Contents:
An EventBuilder misconfiguration led to sensitive data exposure, information belonging to registrants related to virtual events in the EventBuilder, the software platform that allows virtual events setting up such as conferences or webinars.
It is known that Microsoft uses this platform to be a host for external audiences related events, so it uses the Microsoft Teams extension.
Clario Tech, that worked together with Bob Diachenko, an independent security researcher in releasing a report that revealed the data leakage caused by the EventBuilder misconfiguration. Over one million registrants that used Microsoft Team for events had JSON and CSV documents containing private data exposed.
EventBuilder Data Exposure: What Data Was Disclosed?
The data leakage discovered by means of Grayhat Warfare’s engine showed that the following information was exposed:
- Full names
- E-mail addresses
- Names of the companies
- Position of registrants
- Phone numbers
- Survey feedback
An example of the leaked data includes the below “registrant’s summary” containing details about an event such as name, data, or participation status.
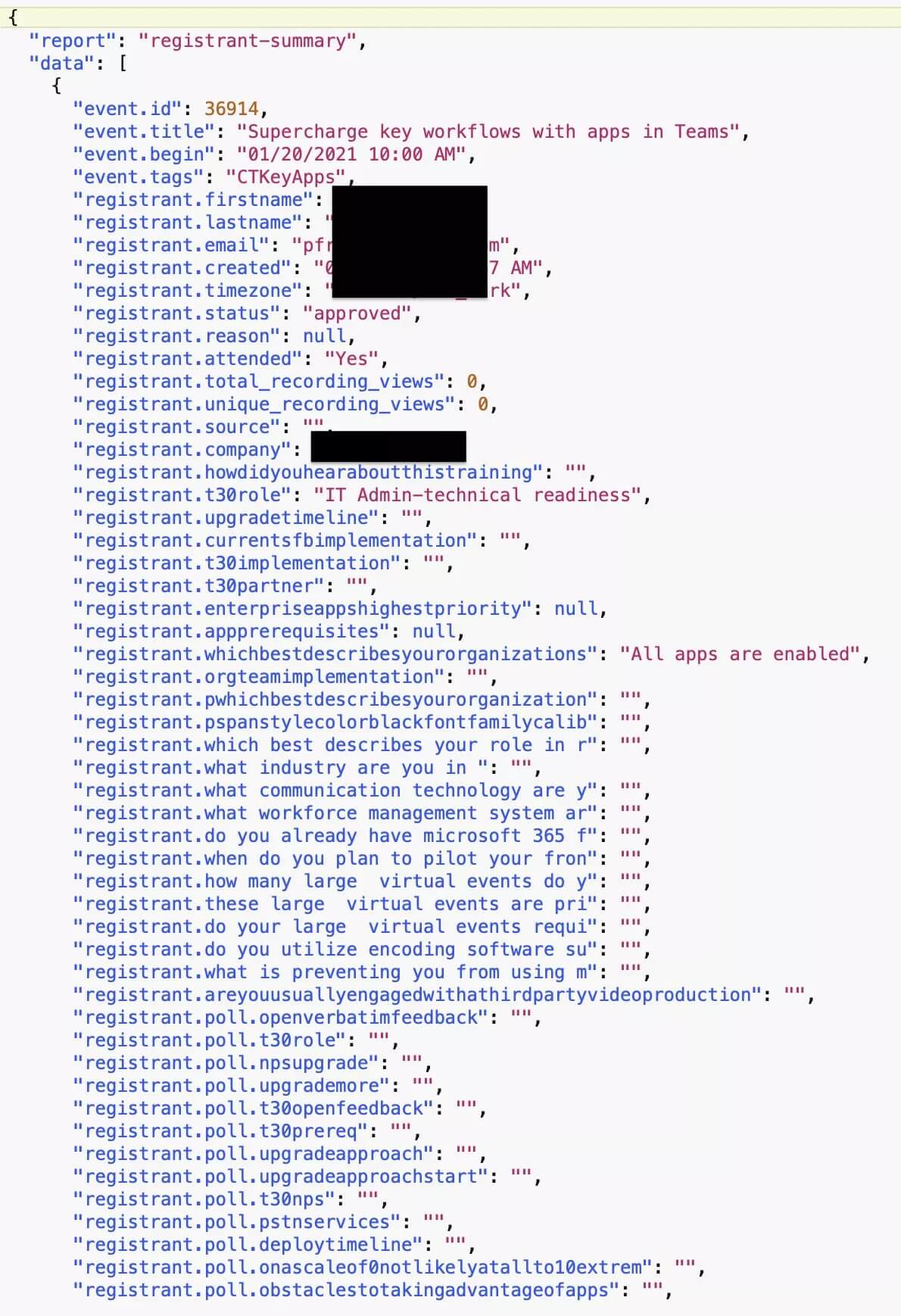
Another example, from the same report, it’s an excel file containing event-related information such as name, e-mail, phone, competition, prize id, prize title shared by Bob Diachenko with the BleepingComputer publication.
