Contents:
Notorious North Korean hacking group, Lazarus, breached Taiwanese multimedia software company CyberLink and trojanized an installer to instead push malware in a complex supply chain attack, with the possibility of a worldwide reach.
Activity that may have been connected to the modified CyberLink installer file first appeared as early as October 20, 2023, according to Microsoft Threat Intelligence.
What We Know About the Attack
This trojanized installer has been found on over 100 devices globally, including those in Japan, Taiwan, Canada, and the United States. It was hosted on authentic CyberLink update infrastructure.
Microsoft identified the source of this supply chain attack as Lazarus (also known as Diamon Sleet), a North Korean cyberespionage group that security researchers have been tracking.
While looking into this attack, it was discovered that the second-stage payload interacted with infrastructure that the same set of threat actors had already penetrated.
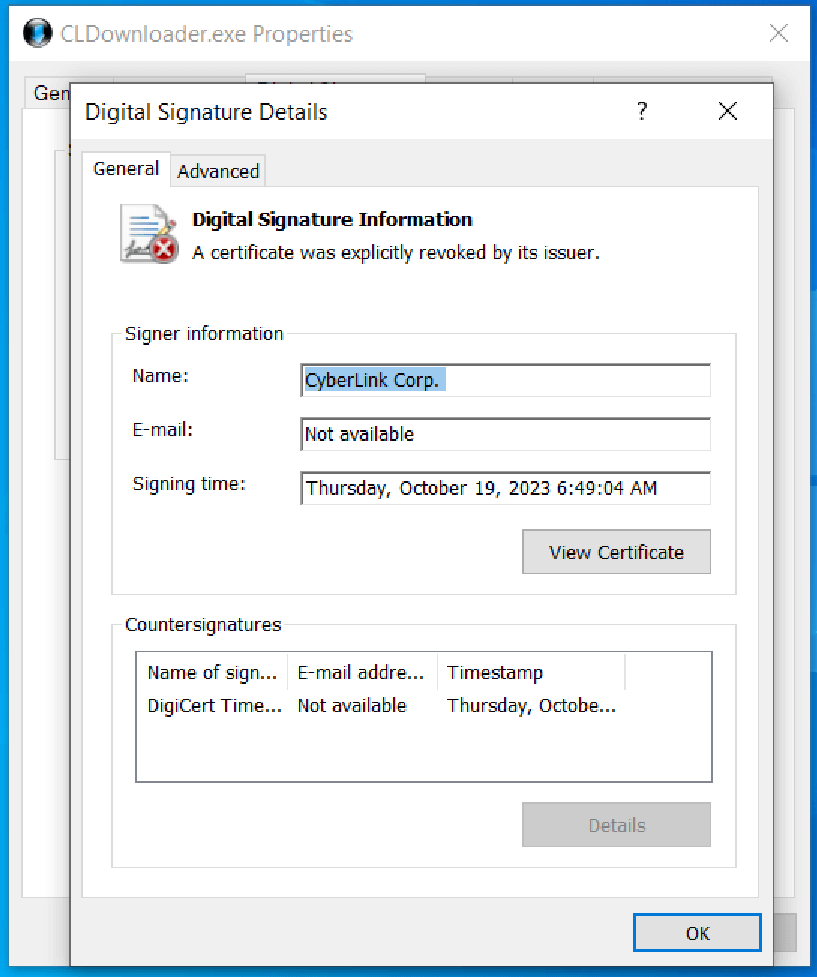
Diamond Sleet utilized a legitimate code signing certificate issued to CyberLink Corp. to sign the malicious executable.
Microsoft (Source)
Trojanized CyberLink Installer (Source)
Microsoft tracks the trojanized software and other related payloads as LambLoad, which is a malware downloader and loader.
If the right conditions are met, the malware will connect with one of three command-and-control (C2) servers to retrieve a second-stage payload concealed within a file posing as a PNG file, using the static User-Agent ‘Microsoft Internet Explorer’.
Microsoft says that the PNG file contains an embedded payload inside a fake outer PNG header that is, carved, decrypted, and launched in memory.
The Lazarus North Korean threat actors, who are renowned for exploiting reputable bitcoin software to steal cryptocurrency assets, frequently employ this assault technique.
Despite Microsoft’s inability to identify keyboard action with hands after LambLoad virus breaches, the Lazarus hackers are well-known for:
- Stealing private information from hacked computers;
- Breaking into software development environments;
- Moving downstream in order to take advantage of more victims;
- Gaining ongoing access to the surroundings of the victims.
Microsoft notified CyberLink and Microsoft Defender for Endpoint customers impacted by the supply chain attack after discovering it.
In accordance with its Acceptable Use Policies, GitHub removed the second-stage payload after Microsoft also reported the attack to them.
Since 1996, CyberLink, a company that produces software for playing and editing multimedia, claims to have shipped 400 million copies of its products worldwide.
If you liked this piece, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










