Contents:
German companies and employees of German companies, in particular, are faced with a devious wave of ransomware attacks. While the new ransomware strain has been targeting mostly German victims so far, there’s no telling how far it may spread. We should all be aware of how the ransomware infects devices and how it works.
The GermanWiper ransomware earned its name not just because of the German focus of its intended targets, but also because it’s particularly devious. It doesn’t really encrypt data with a secret key, like other ransomware, awaiting payment in order to decrypt it.
With this one, there’s a nasty twist. The GermanWiper ransomware overwrites the data with strings of zeroes, rendering it completely unusable (wiped) forever. Nevertheless, it still acts like typical ransomware, falsely promising the victims that their files will be back if they pay a fee.
How Does the GermanWiper Ransomware Spread?
The victims of the GermanWiper ransomware typically receive a German-language email on behalf of a phony job applicant. The spam email pretends to be from a certain Lena Kretschmer, who is looking for a job and is sending the target a job application.
This is how the typical GermanWiper email looks like:
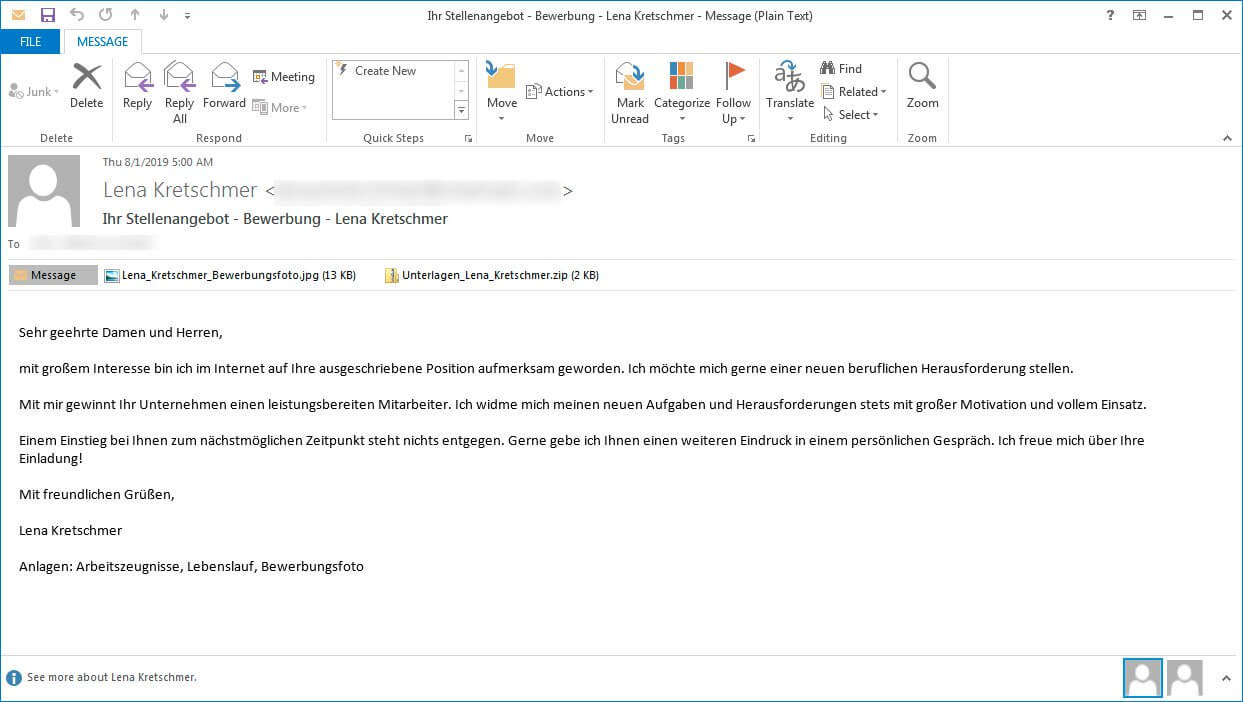
The common subject line of the email is “Ihr Stellenangebot – Bewerbung [Your job offer – Application] – Lena Kretschmer“. If the target opens it, they will notice that the email also contains an attachment named “Unterlagen_Lena_Kretschmer.zip”
If the victim makes the mistake of opening the zip archive, they will then get what looks like PDF files (with the correct file extension, .pdf). The files are actually link files (LNK) masquerading as PDF files, and once opened they will begin running malicious commands on the machine, infecting it.
