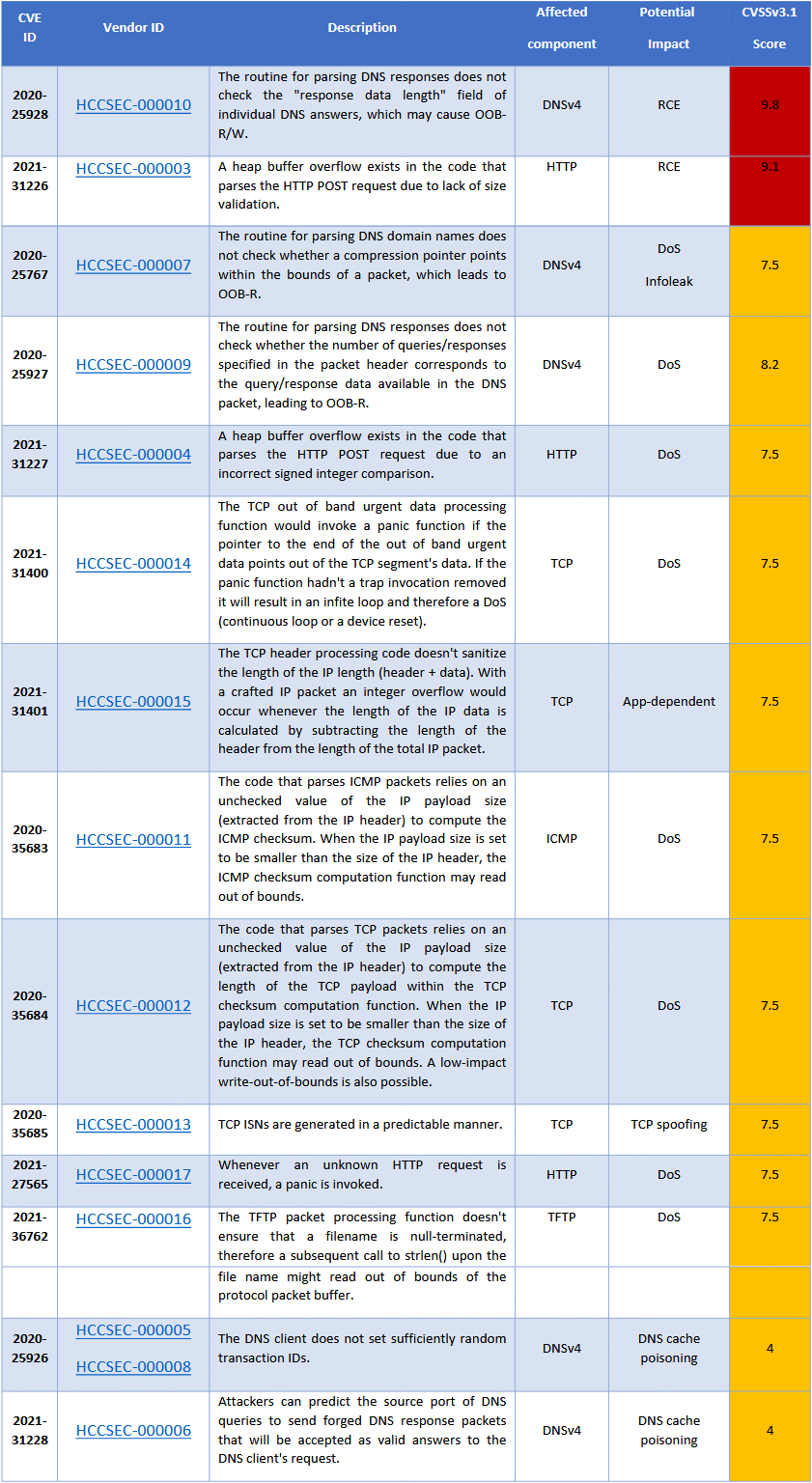
The new vulnerabilities allow for remote code execution, denial of service, information leak, TCP spoofing, or DNS cache poisoning.
The vulnerabilities pose a real threat to impacted devices. Most of them are high-security risks, but only 2 of them are critical. CVE-2020-25928 has a CVS score of 9.8 and CVE-2020-31226 has a score of 9.1.
However, they can be exploited only if hackers manage to get access to the internal network of the organizations. Granting access to the office network is not enough, but managing to connect to the OT section makes way for their malicious actions. Why? Because all the industrial equipment is deployed on that network.
How Many and What Devices Are Exposed?
The number of affected industrial devices that use NicheStack raise to 6400.
Among targeted companies, these can be mentioned, that are NicheStack’s clients, known as InterNiches now because it’s under HCC Embedded at the present moment: Schneider Electric, Rockwell Automation, Honeywell, Emerson, Mitsubishi Electric, and Siemens.
According to the Forescout report, 21 vendors’ systems (2500) are impacted by these vulnerabilities.
What Measures Have Been Taken?
HCC Embedded has taken the necessary measures and provided the proper patches that customers are urged to immediately apply. In short, all devices should be updated with the NicheStack 4.3 version.
Researchers from JFrog and Forescout also shared their mitigation recommendations where the above-mentioned patches cannot function:
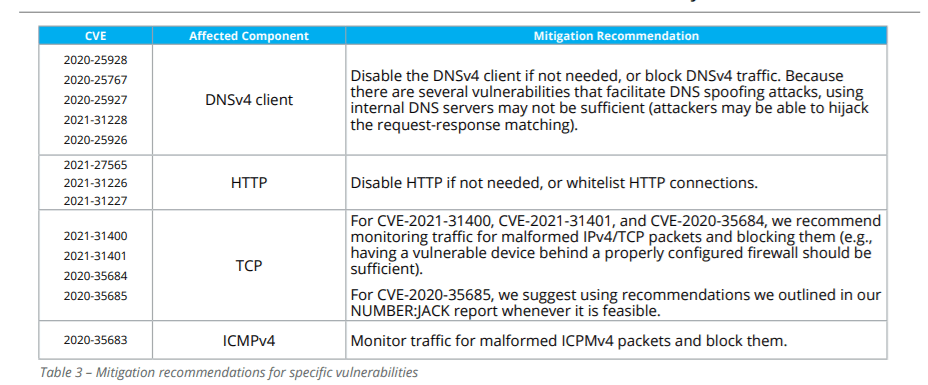
Also, according to the same report, researchers recommend to device vendors, network operators, and the cybersecurity community in general to:
- Perform an audit in order to detect the NicheStack running machines. They can do this by using the script provided by Forescout.
- External communication should be restricted and detected vulnerable devices should be kept apart from those running well until they are patched.
- Keep up to date with the patches.
- The traffic should be monitored: because hackers can use data packets to exploit o-day bugs.
- A tool that performs an audit on code can be also useful.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










