Contents:
With the start of this new school year, students are returning to classrooms for the first time in months. However, it is more than clear that the Coronavirus pandemic refuses to die down (for now), which means that remote learning is still very much on the table in 2020-2021. While some schools are attempting a fulltime return to their teaching spaces, others are adopting a hybrid model that will see students come to class on certain days and learn from home on others. In terms of cybersecurity, this poses new issues for institutions and students alike. In the following lines, I will first and foremost discuss how the educational sector is affected by cyberattacks. Then, I aim to provide both educational staff and their students with the information they need to handle these matters more proactively in the school year to come.
Cyberattacks in the Educational Sector: An Overview
The K-12 Cybersecurity Resource Center has been monitoring cyberattacks that target American schools, kindergarten through 12th grade, since January 2016. At the moment of my writing of this article, 958 incidents of this sort have been registered. To put the situation into perspective even more, the total rose by 6 over the weekend. What is more, the total number of operations aimed at K-12 schools alone tripled in 2019. When we take universities into account as well, the statistics are even more desolate. In 2019, several high-profile universities in Europe and the United States alike fell prey to vicious malware and ransomware strains like Emotet or Netwalker. The Columbia College of Chicago and the Humboldt University of Berlin are just a few of the affected institutions of this kind. With schools moving towards remote learning in 2020 due to the Coronavirus pandemic, the situation got even worse. As per an article published by BleepingComputer, the U.K. National Cyber Security Centre (NCSC) issued an alert in September of the same year warning that ransomware threats targeting educational facilities were on the rise. What goes on behind these online threats? Why are our schools and universities so vulnerable online? In the sections below, I will talk about the most prevalent types of cyberattacks schools are faced with, as well as their palpable consequences and the reasons why hackers target such institutions.
Prevalent Types of Cyberattacks on Schools
For our readers with experience in the educational sector, it might come as no surprise that unauthorized disclosure breaches are the most widely encountered type of cyberattack plaguing the world’s schools. More often than not, hackers are after your data and money, and do you know which institutions have plenty of that on record? If you shouted ‘schools’ at the screen, you were spot on. Nonetheless, attackers have a few more threats under their malicious tool belt, and they’re always waiting for an opportunity to throw them at our schools. According to the K-12 Cybersecurity Resource Center’s 2019 Year in Review, the number for the previous year go as follows:
- 60.06% consisted of data breaches,
- 17.82% consisted of ransomware attacks,
- 8.05% consisted of phishing campaigns,
- and 1.15% consisted of denial of service,
- while other incidents made up 12.93%.
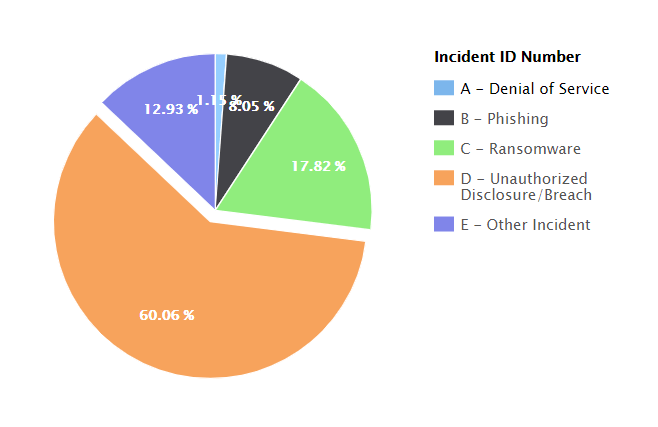
Image Source: The K-12 Cybersecurity Research Center
This differed slightly from the statistics gathered by the center in its 2018 Year in Review, when:
- 46,72% consisted of data breaches,
- 15.57% consisted of phishing campaigns,
- 9.84% consisted of denial of service,
- and 9.02% consisted of ransomware attacks,
- while other incidents made up 18.85%.
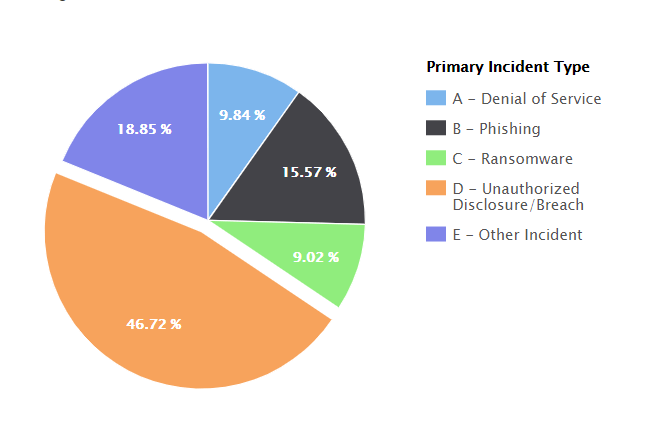
Image Source: The K-12 Cybersecurity Research Center
As you can conclude from the statistics above, data breaches held the majority in 2018 and 2019 alike. However, the notable difference stands in the fact that ransomware attacks surpassed phishing in frequency in 2019, outlining a trend in the industry.