When the LNK files are opened, they execute a PowerShell Command which downloads a malicious HTA file from xpandingdelegation[.]top site (domain sanitized for your safety). The HTA file then downloads the main ransomware executable. It all takes place in a matter of seconds. So, once you open those fake PDF files, there’s no turning back.
What Happens Once Infected with the GermanWiper Ransomware
There are two types of ransomware, usually: file lockers and computer (or device) lockers. The first (and more common) just lock your important data with a secret encryption key. The second type renders your device as a whole unusable until the ransom is paid.
GermanWiper is the type which only locks the files, so it’s less severe than the ones which block any use of your device. But unlike file lockers the world has seen so far, GermanWiper doesn’t lock anything. It only claims to have locked (encrypted) your files.
What it actually does is rewrite them with zeroes, such as in the screenshot below:
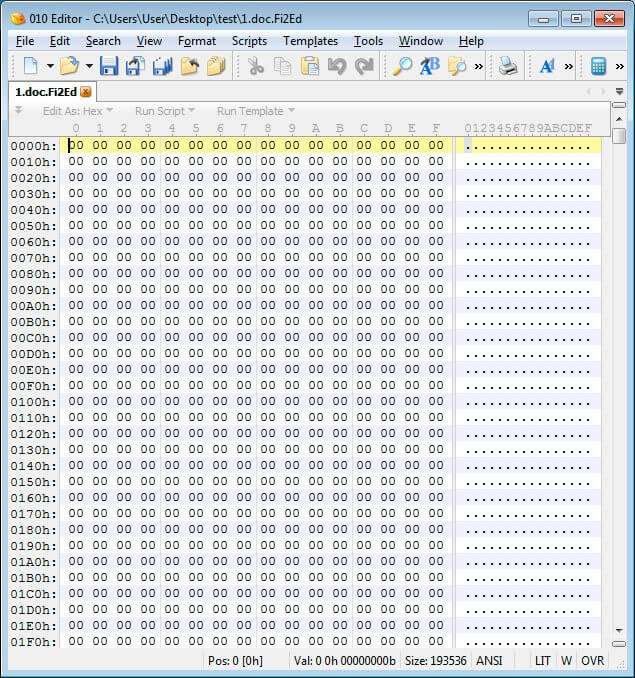
Image source: BleepingComputer.
If you were so inclined to pay the required ransom, there’s no doubt it would be for nothing. We haven’t heard from people who fell for the scam so far, but since the files are actually rewritten with zeros, it’s clear that there is nothing to recover.
If you are in this situation and find yourself infected with GermanWiper, there’s nothing to do. Just count your losses and have a better protection system in place next time. Company-wide cybersecurity awareness training is also a must.
What to Do If Infected with Ransomware
Even though there are plenty of free ransomware decryption tools which can help victims of ransomware, in many cases there is nothing to do but pay the attackers.
I personally wouldn’t recommend it because this keeps feeding the malware economy. Unless the data you lost is a matter of life-and-death, if you can’t decrypt it just let it go. Don’t repay the attackers for their unethical work.
Still, I won’t judge if you do decide to pay the ransom in order to get your data back. Unfortunately, as mentioned above, payment is not an option with the GermanWiper ransomware. This malicious creation will just delete your data from the start, so even if you send the ransom money, you can’t get it back. It’s just falling for a scam.
Of course, the best way to not get infected with ransomware (and other malware in general) is prevention. Adopt a proactive stance to your online security and you’ll be safe instead of sorry.
Against new strains of ransomware such as this one, Antivirus is not enough. You also need a DNS traffic filtering layer on top, which is able to detect even unknown malware. Our flagship product, Heimdal™ Threat Prevention Home, is an award-winning product exactly for this type of challenge. If you’d like to try it out, here’s one month on the house.

Be vigilant and don’t open attachments in emails, no matter how legit they seem. If you’re located in Germany and receive a work proposal email, be extra-extra cautious. It may be GermanWiper looking for its next victim.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










