Contents:
Honeypots are designed to trick attackers into thinking they’ve found a real machine.
The goal is to deceive them into committing attacks against a fake system, thereby uncovering their tactics and network behaviors. Many organizations use honeypots alongside website security software to improve their intrusion prevention and detection systems (IDPS).
In this article, we’ll take a look at honeypots and explain how you can use them to help your business defend against cyber attacks.
What is a honeypot?
A honeypot is a decoy system designed to lure cyber attackers and study their motives, techniques, skillset, and behaviour. It’s deployed alongside production systems on the network and pretends to be an attack surface.
Honeypots are based on deception technology. They masquerade as a part of the network vulnerable to a cyber attack, but the real network stays protected and well monitored. Organizations involved in cybersecurity research typically use honeypots to protect against advanced persistent threats (APTs). These companies get substantial insights into cyber attackers’ tools and techniques, as well as their own networks’ vulnerabilities, with the help of active defense set in place.
According to a survey, 72% of respondents either already use or are willing to use honeypots or similar technologies.
However, honeypots can be costly to maintain since they require an expert to monitor the system and understand attack tactics while preventing a cybercriminal from penetrating through their actual network.
Types of honeypots
Honeypots are classified into different types based on their design, deployment, complexity, and usage.
Production honeypots
Security teams deploy this type close to production servers in a network. It makes attackers move toward the decoys and away from the actual server. Production honeypots help security professionals understand the nature of threats and effectively manage vulnerabilities.
Production honeypots look lucrative because they appear to hold sensitive information, serving as bait for malicious hackers.
Research honeypots
Security professionals use a research honeypot for education and training while strengthening their security posture. They hold trackable data that helps the security team analyze and respond to security incidents and understand how the company can protect its systems.
Research honeypots are generally used by the government and research organizations. Unlike production honeypots, they’re much more complex and provide more detailed insights.
Pure honeypots
Pure honeypots represent a full-scale production system running on multiple servers. These are complex and might pose maintenance challenges since they require so much effort and attention to keep them operational.
Pure honeypots have data that appears to be confidential or sensitive, but in reality, it has no value. You can track this data and draw actionable information about a cyber attack.
High-interaction honeypots
Security experts design these to get attackers to spend more time within a honeypot. This opens up several opportunities for the security teams to detect weaknesses and understand the ways attackers can exploit them.
High-interaction honeypots let attackers gain administrative or root-level privileges and monitor them navigating the deception technology.
Mid-interaction honeypots
Mid-interaction honeypots mimic the application layer of the open system’s interconnections (OSI) model and aren’t connected to any operating system. The application layer interacts directly with user data. It establishes protocols that enable software to communicate and receive data to present users with helpful information.
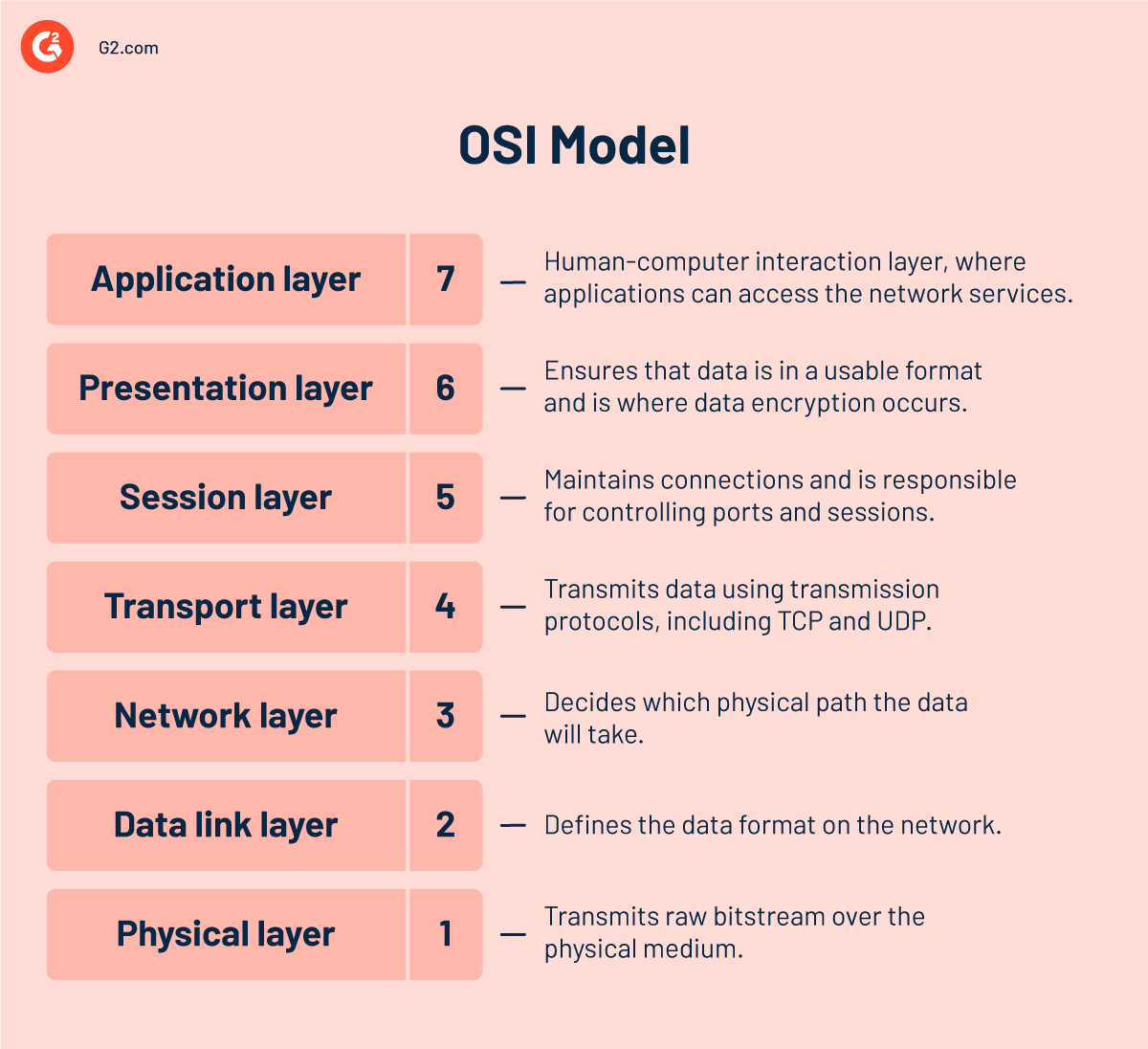
Mid-interaction honeypots are used to stall the attackers so that security teams get enough time to study an attack and come up with relevant preventative or mitigation measures.
