Contents:
Since early 2020, over 250 domains have been used to spread information-stealing malware such as Raccoon and Vidar, according to an analysis recently published by cybersecurity researchers.
As per the French research team, the domains are managed by a threat actor running a traffic direction system (TDS), that could be rented by other hackers to distribute the malware.
The associated infection chain, leveraging this infrastructure of over 250 domains, uses about a hundred of fake cracked software catalogue websites that redirect to several links before downloading the payload hosted on file share platforms, such as GitHub.
Luring Victims into Downloading Malware via SEO Poisoning
The attacks aim at users searching for cracked versions of software and games on search engines such as Google, surfacing fraudulent websites on the first page by leveraging a technique known as search engine optimization (SEO) poisoning to trick victims into downloading and executing the malicious payloads.
When a user clicks on the poisoned result’s download link, they are taken through a five-step URL redirection sequence that ultimately leads them to a webpage showing a shortened link that leads to a password-protected RAR archive file hosted on GitHub, along with its password, explains The Hacker News.
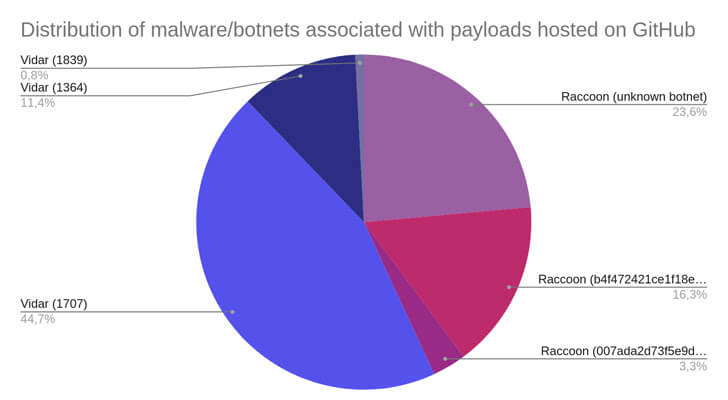
Malware/Botnet Distribution
Both the Raccoon and Vidar malware families are installed if the victim decompresses the RAR archive and runs the fraudulent setup executable it contains.
An alternative form of the attack chain has been spotted using phishing emails disguised as bank statements to trick unsuspecting users into clicking on bogus links.
Both kinds of malware are capable of extracting a variety of personal data from infected computers, gathering login information from web browsers, and stealing information from different cryptocurrency wallets.
The researchers encourage users to avoid installing illegal software and, whenever possible, to use multi-factor authentication(MFA) to secure their accounts.
We highly recommend only downloading and installing software from trusted, official websites. Beyond the indicators of compromise, detection teams can hunt for infection chains leveraging fake cracked software by searching for weak signals, such as communications to unusual TLD and to URLs containing IP addresses, or looking for suspicious file names.
The full analysis published by SEKOIA is available here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










