Contents:
One thing is certain in today’s cybersecurity landscape, managing cyber risk across enterprises is harder than it used to be previously, but why? It started with the explosion of cloud-based services and contact with third parties, which increase organizations’ overall cybersecurity risk. Additionally, the pandemic situation caused practices such as work-from-home, and BYOD to surge, contributing even more to the speed at which an already fast-changing landscape shifts.
What Is Cybersecurity Risk Management?
Cybersecurity risk management is a strategic process to approach the prioritization of threats. Organizations implement cybersecurity risk management to ensure that they can respond to threats in a timely manner. The strategy identifies potential risks, assesses their impact, prioritizes, and plans on how to respond to threats based on their potential impact on the business.
Risk management strategies recognize that a company cannot completely eliminate all system flaws or prevent all online threats. Developing a cybersecurity risk management strategy aids firms in being the first to respond to the most serious vulnerabilities, threat patterns, and assaults.
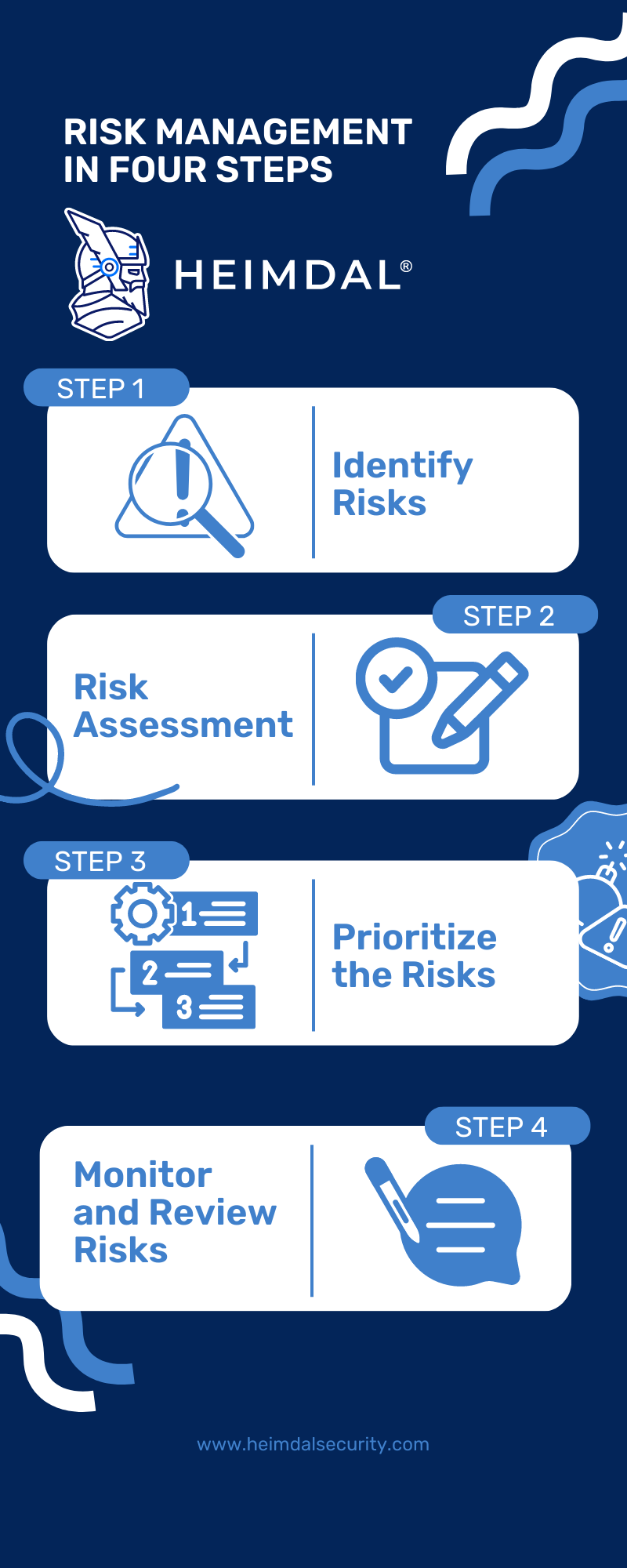
The Risk Management Process
The risk management process can be done by following four steps:
- Identify the Risks: Evaluate the environment of your organization to identify current or potential risks that could have an effect on your business;
- Assess the Risks: After identifying what are the risks of your organization, it’s time to analyze how likely are they to impact your organization’s business and what effects could a potential fruition of the risk could have on your operations. For more information on how to conduct a cybersecurity risk assessment, you can check out this article;
- Prioritize the Risks: Based on the threats they pose to the security of your business and the likeliness to encounter them, prioritize the risk and take measures to stop them;
- Constantly Monitor Risks and Review Strategies: Risks are regularly monitored, and a clear risk response strategy is in place. Evaluate constantly how effective your controls are at mitigating the respective risks and adjust them accordingly.
Cybersecurity Risk Management Frameworks
There are various frameworks for managing cybersecurity risks, and each one offers guidelines that organizations can use to pinpoint and reduce risks.
Organizations can assess, monitor, and define security policies and procedures to address threats with the aid of a cyber risk management framework. Here are a few popular frameworks for managing cyber risk:
NIST Risk Management Framework
The system development life cycle can be integrated with security, privacy, and cyber supply chain risk management tasks using the NIST Risk Management Framework. The RFM approach can be used in any sort of company, regardless of size or industry, with any form of system or technology (such as IoT, and control systems), both new and legacy.
DoD Risk Management Framework
The Risk Management Framework (RMF) for the Department of Defense (DoD) outlines the standards that DoD entities must follow when evaluating and managing cybersecurity threats. The six main steps in the RMF breakdown of the cyber risk management plan are categorization, chosen, implementation, assessment, authorization, and monitoring.
ENISA Risk Management/Risk Assessment Framework
The Risk Management/Risk Assessment (RM/RA) Framework developed by ENISA provides a critical review of pertinent information about Europe’s cyber threat landscape that may be found in related literature.
ISO
For the management of cybersecurity risk, the International Organization for Standardization (ISO) offers several frameworks. ISO/ISE 27000, which contains more than a dozen standards for identifying and addressing cybersecurity threats, is the first and most important.
How Can Heimdal® Help Your Business?
Keeping threat actors at bay is essential for the activity of any business. Attacks can have a massive impact on organizations, cause data breaches, and even completely halt some activities. Unpatched software is one of the leading causes of many types of cyberattacks.
Heimdal’s Patch & Asset Management solution is a complete, automated, and customizable software that can help you be one step ahead of attackers. The solution can inventory both hardware and software assets, and patch them accordingly. Patches, updates, and hotfixes from exclusive, outside, and OS-specific sources are supported by this solution.

Heimdal® Patch & Asset Management Software
- Schedule updates at your convenience;
- See any software assets in inventory;
- Global deployment and LAN P2P;
- And much more than we can fit in here...
Conclusion
With the current, ever-changing landscape, implementing a cybersecurity risk management process is one essential step for keeping your company safe and sound from threat actors. Keep in mind that although not all threats can be prevented, at least we can expect them and act in a controlled, more efficient manner.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