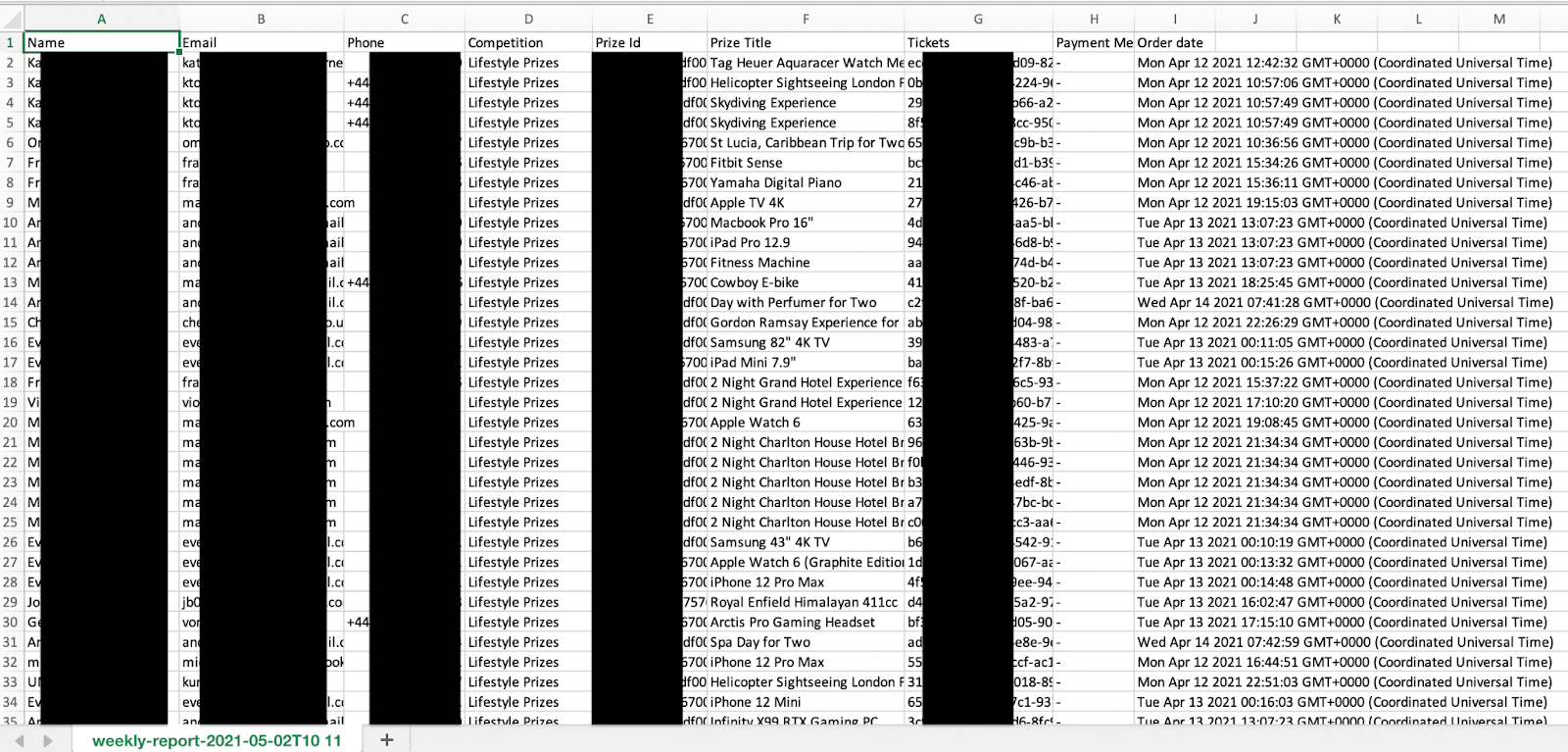
The discovery of the data exposure took place on the 10th of June, followed by contacting and informing EventBuilder about this. As Diachenko mentioned to the same publication, the company managed to solve the problem but did not come up with any comments regarding the EventBuilder data exposure.
It has not yet been determined how many records were exposed in total, but from the report, it’s understood that we are talking about large-sized files.
The data was stored on Microsoft Azure Blob Storage — Microsoft’s object storage solution for the Cloud. Blob storage is optimized for storing massive amounts of unstructured data (data that doesn’t adhere to a particular data model or definition, such as text or binary data). (…) The storage in question was supposed to be partially public, to host recorded sessions for link-only access. However, for some reason, the webinar organizers were putting registrant information into the blob. This meant it was open to indexing by a Public Bucket searcher (Grayhat Warfare), thus compromising their personal information and potentially putting them in danger of being targeted by hackers from across the globe.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








