Contents:
In a credential phishing attack intended to steal users’ Microsoft Office 365 and Google email passwords, hackers posed as the American business security company Proofpoint.
Armorblox cybersecurity researchers revealed that they discovered one such operation aimed at an unidentified international communications company, with virtually a thousand employees targeted solely within that organization.
The email claimed to contain a secure file sent via Proofpoint as a link. Clicking the link took victims to a splash page that spoofed Proofpoint branding and contained login links for different email providers. The attack included dedicated login page spoofs for Microsoft and Google.
The Operation
A file apparently related to mortgage payments was the email’s bait. The subject line, “Re: Payoff Request,” was designed to trick victims into believing it was part of an ongoing conversation, adding credibility to the operations while also making it seem urgent enough and convincing them to click it.
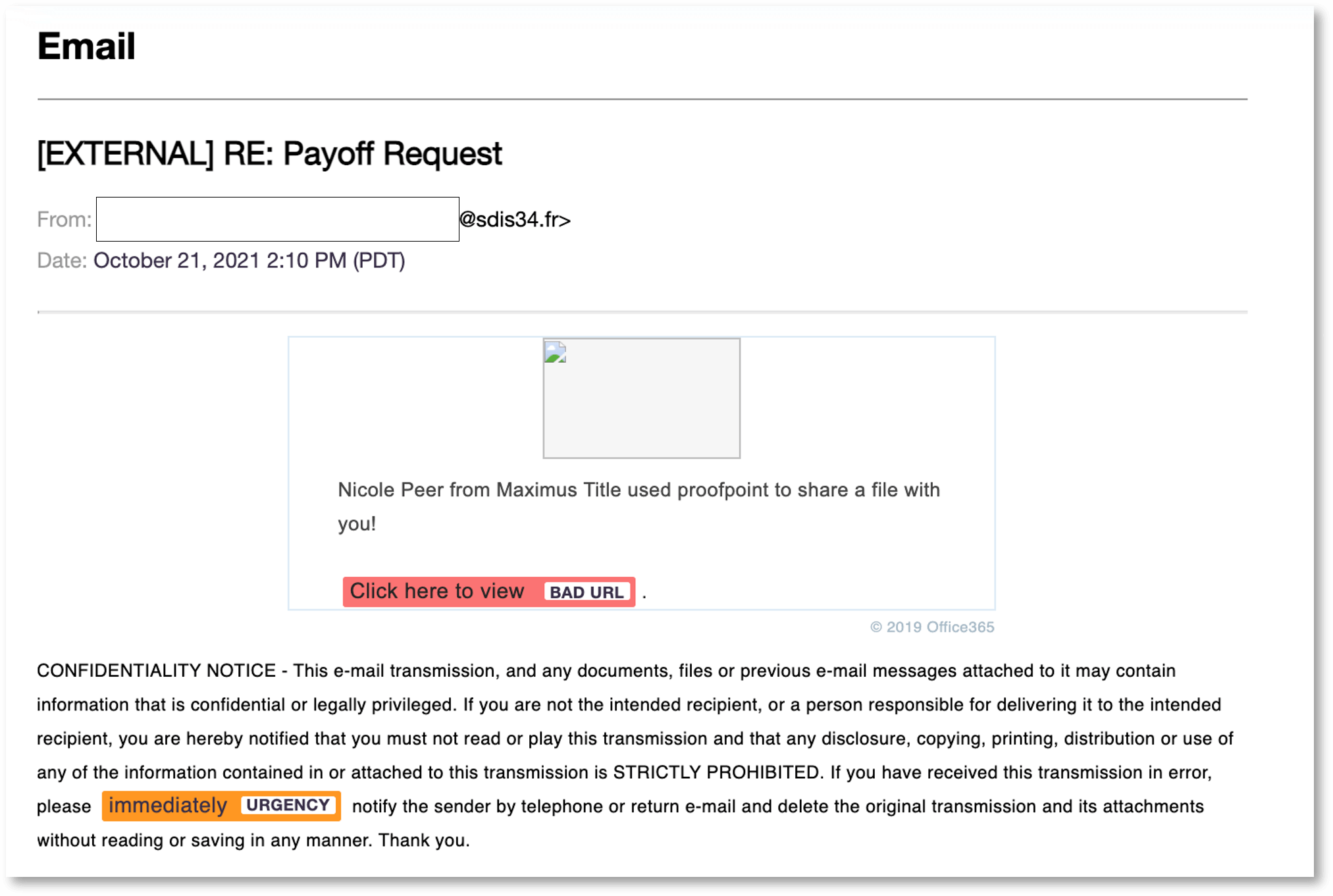
The moment targets opened the “secure” email link contained in the message, they were directed to an introductory page with the Proofpoint logo and login spoofs.
The analysts added:
Clicking on the Google and Office 365 buttons led to dedicated spoofed login flows for Google and Microsoft respectively. Both flows asked for the victim’s email address and password.
According to them, the email was sent through a hacked email account. The sender’s parent domain was “sdis34[.]fr,” which is a department of fire rescue in Southern France.
As explained, sending phishing emails from valid (but hacked) email accounts makes it easier to avoid binary detection control mechanisms such as filters or blocklists.
The phishing pages were hosted on the parent domain of a property firm.

Used Techniques
This email attack employed several techniques to circumvent traditional email security filters and pass the eye tests of unknowing users, including social engineering, brand impersonation, replicating existing workflows, and the use of compromised email addresses.
Proofpoint Guidance and Recommendations
Enhance native email security with additional controls.
Be on the lookout for social engineering indications.
Follow Multifactor authentication and password management best practices.
- Use multi-factor authentication (MFA) on both work and personal accounts.
- Avoid using the same password on multiple websites/accounts.
- Use password management software to save your account passwords.
- Avoid using passwords that contain public personal information such as (date of birth, anniversary date, etc.).
- Don’t use simple passwords such as ‘123456’, ‘
password123’, etc.
How Can Heimdal™ Help You?
HeimdalTM Security has developed two email security software aimed against both simple and sophisticated email threats (Heimdal™ Email Security, which detects and blocks malware, spam emails, malicious URLs, and phishing attacks and Heimdal™ Email Fraud Prevention, a revolutionary email protection system against employee impersonation, fraud attempts – and BEC, in general.
Heimdal® Email Security
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