However, they can also become a pathway for attackers to infiltrate your network without an operating system, making it exploitable.
Low-interaction honeypots
Low-interaction honeypots are comparatively simpler to set up and don’t require a lot of computational resources. They use TCP and IP simulating common attack vectors on the network.
These honeypots can appear fake to an attacker and might not engage threat actors for a long time. However, security teams can use them to detect attacks from malware or bots.
Specialized honeypot technologies
Apart from the ones mentioned above, a few specialized honeypots are suitable for different purposes and requirements.
- Spam honeypots can emulate open proxies and open mail relays, detecting spammer’s tests and blocking them. Spammers test mail relays by trying to send themselves an email first and then sending in large quantities if they succeed.
- Malware honeypots replicate attack vectors of malware. For example, if a computer is infected by malware that spreads through USB devices, malware honeypots trick attackers into interacting with the USB. This will help security teams detect the presence of malware.
- Database honeypots create decoy databases to detect database-specific attacks like structured query language (SQL) injection.
- Honeynet comprises a network of honeypots designed to detect multiple attack types such as distributed denial-of-service (DDoS) attacks and content delivery network (CDN) attacks. Security teams can use them to track the methods and motivations of an attacker and keep track of all inbound and outbound traffic.
How honeypots defend against cyber attacks
Honeypots are generally placed in the demilitarized zone (DMZ), also known as the DMZ network. These sub-networks act as a buffer between an organization’s private network and the internet. It adds an extra layer of protection against untrusted traffic while allowing security analysts to monitor them from a distance.
Based on how elaborate a honeypot is or the kind of traffic it’s going to attract, its placement can vary. Experts might also consider placing it outside the external firewall to observe attempts to access the internal network. Regardless of the placement, a honeypot maintains distance from the production environment.
Honeypots create deception through application and data that is critical or lucrative to cyber attackers. When attackers try to access this data, their attempts alert security professionals. Honeypots help security teams improve their intrusion prevention and detection system, which eventually allows them to defend better against cyber attacks. By deploying a honeypot, security experts can understand how one vulnerability can be exploited in multiple ways and take measures to fix security weaknesses.
Below are some ways honeypots help security teams protect against cyber attacks. :
- Collects valuable data. Data collected when an attacker interacts with a honeypot is full of useful information and fewer false positives than data aggregated from other detection technologies. Security teams use this data to organize their strategies and set protective measures.
- Circumvents encryption. Even when an attacker uses encryption, honeypots help teams detect cybercrime or any malicious activity.
- Reduces human effort. With honeypots, there’s no need to adopt high-performance resources to scan through heavy volumes of network traffic. It’s easy to set up, maintain and monitor. A security professional doesn’t have to constantly monitor the decoy network. They know as soon as someone interacts with it.
- Strengthens internal team’s response. Honeypots can be used to test how security teams would respond to an active cyber-attack, helping identify areas of improvement.
- Protects sensitive information. Attackers can move both horizontally and vertically through systems and networks. A honeypot allows teams to trap an attacker when they engage with it and understand hackers’ methods. It also allows organizations to divert threat actors toward fake data while protecting sensitive information.
- Identifies insiders. Honeypots enable security teams to recognize and catch malicious insiders who intend to access and exploit an organization’s sensitive data.
Trick the trickster
Honeypots play a critical role in identifying an enterprise’s information security vulnerabilities. At a basic level, their inherent capabilities allow organizations to gain crucial intelligence about the attacks that hackers are perpetrating against their networks. It helps trick attackers into revealing their malicious methods and motives.
However, honeypots should be used carefully and cautiously. An attacker can also use them to understand their target’s incident response tactics. It’s better to have trained security experts manage honeypots on the network to gather actionable intelligence about threat actors.
Learn more about common network vulnerabilities and keep your systems safe against cyber-attacks by using these preventive measures.
About the Author

Sagar Joshi is a content marketer at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing snooker in his free time.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









