Contents:
Data Execution Prevention (DEP) is a Microsoft security technology and a crucial security feature for Windows operating systems that prevents malicious code from being executed from system memory locations. By using a set of hardware and software technologies, DEP performs additional checks in memory to help protect against exploits.
Malware may be executing malicious code from memory locations that only Windows or other accepted programs should use. If DEP detects that an application on your computer uses memory improperly, it will terminate the program and notify you.
How Data Execution Prevention Works
DEP isn’t like a firewall or antivirus program and therefore doesn’t help prevent harmful programs from being installed on your computer. What Data Execution Prevention does is to carefully monitor your programs to see if they’re using the system memory safely. For this, it marks specific memory locations as “non-executable”, and monitors programs that attempt to execute code from a protected location. Certain legacy applications, particularly 32-bit ones, may require specific adjustments to run code effectively on modern operating systems.
Let’s say that an application attempts to run malicious code from a protected page. In this case, the application will receive an exception with the status code STATUS_ACCESS_VIOLATION.
This can happen because your DEP settings are configured to start at system boot in line with the no-execute page protection policy setting within the boot configuration data. Depending on the policy setting, a particular application can change the DEP setting for its process.
By marking specific memory locations as “non-executable” and monitoring programs that are attempting to run malicious code from a protected location, DEP helps protect against various security threats.
DEP is enforced by hardware and by software:
Hardware-enforced DEP
Marks all memory locations during a process as non-executable unless the placement explicitly contains executable code, therefore helping prevent specific attacks by intercepting them and raising an exception.
Relying on processor hardware to mark memory with an attribute indicating that code shouldn’t be executed from that memory, it functions by changing a bit within the page table entry to create a mark on the particular memory page.
The actual hardware implementation of Data Execution Prevention and marking of the virtual memory page varies by processor architecture, but processors that support hardware-enforced DEP are capable of raising an exception when code is executed from a page marked with the suitable attribute set.
Software-enforced DEP
Windows has added an extra set of data execution prevention security checks, also called software-enforced DEP, designed to mitigate exploits of exception handling mechanisms in Windows. Software-enforced DEP can run on any processor capable of running Windows XP SP2 and above.
Should You Disable Data Execution Prevention?
DEP automatically monitors essential Windows programs and services, so you shouldn’t turn it off. However, there are scenarios where you might need to disable DEP, such as compatibility issues with older 32-bit applications.
You can increase your protection by having DEP monitor all programs. Therefore, you should remember that disabling Data Execution Prevention or adding exclusions may allow malicious scripts to execute and cause severe damage to Windows which can leave your PC permanently unstable and/or unusable state.
If you switch off Data Execution Prevention for a particular program, it will become vulnerable to attacks. A successful attack could then spread to other programs on your computer, to your contacts, and will damage your files.
If you notice that a program doesn’t run correctly when DEP is on, check the current DEP status and look for a DEP-compatible version or update from the software publisher before you modify any Data Execution Prevention settings.
How To Configure Data Execution Prevention in Advanced System Settings
DEP settings are enabled by default for essential Windows operating system programs and services.
You must be logged on as an administrator or a member of the Administrators group to complete this procedure. If your computer is connected to a network, network policy settings may also prevent you from completing this procedure.