Common Effects of Cyberattacks on Schools
The social and financial damages a cyberattack can inflict on an educational institution can be quite extensive if the threat is not mitigated on time. Here are a few significant ways in which a hacking operation can affect such an establishment:
- corruption of school property,
- misuse of credentials,
- student record theft,
- interruption of operations,
- and financial extortion.
Why Do Cybercriminals Target Schools?
As per Microsoft’s Security Intelligence Report displaying monthly data, around 60% of malware attacks were directed towards the educational sector, making it by far the most affected field. For reference, second place is held by business and professional services, with a mere 10%. Let that sink in for a while. So, what makes schools such attractive targets for hackers? Well, a few things. In terms of gains, there are three main reasons why malicious groups pursue educational facilities:
- Financial benefits, which remain the main driving force behind more than 70% of the world’s total cyberattacks, according to Verizon’s yearly Data Breach Investigations Report.
- Personally-identifiable information (PII), which abounds in the databases of schools and universities and comes from a variety of sources (students, alumni, or staff).
- Confidential research data, which contains secret martial or governmental information that both state-affiliated and independent malicious actors want to get their hands on. For example, in 2019 Chinese hackers attacked several high-profile universities in the US looking for classified maritime military research.
As for the main reasons for which school networks are so accessible to cybercrime operations, here are a few notable ones:
- Lack of cybereducation. While it is expected of companies to train their employees in terms of online safety, this is impractical for schools that see hundreds of new students each year.
- Improper on-site protection. Large campuses make it especially easy for ill-intentioned strangers to infiltrate, then hack the perimeter or plant infected devices.
- Precarious cybersecurity. In SecurityScorecard’s 2018 Education Cybersecurity Report, the educational sector ranked the lowest among all other industries that were analyzed.
Essential Institution-Level Cybersecurity Priorities
Whether you want your students to return to class five days a week or are a fan of the hybrid model, you should always remember that having a proper cybersecurity policy is essential in these times. Below, I will discuss five concrete priorities in this field you should set for your institution in 2020-2021.
Threat Awareness Training
As previously mentioned, security awareness is not too prevalent in schools and universities around the globe. Most educational facilities do not consider this field one worth investing time, money, and other resources in. However, the state of the current online landscape says they should. Kim Griffin, the technical director for Mississippi’s Clinton Public School District performed an experiment in March of 2020 after noticing an alarming increase in phishing-related incidents. Together with her team, she set up a fake Gmail account riddled with red flags such as spelling errors. From it, they sent out emails that contained a link to a survey that required login with Google credentials. What they found indicated a clear lack of cyber education among staff in the educational sector. Out of a total of 572 fake phishing emails that were sent out, 474 were opened by recipients. The most concerning part is yet to come, as 272 members of staff clicked the link in the email and 113 provided their login credentials. As a bonus, 45 people disclosed personal information on a public Google sheet. Unfortunately, while Kim Griffin’s awareness campaign was a faux-threat, actual security breaches occurred over the years due to poorly trained staff and naïve students. For this reason, investing in cybersecurity seminars for staff and students alike should be an essential priority for your institution. Something as simple as teaching people to identify a fake Gmail account can prevent a large-scale malware attack that can have dire consequences in the long run.
Privileged Access Management
Hackers commonly employ the escalation of network privileges to reach multiple machines within the same organization. This is why insider threats are more dangerous than ever, and also why you should always practice the principle of least privilege (POLP) among personnel. This won’t allow them more resources than strictly necessary to perform their daily duties. Of course, you should apply POLP to the student body as well, especially now that remote learning is more widespread than ever. While the risk of this is lower in K-12 education, it is higher in the case of universities (for obvious reasons). To prevent hacking attempts among undergraduates, you should also enforce network segmentation. This prevents lateral and horizontal privilege escalation. For a more holistic approach to privileged access management, I recommend our very own Heimdal™ Privileged Access Management. Being the only PAM solution on the market that also de-escalates privileges upon threat detection or infection, it will ensure that this matter is properly mitigated within any institution. Heimdal® Privileged Access
Management
Remote Account Security
While essential staff members are returning to their posts, students also re-enter classrooms for the first time since this spring. Nevertheless, this doesn’t mean that you should neglect remote access security matters in the school year to come. Remote learning will probably remain a big part of the educational landscape in 2021, especially since everyone must still be sent home within minutes of the first COVID-19 case. For this reason, securing the remote access points to the school network is essential. Fortunately, this can easily be achieved through a Virtual Private Network (VPN). This will offer users a safe passage to the documents that they need to access, and it will encrypt the information they share in the system as well.
