Contents:
According to a new report released by Google’s Threat Analysis Group (TAG) and Mandiant, Russia’s cyber attacks against Ukraine increased by 250% in 2022.
Following the country’s invasion of Ukraine in February 2022, the targeting focused heavily on the Ukrainian government, military entities, critical infrastructure, utilities, public services, and media.
The company said it observed more destructive cyber attacks in Ukraine in the first four months of 2022 than in the previous eight years, with attacks peaking around the beginning of the invasion.
Several unique wiper strains have been deployed against Ukrainian networks, including WhisperGate, HermeticWiper, IsaacWiper, CaddyWiper, Industroyer2, and SDelete.
PUSHCHA (also known as Ghostwriter or UNC1151), a Belarusian government-backed group aligned with Russia, was responsible for the spike in phishing attacks targeting NATO countries.
FROZENBARENTS (aka Sandworm or Voodoo Bear), FROZENLAKE (aka APT28 or Fancy Bear), COLDRIVER (aka Callisto Group), FROZEENVISTA (aka DEV-0586 or UNC2589), and SUMMIT (aka Turla or Venomous Bear) are some of the key actors involved in the effort.
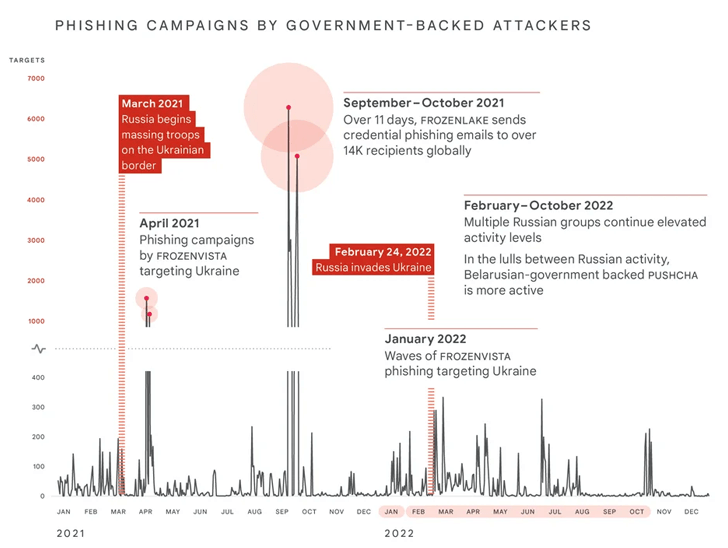
Aside from the uptick in the intensity and frequency of the operations, the invasion has also been accompanied by the Kremlin engaging in covert and overt information operations designed to shape public perception to undermine the Ukrainian government, fracturing international support for Ukraine, and maintaining domestic support for Russia.
The tech giant said GRU-sponsored actors used their access to steal sensitive information and release it to the public to further a narrative or conduct destructive cyber attacks or information operations.
Despite the war splintering hacking groups over political allegiances, and in some cases even causing them to close shop, this development further indicates a “notable shift in the Eastern European cybercriminal ecosystem” that blurs the lines between state-sponsored attackers and financially motivated actors.
An example is UAC-0098, which historically delivered the IcedID malware, repurposing its techniques to attack Ukraine as part of a ransomware campaign.
UAC-0098 members have been identified as former members of the now-defunct Conti cybercrime group. TrickBot has also been targeting Ukraine systematically since it was absorbed into Conti last year.
Besides Russia, Chinese government-backed attackers such as CURIOUS GORGE (aka UNC3742) and BASIN (aka Mustang Panda) are also shifting their focus to Ukrainian and Western European targets for intelligence gathering.
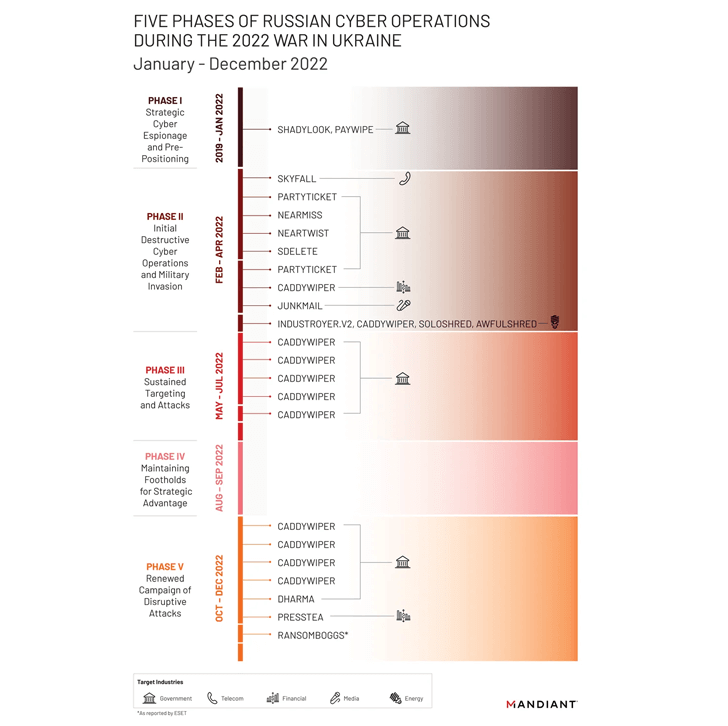
The disclosure comes as the Computer Emergency Response Team of Ukraine (CERT-UA) issued a warning about phishing emails posing as critical security updates but containing executables that lead to the deployment of remote desktop control software on infected systems.
The operation was attributed to a threat actor known as UAC-0096, previously detected using the same tactic in the weeks leading up to the war in late January 2022.
A year after launching its full-scale invasion of Ukraine, Russia remains unsuccessful in bringing Ukraine under its control as it struggles to overcome months of compounding strategic and tactical failures.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