1. Open the Control Panel.
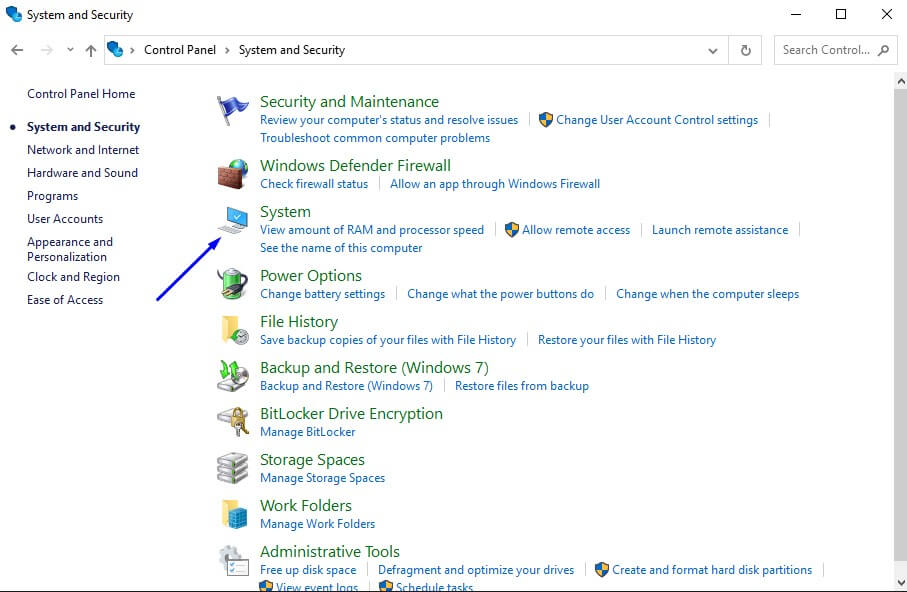
2. Click System and Security > System > Advanced System Settings.
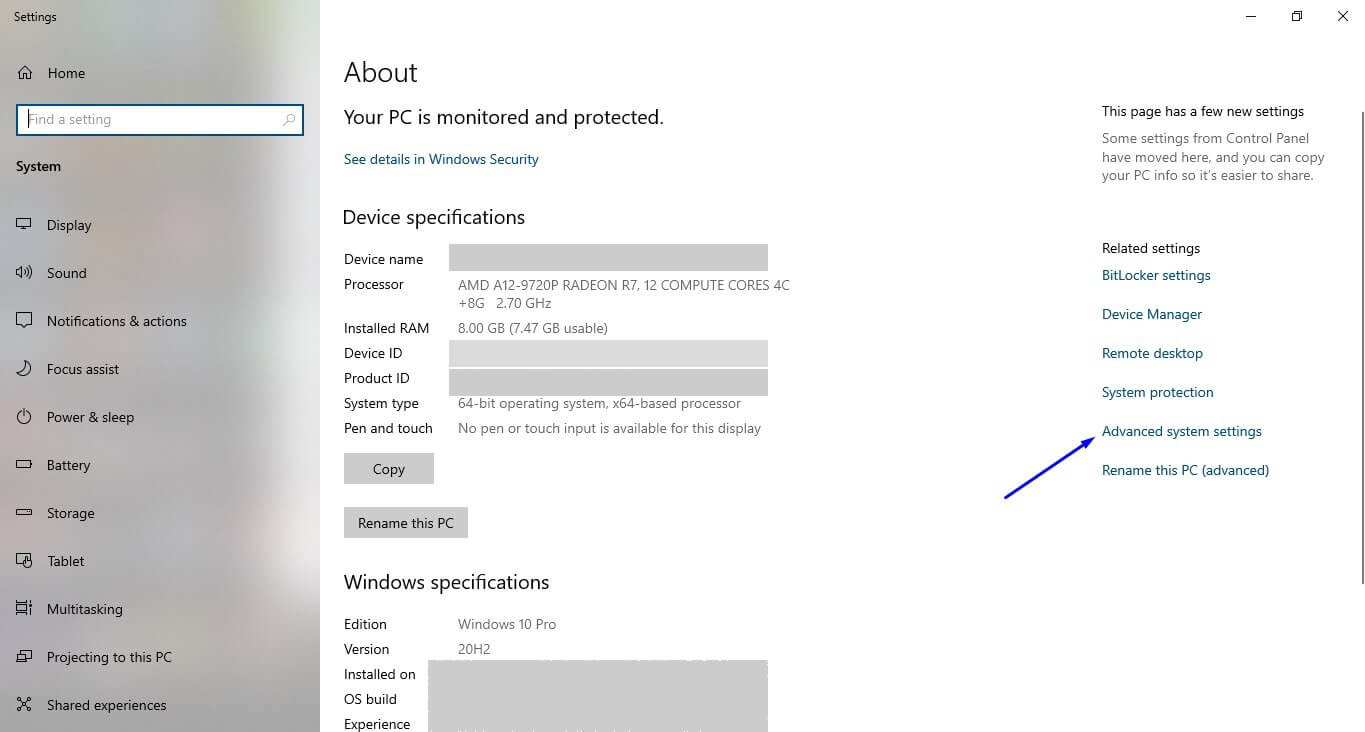
3. Once you are on the Advanced tab click Settings.
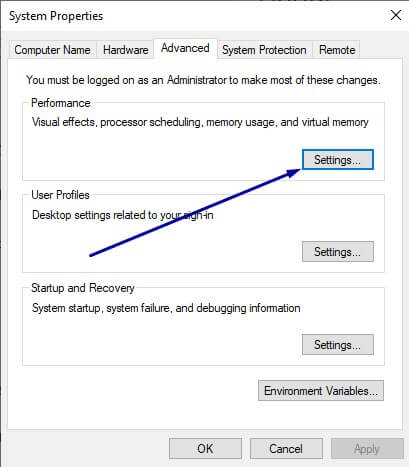
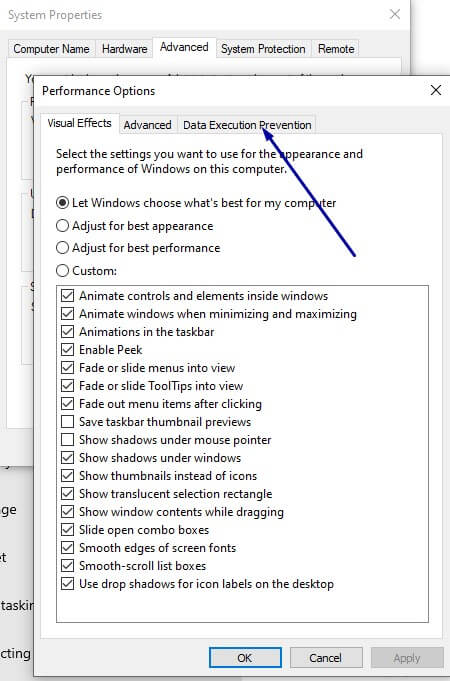
4. Click the Data Execution Prevention tab.
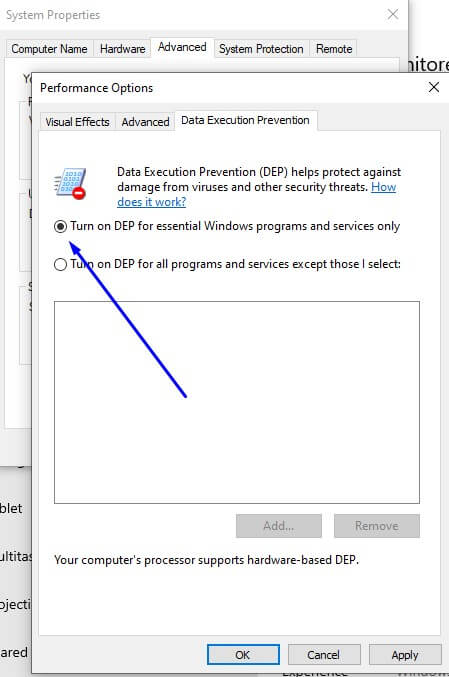
5. Select Turn on DEP for essential Windows programs and services only.
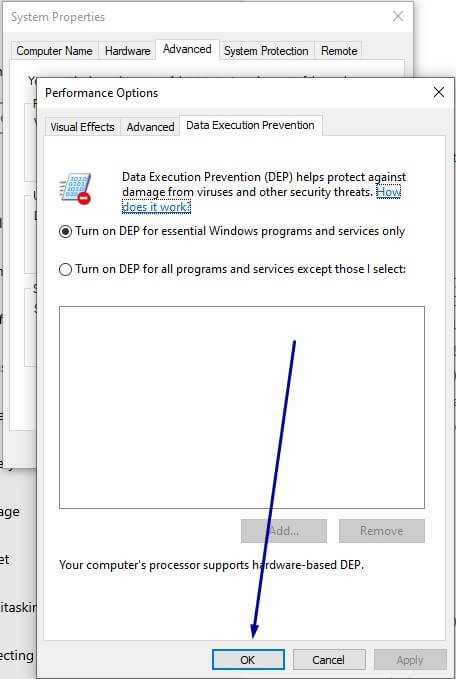
6. Click OK. Make sure to restart your system in order to enable the change.
How to check from CMD if DEP is enabled
1. Open CMD ().
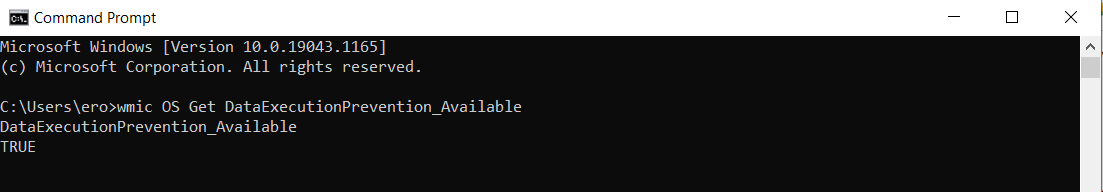
2. Type the following command, then press ENTER:
wmic OS Get DataExecutionPrevention_Available
If the output is “TRUE,” hardware-enforced DEP is available.
Wrapping Up
Data execution prevention is one of the foremost basic protections a Windows-based system can have, and unless necessary, it must always remain active. DEP helps protect against viruses and other security threats that could exploit system weaknesses.
If you’re using programs that are developed to be used on a 64-bit OS, most are created with DEP in mind and will be fine. You can adjust DEP settings through the performance section in the advanced system settings. However, if you use legacy code, you’ll need to create an exception for that specific program.
In any case, you should handle Data Execution Prevention with caution. Keep it as default unless there’s a valid reason to alter it. While DEP is vital, it’s just one aspect of infosec when discussing about Windows 10.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











