Contents:
Although other malware families are still prevalent and dangerous, Emotet has climbed to the top of the list, with tens of thousands of malware campaigns occurring in recent months.
Security company Infobox observed over 60,000 malware campaigns distributing more than 13,000 file hashes.
“Emotet is a dangerous malware family that has evolved continually over the years: from a simple banking trojan to a botnet to an infrastructure for content delivery,” the company said.
What does this mean exactly? It means that now more than ever, it’s essential to be aware of malware so that you can protect your business. Emotet is once again wreaking havoc without restraint.
Emotet: A Walk Down Memory Lane
Emotet is a type of malware classified as a banking Trojan.
After being taken down by law enforcement back in January 2021, Emotet went offline for 11 months. In the meantime, threat actors developed improved detection evasion techniques, and now that it’s back on track, Emotet is potentially one of the most prevalent business threats.
This spring, cyber security companies noted that a more advanced self-propagating modular Trojan was back. For example, Check Point Research said that Emotet dominated its monthly top malware charts and impacted about 7% of organizations globally.
“Earlier this year, Emotet was targeting Japanese victims by hijacking email threads and then tricked victims into opening attachments with malicious embedded macros. One of the more troubling behaviors of this “new and improved” Emotet is its effectiveness in collecting and utilizing stolen credentials, which are then being weaponized to spread malware even further,” John Ayers, VP at Cyderes, told Cybernews.
Details on its Latest Attack
Emotet has been known to deliver emails as attachments to Microsoft Office files. In particular, they have relied on the use of Excel files.
The criminal organization has used the lure of shipping and invoice-related keywords in subject lines, often spoofing Amazon and DHL, which was how Emotet lured its victims. In addition, some malicious emails contained Ukraine-themed content, which made them appear as if they were recent events in the news, therefore increasing their clickability.
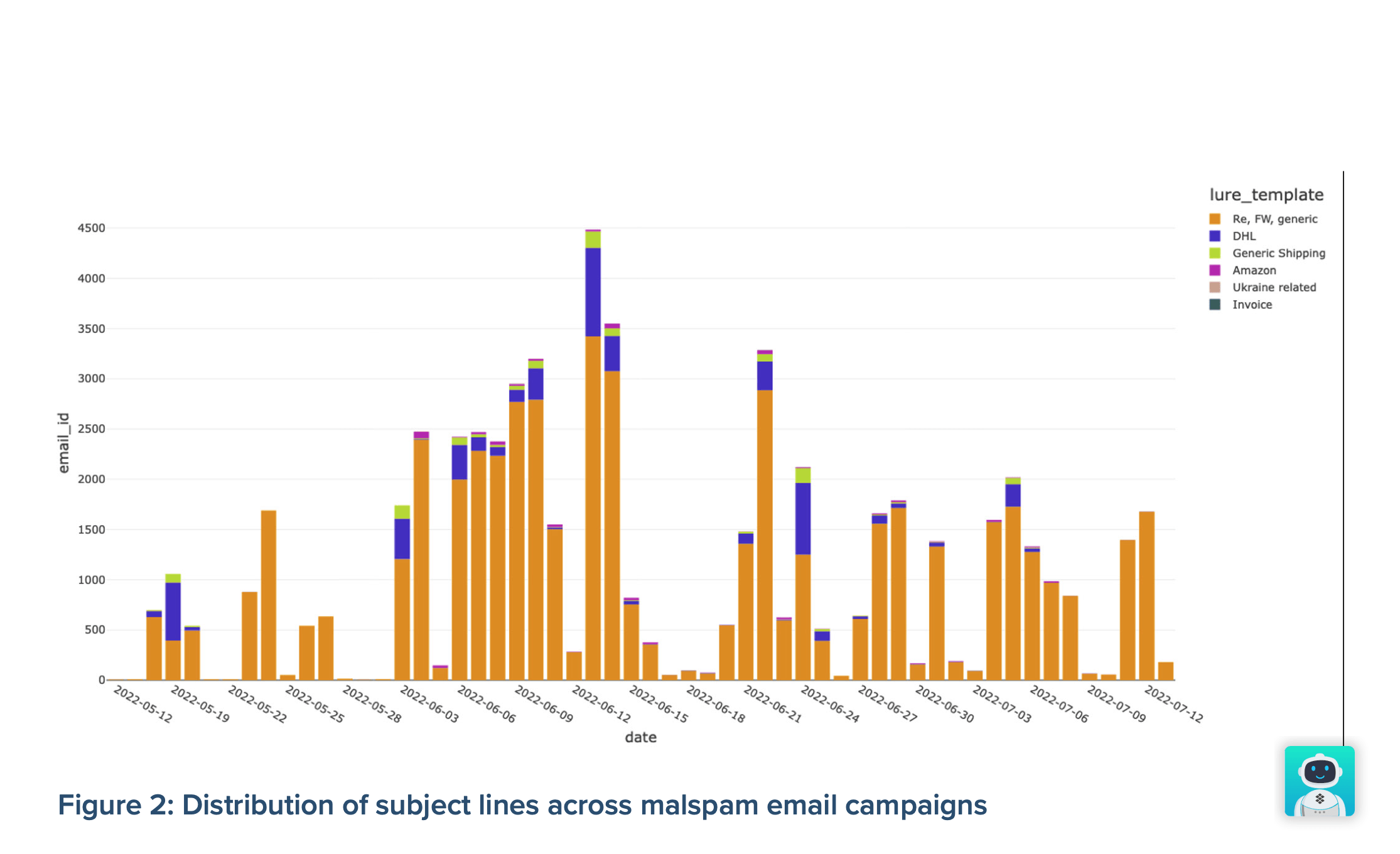
You might think these lures are exclusive to Emotet – that can’t be farther from the truth. Phishing emails that pretend to come from major brands and use hot topics to trick people into opening attachments are widespread these days.
