Contents:
GETTR is a new pro-Trump social media platform that was created by the former Trump advisor Jason Miller to be used as an alternative to Twitter after the platform banned Donald Trump back in January.
After close review of recent Tweets from the @realDonaldTrump account and the context around them — specifically how they are being received and interpreted on and off Twitter — we have permanently suspended the account due to the risk of further incitement of violence.
In the context of horrific events this week, we made it clear on Wednesday that additional violations of the Twitter Rules would potentially result in this very course of action. Our public interest framework exists to enable the public to hear from elected officials and world leaders directly. It is built on a principle that the people have a right to hold power to account in the open.
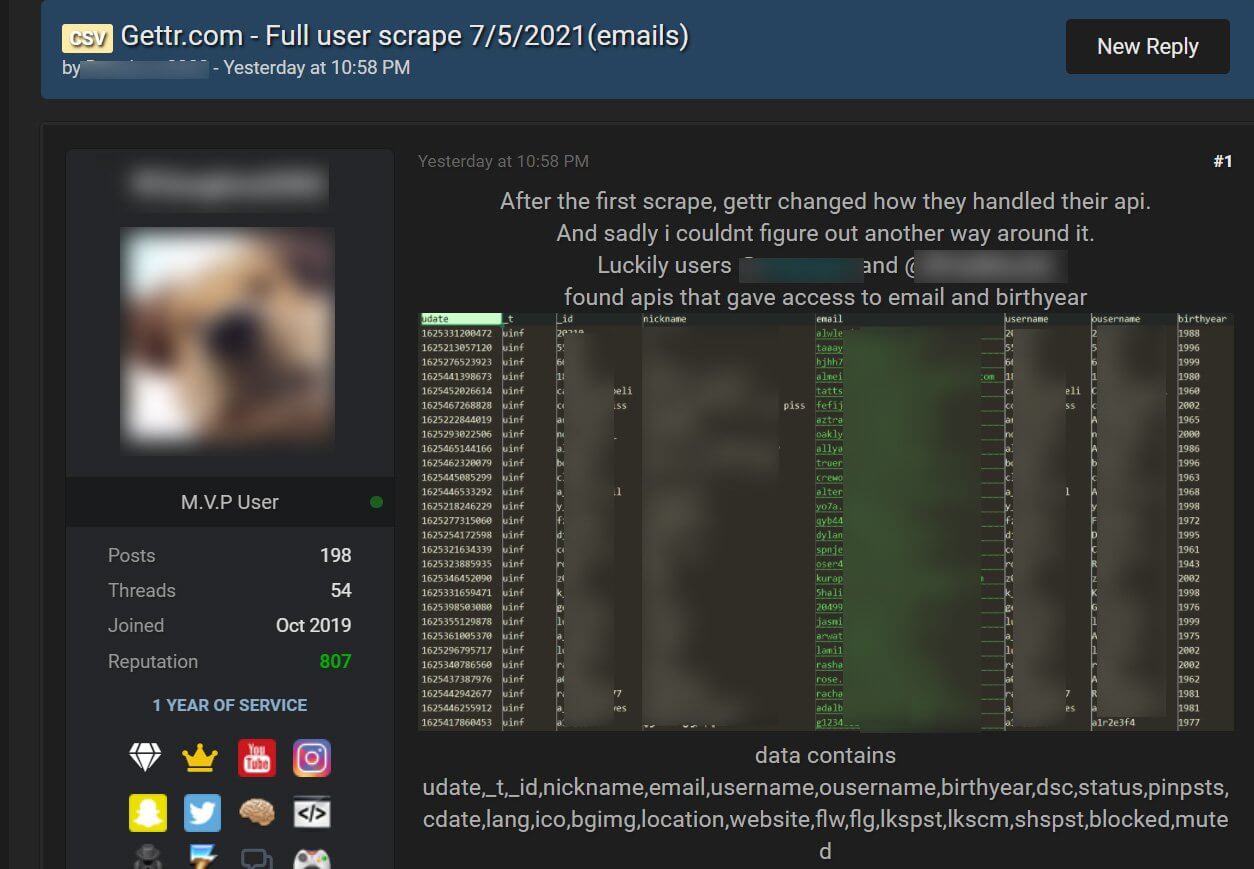
GETTR platform suffered a data breach after a cyberattack in which a hacker claimed to have used an unsecured API in order to scrape the private information of almost 90,000 members, and then he shared the collected data on a hacking forum.
