Contents:
A new phishing campaign disguised as package notification is on the rampage. Initially discovered in Denmark, the malicious venture notifies users that they are expecting a package delivery.
The phishing attempt came to light when a Denmark cell user received the following SMS:
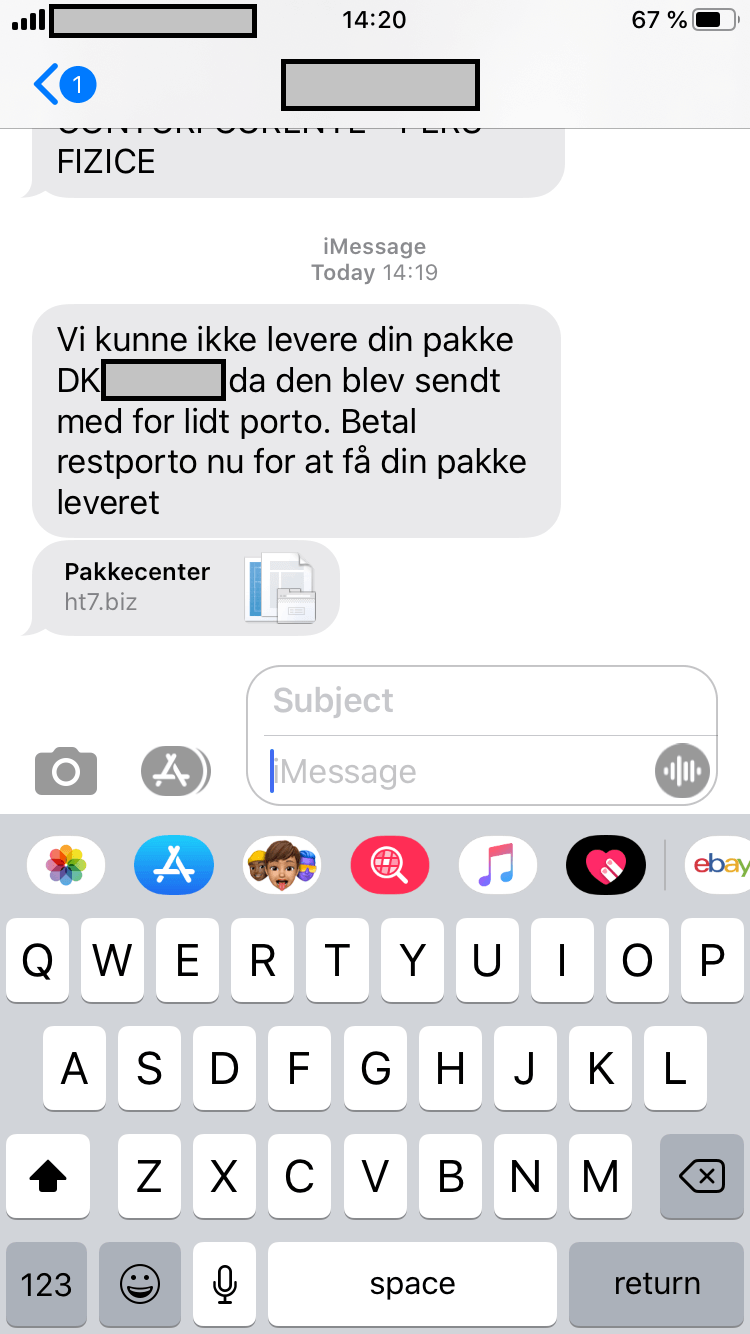
The message reads: “We were unable to deliver your package DK-XXXXXX as it had been shipped with too little postage. Pay the shipping fee now to have your package delivered.” Right beneath the message, is a link called ht7.biz (domain sanitized by Heimdal Security) that presumably redirects the user to the package center.
However, right before the browser lands on the package center’s search page, it’s being routed via another domain, called ai6.net (domain sanitized and blocked by Heimdal Security), before calling pakketinfo.paketexclusivo.com website.
