Contents:
Researchers in security are issuing warnings about threat actors misusing Google Cloud Run to spread large amounts of banking trojans, such as Astaroth, Mekotio, and Ousaban.
With Google Cloud Run, customers can manage workloads and launch front-end and back-end services, websites, and apps without having to worry about scaling or maintaining an infrastructure.
Reports from researchers show that Google Cloud Run has become attractive to cybercriminals lately due to its cost-effectiveness and ability to bypass standard security blocks and filters.
The Strategy Behind the Attack
The attack begins with phishing emails created to mimic legitimate communication for invoices, financial statements, or messages from governmental and tax agencies. Most of the emails in the campaign are in Spanish since the main targets are countries in Latin America, but there were also cases where the language used is Italian.
The emails contain links that redirect the victims to web services hosted on Google Cloud Run. MSI files are sometimes used to distribute payloads. In additional instances, the service sends a 302 redirect to a Google Cloud Storage site that houses a malicious MSI file in a ZIP archive.
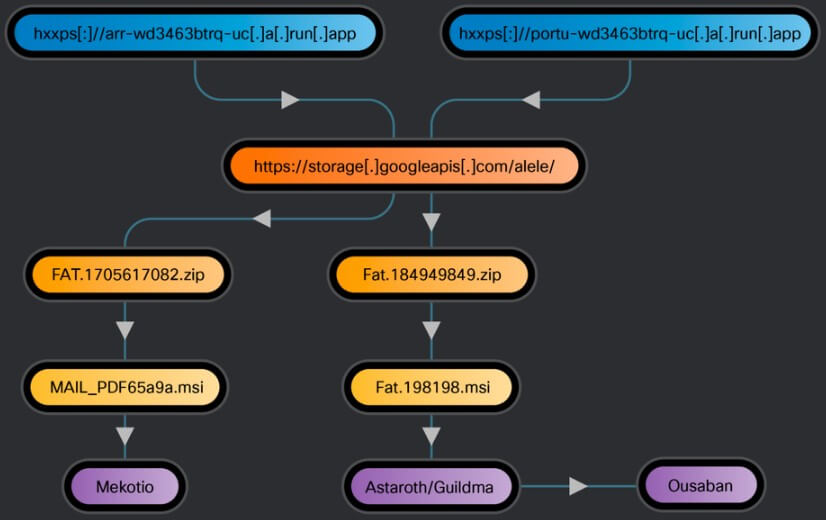
The Distribution Chain of the Malware (Source)
The system is updated with fresh payloads and components that are downloaded and run when the victim runs the malicious MSI files.
In the incidents that have been noticed, the legal Windows tool “BITSAdmin” is abused to deliver the payload in the second stage.
Lastly, the virus adds LNK files (‘sysupdates.setup.lnk’) to the Startup folder, configured to run a PowerShell command that runs the infection script (‘AutoIT’), thereby establishing persistence on the victim’s system to withstand reboots.
Details About the Malware Employed
Three banking trojans are used in the campaigns that misuse Google Cloud Run: Astaroth/Guildma, Mekotio, and Ousaban. Each is made with the intention of quietly entering systems, becoming persistent, and obtaining sensitive financial information that can be utilised to take control of bank accounts.
Astaroth has highly developed evasive skills. Originally concentrating on victims in Brazil, it currently targets more than 300 financial institutions in 15 Latin American nations. The ransomware has just begun gathering login information for cryptocurrency exchange platforms.
In addition to stealing confidential information, Astaroth uses keylogging, screen capture, and clipboard monitoring to intercept and modify internet traffic in order to obtain banking passwords.
Mekotio has also been in use for several years and focuses on the Latin American region. It has a reputation for carrying out fraudulent transactions and stealing personal information and financial credentials. Moreover, it has the ability to trick browsers into rerouting users to phishing websites.
Lastly, Ousaban is a trojan capable of keylogging and more. The malware is used in a later stage of the Astaroth infection chain, indicating a potential collaboration between the operators of the two malware families or a single threat actor managing both.
If you liked this piece, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










