Contents:
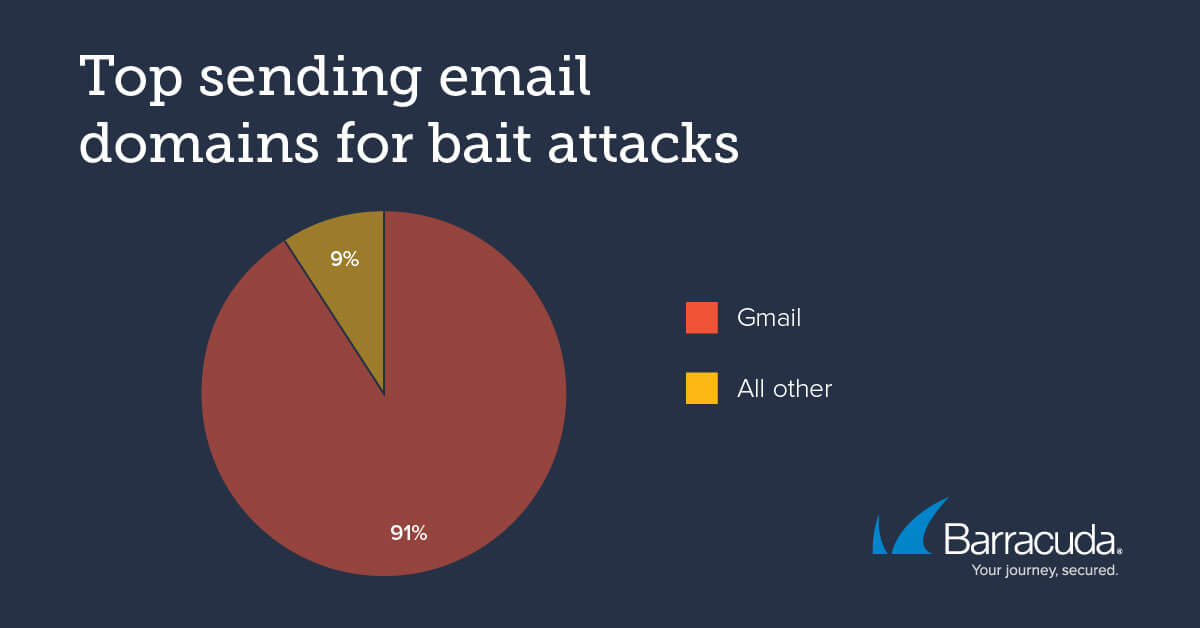
As the frequency of bait attacks, also known as reconnaissance attacks, increases, it seems that cybercriminals who send this type of phishing email choose to run their operations using Gmail accounts.
According to a survey conducted by Barracuda experts, almost 40% of the 10,500 businesses analyzed were targeted by at least one bait attack in September 2021, with each company receiving one of these emails in an average of three different mailboxes.
What Is a Baiting Attack?
A threat actor uses a baiting attack to just gather information about an individual or corporation in order to plan future attacks. Bait attacks are typically delivered in the form of emails with very short or even empty content.
The purpose of this type of attack is merely to verify the existence and accessibility of the receiver’s email, which is achieved if the threat actor receives a no “undeliverable” notification or, better yet, gets an answer from the target. Another goal is to test the effectiveness of automated spam-detection solutions.
Traditional phishing detectors struggle to defend against this class of threats because they contain little text and no phishing links or malicious attachments.

Gmail, the Biting Attack’s Favorite
Threat actors usually go for Gmail as it is a widely used free email service that users associate with credibility and trustworthiness.
Furthermore, Google’s email service serves as a platform that facilitates the creation of pseudonymous accounts quickly and easily.
Lastly, Gmail provides a “read receipt” feature, which informs the malicious senders that the target read the email even if they did not respond.
And jackpot! The biting attack’s goal is accomplished. That is the moment when the threat actors see the mailbox is valid and actively used.
The Experiment
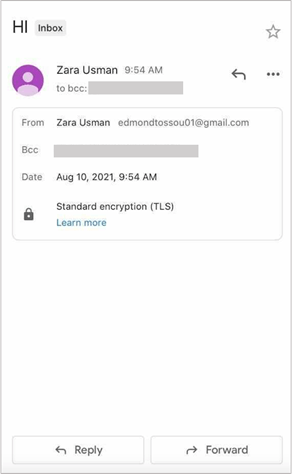
The Barracuda research team decided to conduct an experiment and responded to a baiting attack that had arrived in one of its staff’s mailboxes.
On August 10, 2021, the initial attack consisted of an email with the subject line ‘HI’ and no additional text.
On August 17, 2021, the employee experienced a targeted phishing attack. The first email was intended to confirm the existence of the target’s inbox and their willingness to react to email messages.
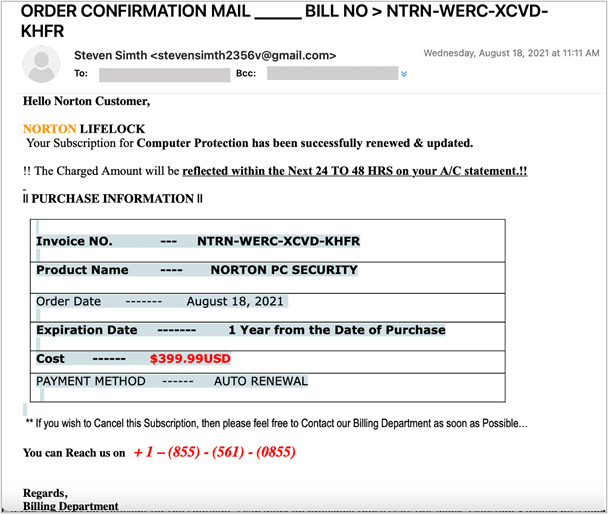
It’s important to note that potential victims don’t even have to respond to these email messages to verify that they’re vulnerable to email-based attacks. It is recommended that whenever you receive this type of email, send it right to trash without reading it.
How Can Heimdal™ Help You?
HeimdalTM Security has developed two email security software aimed against both simple and sophisticated email threats (Heimdal™ Email Security), which detects and blocks malware, spam emails, malicious URLs, and phishing attacks and Heimdal™ Email Fraud Prevention, a revolutionary email protection system against employee impersonation, fraud attempts – and BEC, in general.
For example, you may want to consider HeimdalTM Security’s Heimdal™ Email Fraud Prevention, the ultimate email protection against financial email fraud, C-level executive impersonation, phishing, insider threat attacks, and complex email malware. How does it work? By using over 125 vectors of analysis and being fully supported by threat intelligence, it detects phraseology changes, performs IBAN/Account number scanning, identifies modified attachments, malicious links, and Man-in-the-Email attacks. Furthermore, it integrates with O365 and any mail filtering solutions and includes live monitoring and alerting 24/7 by our specialists.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










