Contents:
The ALPHV ransomware group, also known as BlackCat, has claimed responsibility for a cyberattack that disrupted numerous state courts in Northwest Florida, specifically within the First Judicial Circuit, last week.
Allegedly, the malicious actors were able to obtain sensitive personal information of employees and judges, including Social Security numbers and CVs. Moreover, ALPHV claims to have a detailed network map of the court’s systems, inclusive of credentials for both local and remote services.
Ransomware attackers, like ALPHV, typically threaten to disclose stolen data online as a strategy to force victims into negotiations or to reignite communication channels.
The appearance of a data leak page for Florida’s First Judicial Circuit on ALPHV’s website implies that negotiations have either not been initiated or the court has staunchly refused to comply with the gang’s demands.
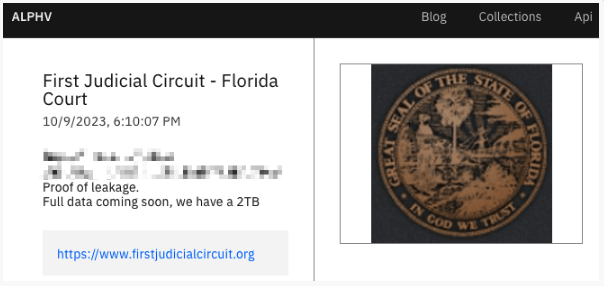
ALLPHV data leak page for Florida’s First Judicial Circuit (Source)
Timeline and Impact of the Breach
The Florida circuit court acknowledged the cyberattack last week, and confirmed that operations were significantly impacted since Monday morning, October 2nd.
This event will significantly affect court operations across the Circuit, impacting courts in Escambia, Okaloosa, Santa Rosa, and Walton counties, for an extended period.
The Circuit is prioritizing essential court proceedings but will cancel and reschedule other proceedings and pause related operations for several days, beginning Monday, October 2, 2023.
Statement from the Court’s Website (Source)
The Court didn’t confirm or deny ALPHV’s claims regarding the ransomware attack.
Background on ALPHV Ransomware Group
BlackCat/ALPHV, first emerging in November 2021, is presumed to be a rebranding of the notorious DarkSide/BlackMatter ransomware groups.
DarkSide became globally recognized after compromising the Colonial Pipeline, prompting investigations from worldwide law enforcement. They rebranded as BlackMatter in July 2021 but ceased operations in November 2021 following server seizures and the development of a decryption tool by security firm Emsisoft.
Characteristically, this ransomware group targets global enterprises, habitually evolving their tactics. In a recent notable attack, an affiliate named Scattered Spider took responsibility for compromising MGM Resorts, encrypting over 100 ESXi hypervisors and stealing customer data after the company refused ransom negotiation.
ALPHV’s attack on MGM Resorts resulted in approximately $100 million in losses and theft of customer data, Bleeping Computer explains.
The FBI had previously warned in April about the group’s involvement in successful breaches of over 60 entities worldwide from November 2021 to March 2022.
How Can Heimdal® Help?
In the fight against ransomware threats, Heimdal offers its clients a comprehensive cybersecurity suite, which features the Ransomware Encryption Protection module. Not only does this module block any unauthorized encryption attempts, but it also detects ransomware irrespective of its signature, whether they operate fileless or file-based.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Check out the linked articles to learn more about: how ransomware spreads, how to mitigate and how to prevent ransomware attacks.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








