Contents:
Cybercriminals are installing a new malicious add-on for the IIS web server on Microsoft Exchange Outlook Web Access (OWA) servers to collect login information and remotely perform commands on the server. The malicious IIS web server software is called ‘Owowa’ and, according to researchers, it could be extremely dangerous.
Based on data gathered and published to the internet security, file, and URL analyzer VirtusTotal, it seems that Owowa’s development began in late 2020.
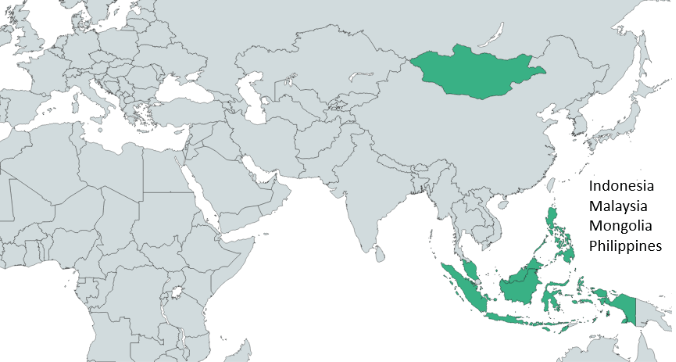
According to Kaspersky‘s telemetry data, the most recent sample in circulation dates from April 2021 and focuses on servers in Malaysia, Mongolia, Indonesia, and the Philippines.
The systems targeted by this malicious IIS web server software belong to government entities and state agencies.
Signs of Owowa in Europe
As per Kaspersky researchers, the ‘Owowa’ targets aren’t confined to Southeast Asia, with infections being detected in Europe as well.
Web shells, which enable cybercriminals to execute commands remotely on a server, are frequently used against Microsoft Exchange servers, and they are typically the focus of defenders.
This is why employing an IIS module as a backdoor is a great strategy to remain anonymous. Hackers can send apparently harmless authentication requests to OWA and also elude typical network monitoring procedures.
IIS modules are not a common format for backdoors, especially when compared to typical web application threats like web shells and can therefore easily be missed during standard file monitoring efforts.
Furthermore, the infection stays even after the Exchange software is updated, so the infection needs to happen only once.
According to Kaspersky, the attacker may be depending on ProxyLogon weaknesses to breach the server, which continues to be a threat even after being fixed nine months ago. The attackers, on the other hand, didn’t do a flawless job with Owowa’s design, failing to conceal PDB paths in the virus executable and, in some instances, triggering server failures.
So, How Dangerous Is this Malicious IIS Web Server Software?
As explained by BleepingComputer, Owowa is developed to log the credentials of users that successfully authenticate on the OWA login web page. It specifically impacts Outlook Web Access (OWA) applications on Exchange servers.
The login success is confirmed automatically by tracking the OWA application to generate an authentication token.
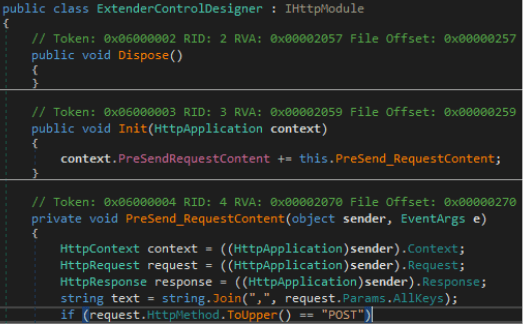
When this happens, Owowa saves the user’s username, password, IP address, and current timestamp and encrypts the information with RSA (Rivest–Shamir–Adleman), a public-key cryptosystem that is widely used for secure data transmission.
Afterward, the attacker is able to manually send a command to the malicious module to gather the stolen information.
Remote commands can also be used to run PowerShell on a corrupted machine, allowing for a variety of attack options.
The cybercriminals only need to access the OWA login page of a compromised server to enter specially crafted commands into the username and password fields.
This is an efficient option for attackers to gain a strong foothold in targeted networks by persisting inside an Exchange server.
What Is There to Do?
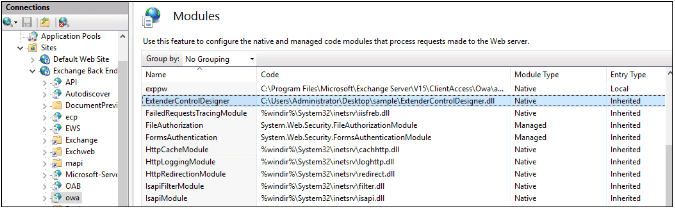
In order to obtain a list of all loaded modules on an IIS server, system administrators can use the command ‘appcmd.exe’ or the IIS setup tool.
According to the researchers, in the situations they’ve seen, the malicious module goes by the name “ExtenderControlDesigner”.
Although the identity of the hacker remains unknown, the clumsiness with which the module was developed suggests an inexperienced threat actor.
In conclusion, this is yet another reminder of the significance of constantly verifying your IIS modules, looking for evidence of lateral movement, and having a good endpoint security solution in place.
How can Heimdal™ Help You Secure Your Endpoints?
The Heimdal™ EDR suite of cybersecurity solutions incorporates threat prevention, patching, privileged access management, and a next-generation antivirus that will cover all your bases at an enterprise level. By adding state-of-the-art DNS traffic filtering, vulnerability management, access governance, threat detection, and incident response to your network, you will stop cyber attackers in their tracks before they even start to consider targeting your business.
Consisting of practices of prevention, detection, and response (EPDR), Heimdal’s EDR suite is the modern standard for cybersecurity, due to its focus on prevention on top of detection and response.

- Next-gen Antivirus & Firewall which stops known threats;
- DNS traffic filter which stops unknown threats;
- Automatic patches for your software and apps with no interruptions;
- Privileged Access Management and Application Control, all in one unified dashboard
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