The link takes the user to a package search page (see the picture below)
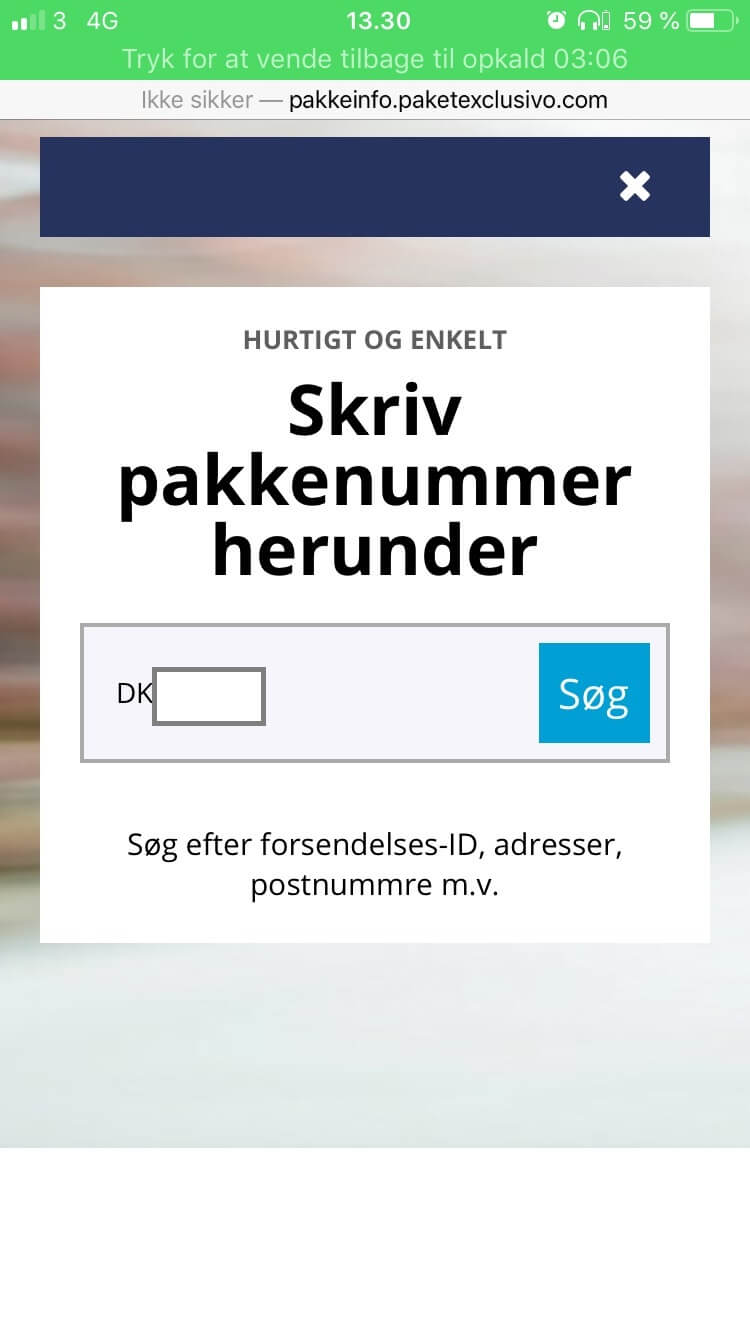
At this point, the user is required to search for the package’s number. The text above reads: “Quick and easy. Write your parcel number below. Search after shipping ID, address, postcode, etc.” Once the user writes down the parcel number flagged down in the SMS and presses the “Search” button, he will be redirected to the following screen:
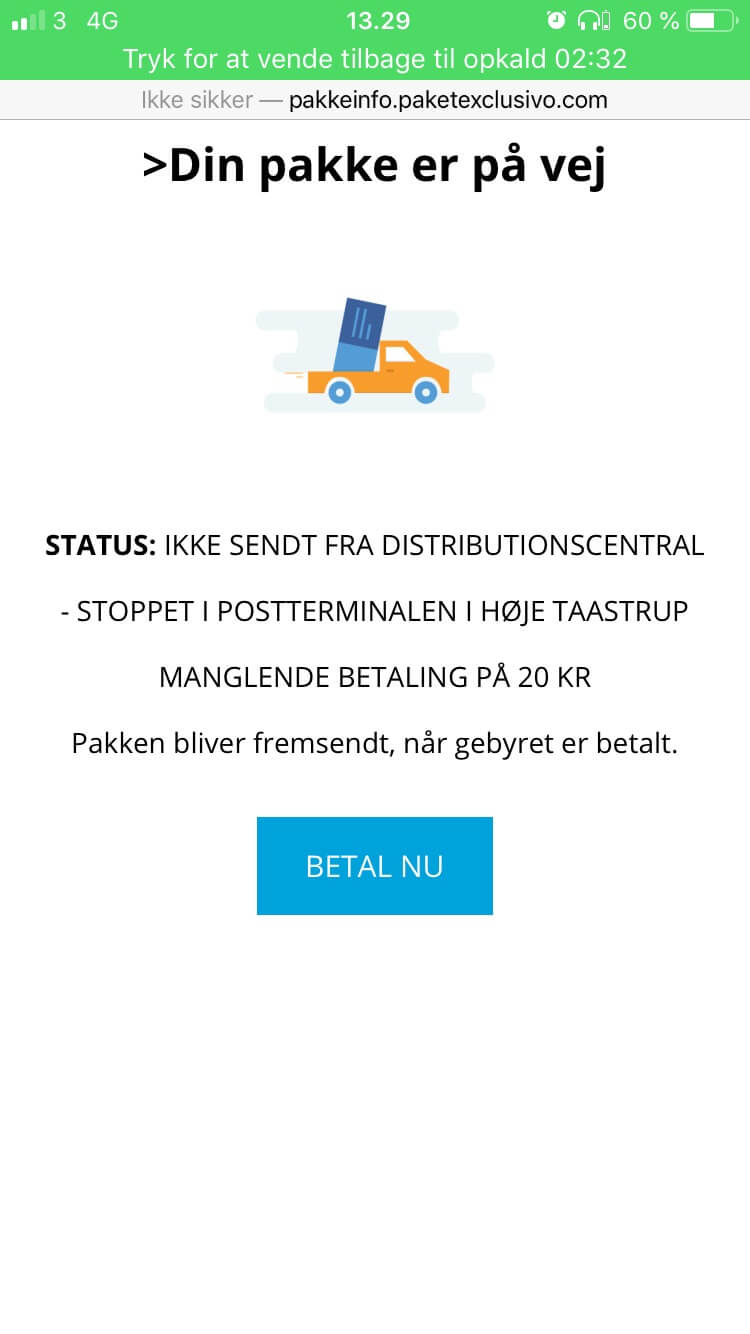
The message reads: “Your package is on its way. Status: not sent from the Distribution Center – stopped in X post office, failing payment of 20 Danish crowns ($3). The package will be shipped when the fee is paid.” Motivated to pay the remaining postage fees, the user will press the “BETAL NU” (Pay now) button. Once again, the browser redirects the user to another website – dk.price-live.com (domain sanitized and blocked by Heimdal Security).
The DK appendage is just a bounce. Price Live, the root domain, which is listed under a United States IP, is not under CloudFlare’s protection and, therefore more visible in the wild. The root domain has also been sanitized and blocked by Heimdal Security.
Price Live’s payment processing page was specifically engineered to mimic a legitimate page. Notice in the picture below the credentials included to reinforce the illusion: Norton secured badge, SSL encryption certificate, PCI compliance, Verified by Visa, and MasterCard SecureCode and supported payment methods such as Visa, Visa Electron, MasterCard, Maestro.

Private info fields have also been added. To send the order through, which in this case is the additional postage fee, the user must fill in his first and last name, physical address, ZIP Code, city of residence, mobile number, and email address.
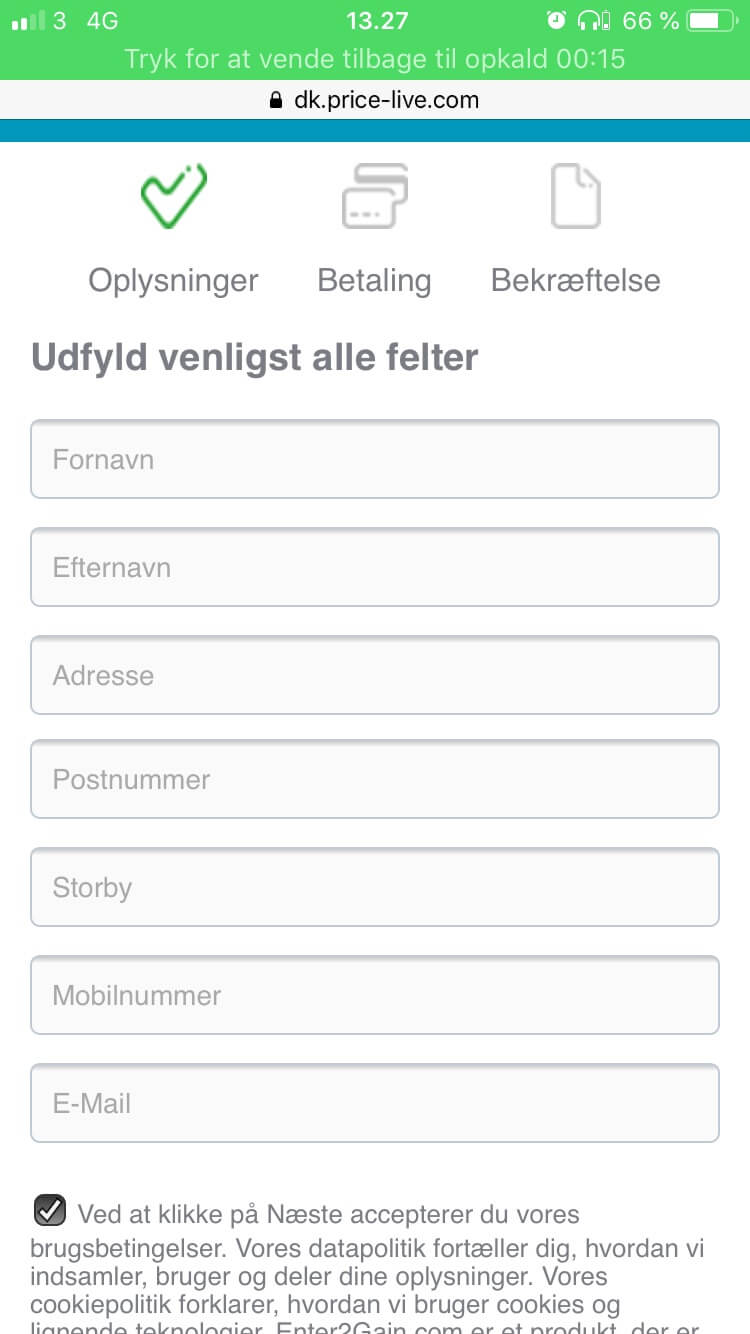
The mimicry is very difficult to detect at first glance. However, the message at the bottom of the page, which so conveniently is accompanied by a checked box, tells another story. The message reads:
By clicking Next, you will automatically agree to our Terms of Use. Our data policy tells you how we collect, use, and share your information. Subsequently, our cookie policy explains how we use cookies and similar technologies. Enter2Gain.com is a product based on an automatic subscription of 39.99 euros and AUTOMATIC RENEWED at the end of the three-day trial period unless it expires before the beginning of the three-day trial period when it will be canceled.
In essence, the phishing campaign works like this: having received an SMS on the phone, the user clicks on the appended link to verify the status of the package. A brief search reveals that the delivery has been denied on account of insufficient postage. The user is then redirected to another website where he can post the due fee. There are 2 foreseeable outcomes:
1) The user fills out the fields, leaves the box checked.
The data goes directly to the malicious actor who engineered the page. Twenty Danish crowns will be deducted from the bank account. Financial data will also be exposed. The user will also be subscribed to the product. At the end of the three-day trial period, 39.99 euros will be deducted from the bank account. Auto-renewal will kick in every three days, posting similar payouts. There’s no visible way of canceling the subscription.
2) The user fills out the field, unchecks the box.
Personal data gets stolen. Twenty Danish crowns will be deducted from the account. Financial info will be exposed. Enter2Gain subscription will not be possible.
Forensic Analysis of end domain
Domain forensics reveal that Price Live was created on the 10th of December 2019 in the UK, under TUCOWS, INC. Tucows Domains Inc. It has two CloudFlare name servers, both of them calling out approximately 21 million domains. IP address analysis points to Fasthosts Internet Limited as being the ISP. The subsequent IP change history reveals that there have been 10 changes on 10 unique addresses during the last 5 years. Registrar’s current status: client transfer and update have both been prohibited. Furthermore, the registrant has been listed as REDACTED FOR PRIVACY.