Alon Gal, the co-founder of Hudson Rock, discovered that a group of hackers found an unsecured application programming interface (API) that allowed them to scrape the data for 87,973 GETTR members, and after compiling the information they published the data to a hacking forum that is usually used to share databases stolen during data breaches.
Threat actors were able to take advantage of bad API implemented on Trump’s recent social media platform, Gettr (@GettrOfficial).
This allowed them to extract usernames, names, bios, bdays, but most importantly, the emails which were supposed to be private, of over 85,000 users. pic.twitter.com/NsKyz9zHmQ
— Alon Gal (Under the Breach) (@UnderTheBreach) July 6, 2021
According to Gal, the incident should be considered a data breach.
When threat actors are able to extract sensitive information due to neglectful API implementations, the consequence is equivalent to a data breach and should be handled accordingly by the firm and to be examined by regulators.
The hacker that managed to steal the data says that they made use of an unsecured API in order to scrape public profile data of GETTR users, but this API was later secured.
The attack did not stop here, as another member of the hacking forum discovered another API that was unsecured therefore allowing for the scraping of public information and a member’s private email address and birth year.
The journalists at BleepingComputer said that the scraped information includes a member’s email address, nickname, profile name, birth year, profile descriptions, avatar URL, background images, location, personal website, and other internal site data.
GETTR Data Breach
Large amounts of the leaked information are available just by visiting a GETTR user’s profile but a user’s email address, location, and birth year are not publicly available.
Even if most leaked GETTR account information is accessible publicly, the email addresses, birth year, and locations are not meant to be accessible to other users, and unfortunately, this type of private information can be used by malicious actors wanting to perform targeted phishing attacks aimed at gathering further sensitive information, such as login passwords.
As a consequence of this breach, the GETTR users should be paying attention to any phishing emails that are pretending to be from GETTR, and upon receiving these emails users should delete them right away and not enter their credentials.