Multiple Layers of Cybersecurity
Phishing emails containing malware are just one of the many threats a school can face online. As shown by the data I presented at the beginning of this article, data breaches, ransomware infections, and DNS-level attacks are just the most widely encountered concerns you should have in this field. For this reason, having multiple layers of cybersecurity within your organization is essential, which is where we here at Heimdal come in to help. Combining the next-generation antivirus properties of Heimdal™ Next-Gen Antivirus & MDM and the advanced threat prevention features offered by Heimdal™ Threat Prevention, our EDR Software can cover all bases for your school’s needs. Its inbuilt firewall protects against potential brute force attacks, while local and real-time cloud scanning detects any malicious visitors to your network. Moreover, its proprietary DarkLayer Guard technology prevents both data leaks and ransomware attacks by filtering threats at the DNS and HTTP levels. Finally, its Heimdal™ Patch & Asset Management will deploy software updates automatically, which can help your school with proper patch management as well.
Detection and Response Plan
Finally, when worst comes to worst against all precautions, knowing when and how to respond is crucial. This is why outlining a Doomsday Plan for the school will make a difference between a small crisis and an enormous catastrophe. Does your institution have one? If not, here are a few things you should consider doing proactively as part of it:
- backup essential data offline,
- monitor network traffic,
- and activate two-factor authentication.
As for what you can do reactively, consider the following:
- shut down the network,
- identify the infection point,
- reset infected machines,
- change passwords,
- and notify the authorities.
Having an immediate response is essential for the proper mitigation of any cyberattack. As little as a couple of minutes can completely change the outcome of the situation.
How to Mitigate Remote Learning Risks at Home
Not an educator? Students (and their parents) also play a crucial role in the mitigation of the cybersecurity risks associated with remote learning. Here is how you can play your part in strengthening your school’s online safety with five easy-to-follow steps.
1. Learn How to Recognize Malicious URLs
Although phishing has decreased in popularity over the years, hackers still love themselves a bit of malspam. For this reason, every student should be able to recognize a malicious link or a malware attachment in an email. While it is true that hackers are becoming more and more refined in their spam campaigns, more often than not corrupt URLs will have at least one giveaway. A different domain (dotnet instead of dotcom, for example) is the first sign of bad news. Other, less perceptible clues are slight variations in spelling, as well as extra or missing hyphens.
2. Never Disclose Any Personal Information
If you ever receive an email asking you to reveal personal or financial information, move it straight to the Trash folder. Organizations seldom ask for such data over the Internet. You most likely already know this if you’ve reached college age, but younger students might be easier prey to this ruse. To verify the legitimacy of a request sent over email, you can always contact the institution or company that sent it. This will drag the process (if any) on for a little while more, but your information security should be a higher priority in this day and age.
3. Activate Your Webcam Sparingly (or Not at All)
Did you know that your computer’s camera might be your biggest vulnerability during the pandemic? As more and more of us are moving our daily activities (i.e. school) to Zoom or other video streaming platforms, attackers are not indifferent. In fact, over 15,000 webcams worldwide are exposed to hackers to exploit. And those are just the ones that don’t require too much hard work to crack. For this reason, I always recommend turning your webcam on only when it’s absolutely mandatory. But even so, you might be targeted, as skilled cybercriminals can still access it remotely. When in doubt, covering it is the best option. Even Mark Zuckerberg does it, and he tapes over his microphone too. Take a page out of the richest millennial’s book on this one, even if your friends laugh and call you paranoid.
4. Always Keep Your Software Up to Date
Updates are deployed to fix flaws in design and patch software vulnerabilities. Constantly postponing them opens gateways for malware, ransomware, and other malicious operations that can steal your data and inflict financial damage as well. Therefore, you should always install updates on all your Internet-connected devices (laptop, smartphone, tablet) as soon as they are sent out by the developers. This doesn’t have to be a disruptive affair either, as you can easily schedule them outside of school hours.
5. Install an Antivirus Optimized for Home Use
The final and arguably most effective step to achieve at-home cybersecurity is to install antivirus software if you don’t have one already. Fortunately, this doesn’t have to be a costly affair, as there are quite a few free ones available online. For example, our Heimdal Free automatically updates vulnerable applications, a necessity in this day and age (that I’ve covered at point 4). Still, if you want to be completely safe out there and close all potential gateways, you will need more than a basic piece of software. As cyber-threats are becoming increasingly robust, so should your home security. My recommendation here is Heimdal™ Premium Security Home, an all-in-one suite of cybersecurity tools that combines the functionalities of Heimdal Next-Gen Antivirus Home and Heimdal Threat Prevention Home. Try out for 30 days (on us) and see how you like it.
To Sum It Up…
This new school year will see the world’s youth learning from school and home alike, which comes with its own set of challenges. Nevertheless, having the proper training and tools on hand will greatly enhance your online safety regardless of the location. In 2020-2021, protecting essential institutional data will fall into the hands of students and staff alike.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