These attachments often trigger malicious XLM macros, which initiate the Emotet infection chain. Almost always, zip archives are used as the attachment type because they’re easy to convince recipients to open.
However, Infoblox explains why attackers would use Microsoft Excel files: Corporate systems are sluggish and slow to update, so regardless of the vulnerability in a company’s software updates, the attacker can exploit it.
Infoblox’s analysis of Emotet’s command and control IPs indicated that the threat actor pays for the VPC service and uses virtual private cloud infrastructure.
According to the company, law enforcement agencies are less able to conduct takedowns since most providers used were telecommunications providers before the recent takedown.
To combat attacks, humans must ALWAYS be at the heart of any security process. These attacks exploit the human factor in the first instance, but if one does get through, we need our employees to be aware of spear phishing emails containing attachments or malicious links within the body of a message.
Mitigating risk is important, so here are the five things you can do right now:
- Since Emotet often hides in Microsoft Office files and needs macros to install malicious programs, it makes sense not to allow users to install them. In most business areas, macros are not required. If you still need them, you can only enable those that are signed.
- Regardless of what security updates get deployed and installed, they must immediately be applied to operating systems, anti-virus programs, and web browsers to keep your data secure.
- Backing up regular data is essential to keep safe in an emergency, and despite how common it is these days, 25% of people don’t back up regularly.
- Vigilance is the top priority: even when sending emails from trusted senders, you should watch out for any attached Office documents with attachments or links. As always, when in doubt, call the sender of a suspicious email to verify the legitimacy of their content before clicking anything.
- Corporate network access should also be monitored constantly so that individuals can find out about any Emotet infections early on, especially if you want to keep company information safe from cybercriminals.
Conclusion
Emotet malware has been designed to bypass traditional file-based antivirus detection, which can be challenging to eradicate.
However, it becomes possible with Heimdal™ Next-Gen Antivirus & MDM‘s four state-of-the-art malware detection layers and life process monitoring.
And when you add in Patch & Asset Management, you’re armed with a complete endpoint detection and response solution.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