Not the First Problem that GETTR Faces
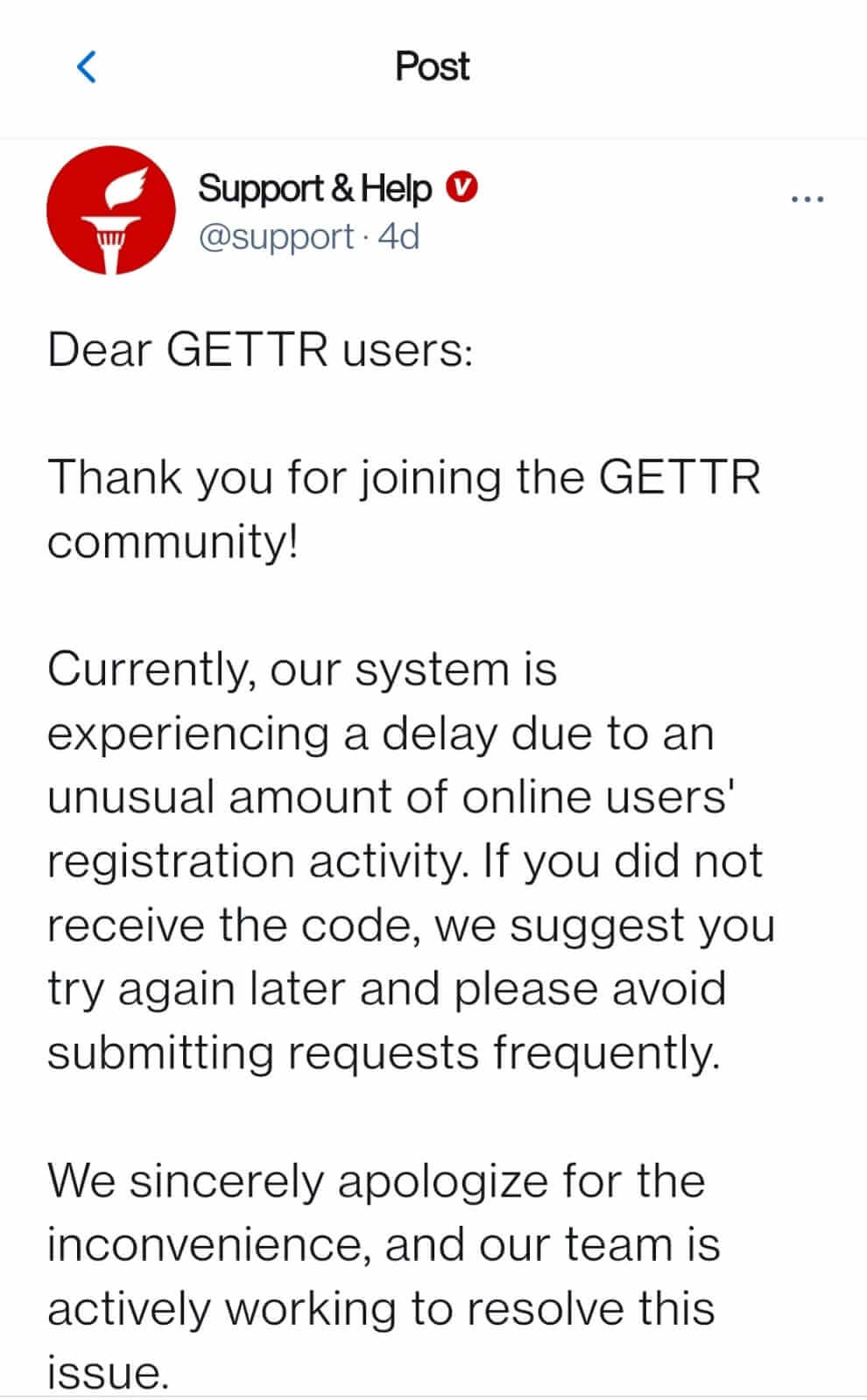
The app went live in the App Store and Google Play last month but only left beta on July 4, as on July 2, with the app’s team was apologizing for the signup delays by blaming a spike in downloads.
Over the weekend the platform’s most popular verified users had their accounts compromised, therefore the accounts of Mike Pompeo, Steve Bannon, Marjorie Taylor-Greene, Harlan Hill, Sean Parnell, and others were also hacked.
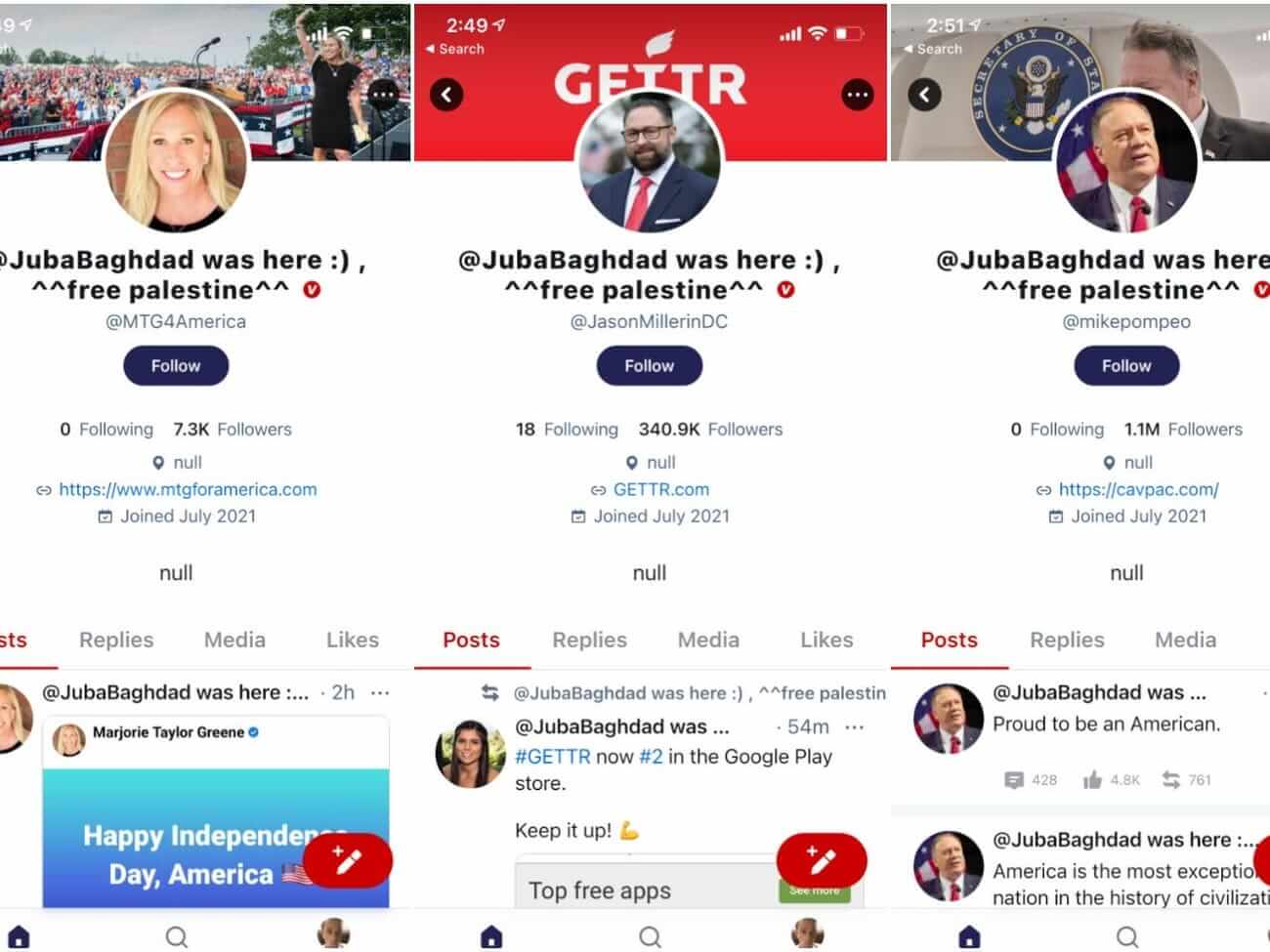
All of these account’s profiles were changed to show the same message: “@JubaBaghdad was here 🙂 ^^ free palestine ^^.”
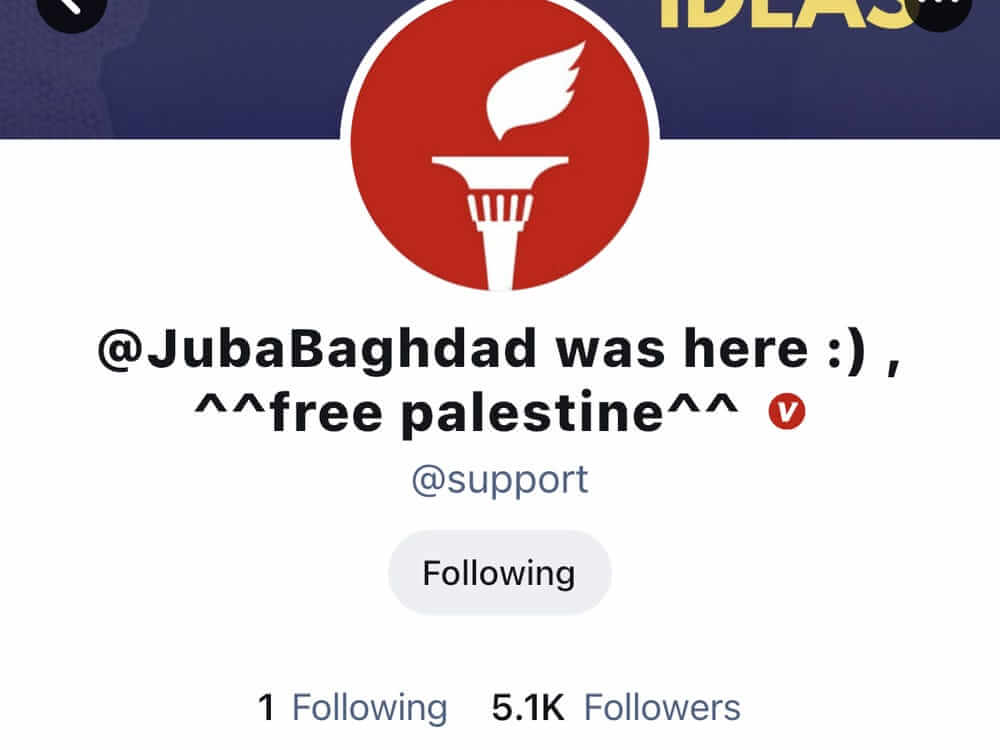
@JubaBaghdad said he is a “bounty hunter” of software bugs, tracking down and reporting problematic code in exchange for a financial reward and declared for Insider that although GETTR fixed the initial bug he said he used in the attack, he was still able to scrape user data from individual accounts, including email addresses and birth years.
They should not publish the website before making sure everything, or at least almost everything is secure.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security