Contents:
Emotet is a malware known as a banking Trojan.
Malspam, which are spam emails that contain malware, is the primary means by which it spreads. To persuade consumers, these communications frequently feature recognizable branding, replicating the email structure of well-known and trustworthy firms such as PayPal or DHL.
Since 2015, Emotet started assaulting the United States. In 2017, there were over 50,000 infected PCs in one day alone. There have also been attacks in Europe and Asia, albeit not as high in numbers as in the United States.
What Happened?
Emotet malware is now being disseminated via malicious Windows App Installer packages that masquerade as Adobe PDF applications. The threat actors behind Emotet are now infecting PCs by installing malicious packages using App Installer, a built-in function of Windows 10 and Windows 11.
This approach has previously been utilized to disseminate the BazarLoader virus, which installed malicious packages stored on Microsoft Azure.
According to BleepingComputer, the assault path of the latest phishing email campaign is using URLs and email samples given by the Emotet tracking group Cryptolaemus.
This new Emotet campaign starts with an intercepted reply-chain email masquerading as a reply to an existing chat. These responses merely state, “Please see attached,” and include a link to a supposed PDF connected to the email chat.
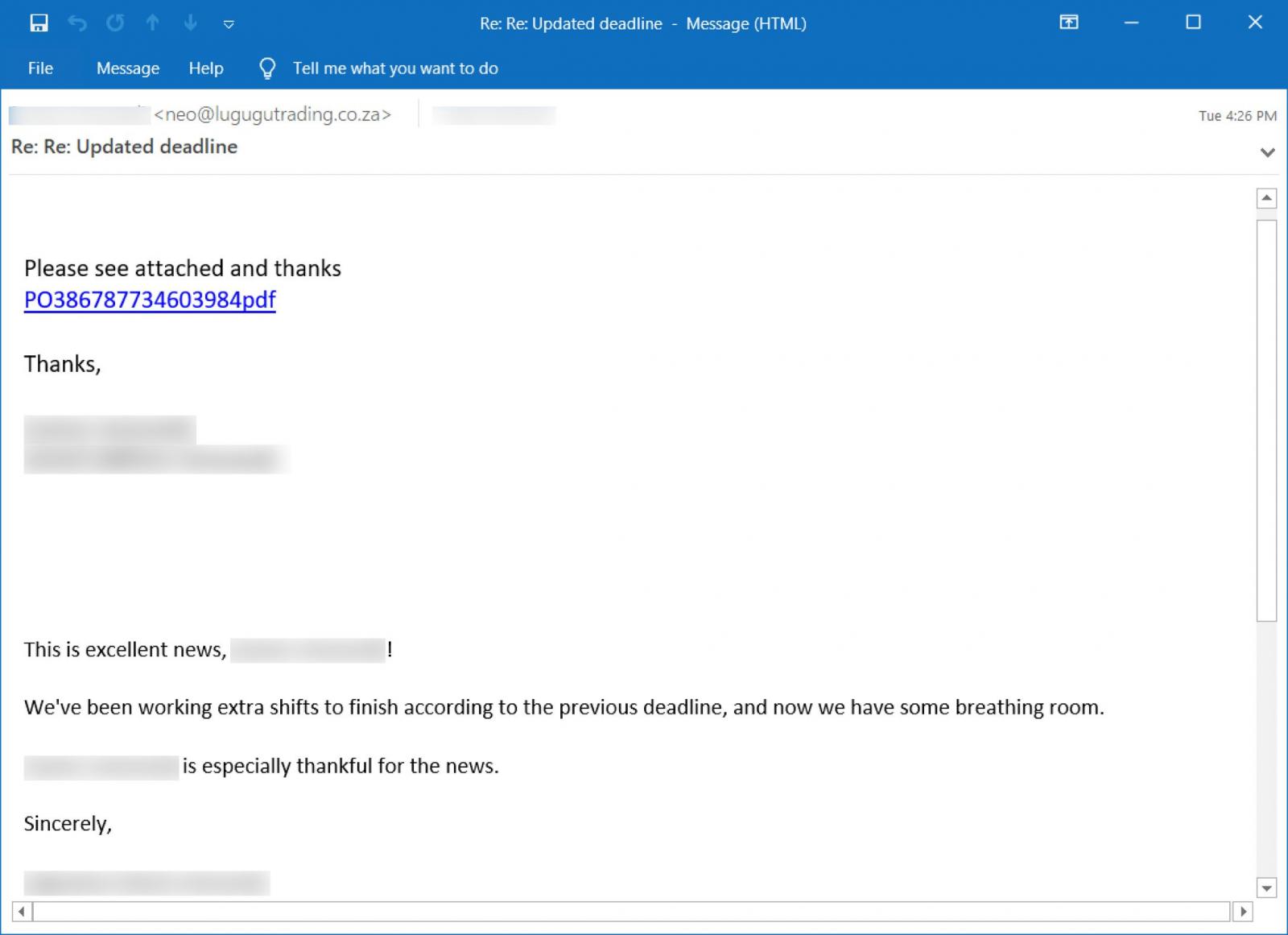
When the link is clicked, the user is sent to a bogus Google Drive website where they are prompted to click a button to preview the PDF document.
This ‘Preview PDF’ button is a ms-appinstaller URL that tries to open an appinstaller file housed on Microsoft Azure using URLs beginning with *.web.core.windows.net.
The preceding link, for example, would launch an appinstaller package at the following URL: ms-appinstaller:?source=https://xxx.z13.web.core.windows.net/abcdefghi.appinstaller.
An appinstaller file is nothing more than an XML file containing information about the signed publisher as well as the URL of the appbundle to be installed.
When you attempt to open an.appinstaller file, the Windows browser will prompt you to launch the Windows App Installer program.
When you approve, an App Installer window appears, asking you to install the ‘Adobe PDF Component.’
The malicious program seems to be a genuine Adobe application since it has a genuine Adobe PDF icon, a valid certificate claiming that it is a ‘Trusted App,’ and phony publisher information. This level of validation from Windows is more than enough for many users to trust and install the software.
The App Installer will download and install the malicious appxbundle hosted on Microsoft Azure after a user hits the ‘Install’ button. This appxbundle will place a DLL in the %Temp% folder and launch it using rundll32.exe.
This method will also copy the DLL as a randomly named file and folder in percent LocalAppData%, and an autorun will be established under HKCUSoftwareMicrosoftWindowsCurrentVersion.
Run to have the DLL run automatically when a user login into Windows. Emotet campaigns frequently result in ransomware attacks, therefore Windows administrators must be always informed on malware dissemination tactics.
How Can Heimdal™ Help?
In the fight against ransomware, Heimdal™ Security is offering its customers an outstanding integrated cybersecurity suite including the Ransomware Encryption Protection module, that is universally compatible with any antivirus solution, and is 100% signature-free, ensuring superior detection and remediation of any type of ransomware, whether fileless or file-based (including the most recent ones like LockFile).
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










