Contents:
Cybersecurity researchers unveiled a new malvertising campaign that uses malicious Google ads to deliver a backdoor dubbed ‘MadMxShell’. The ads leverage a set of domains to push the backdoor and mimic legitimate IP scanner software.
The 45 domains, registered between November 2023 and March 2024 pose as IP scanner software such as:
- Angry IP Scanner
- Advanced IP Scanner
- IP Scanner PRTG
- ManageEngine
The malicious campaign was identified by researchers at Zscaler ThreatLabz.
How Is the Attack Carried Out?
Although this isn’t the first time that threat actors have used malvertising to spread malware through fake websites, this is the first time that the method has been used to spread a complex Windows backdoor, explains Bleeping Computer.
To gain access, attackers lure people who search for these kinds of tools to visit fake websites with JavaScript code that, when clicked, download a file called “Advanced-ip-scanner.zip.”
The ZIP package contains a DLL file (“IVIEWERS.dll”) and an executable (“Advanced-ip-scanner.exe”), the latter of which employs DLL side-loading to load the DLL and initiate the infection sequence.
The DLL file injects the encoded shellcode into the “Advanced-ip-scanner.exe” process via a method known as process hollowing, and the injected EXE file then unpacks two more files: OneDrive.exe and Secur32.dll.
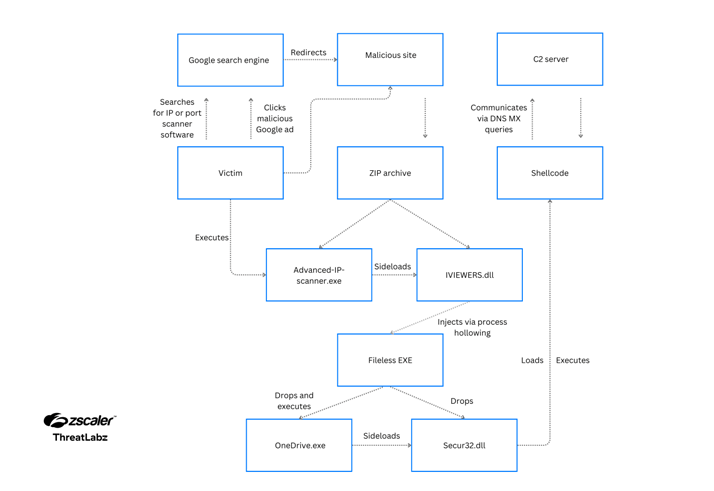
Zscaler Report Source
Then, the attackers exploit the legitimate signed Microsoft binary, OneDrive.exe, to sideload Secur32.dll and execute the shellcode backdoor, setting up persistence in the system through a scheduled task and disabling Microsoft Defender Antivirus to avoid detection.
Named for its method of utilizing DNS MX queries for command and control (C2), the backdoor is engineered to collect system information, execute commands through cmd.exe, and manage basic file operations like read, write, and delete.
The malware communicates with its C2 server (“litterbolo[.]com”) by embedding data within the subdomains of the Fully Qualified Domain Name (FQDN) during a DNS DNS mail exchange (MX) query, receiving encoded commands in return.
The backdoor uses techniques such as multiple stages of DLL side-loading and DNS tunneling for command-and-control (C2) communication as a means to evade endpoint and network security solutions, respectively.
In addition, the backdoor uses evasive techniques like anti-dumping to prevent memory analysis and hinder forensics security solutions.
Zscaler Report Source
Origins
The origins and motives of the malware operators remain unclear. However, Zscaler has identified two accounts linked to the perpetrators on criminal forums like blackhatworld[.]com and social-eng[.]ru, using an email wh8842480@gmail[.]com also associated with a spoofed domain for Advanced IP Scanner.
These accounts have been active since at least June 2023, suggesting plans for a sustained malvertising effort.
The researchers note that these forums often discuss strategies for exploiting Google Ads threshold accounts to conduct extensive ad campaigns without immediate payment, indicating a method to sustain their malicious activities over long periods.
The full report is available here.
How to prevent Malvertising?
Malvertising will not go away anytime soon, so businesses and individual users must understand how to spot and prevent it. Measures include:
- Use a DNS filtering solution to prevent communication with malicious domains;
- Use next generation antivirus software to prevent malware from downloading automatically;
- Turn on click-to-play in your browsers.
- Use adblockers to block all advertisements.
- Avoid using Flash and Java due to vulnerabilities that can lead to malvertisement attacks;
- Update browsers and plugins on a regular basis – if you’re a business, you can use an automated patching solution to simplify the process;
- Identify advertisements that appear illegitimate.
- Search for a company without clicking on an advertisement.
- Stay current on the newest malvertising campaigns.
Read more about how to create a successful cybersecurity strategy here.

Heimdal® DNS Security Solution
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
And if you liked this piece, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