How to stay safe from the new Nordic phishing campaign
1. Refrain from clicking on any links enclosed in SMSs/emails
The most common phishing method is to include ‘spiked’ links inside an SMS or email. This will redirect you to a fake form. Contents are transmitted to a malicious actor instead of a legitimate data processing unit. Bear in mind that vendors will not ask you to fill in passwords, email addresses, names, or financial details via email.
2. Get in touch with your parcel shipping company
If by chance, you do come across a message informing you that your order cannot be delivered due to one reason or another, the best way of figuring out its legitimacy is to get in touch with your shipping company. Request details about the ETA, any due fees, and any hang-ups. Most shipping companies enclose the courier’s cell number. Give him or her a call and inquire about the status. If your parcel’s due to arrive via the postmaster service, head to the nearest office and make inquiries. Don’t forget to bring along any paperwork or data regarding your delivery.
3. Anti-phishing protection
Against phishing attempts, an antivirus isn’t enough to ensure complete protection. Most requests are hijacked at the DNS level, something a traditional antivirus can’t pick up. Heimdal™ Threat Prevention Home, our flagship threat prevention system, can filter out traffic at the DNS level and root out any phishing attempts. In addition, it can sever the connection to malicious command & control servers, rendering them useless.

Wrap-up
The latest phishing campaign proves that malicious actors have resorted to twisted guerilla marketing techniques in order to maximize the damage and increase efficiency. Be on your guard, refrain from clicking on suspicious links, get confirmation from your shipping agency, and use an adequate antimalware solution.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







