Contents:
There has been a surge in cyber-attacks against cloud service providers (CSPs) and managed service providers (MSPs). Resecurity recently alerted several data center organizations about a malicious cyber campaign targeting both the organizations and their clients.
Threat actors orchestrated all of these attacks in order to gain unauthorized access to sensitive information belonging to government organizations and businesses by exploiting vulnerabilities in the cybersecurity supply chain.
Customers and Data Impacted
As an essential component of most enterprises’ supply chains, data centers are a substantial target for attackers.
A number of large data center customers have been affected by this breach, according to Resecurity‘s cybersecurity analysts, including the following:
- Alibaba Group Holding
- Amazon
- Goldman Sachs Group
- Walmart
The data related to the following has been mainly targeted and stolen from the data centers:
- Customer service
- Ticket management
- Support portals
- Remote management services
- Datacenter employee
- Customer email account credentials
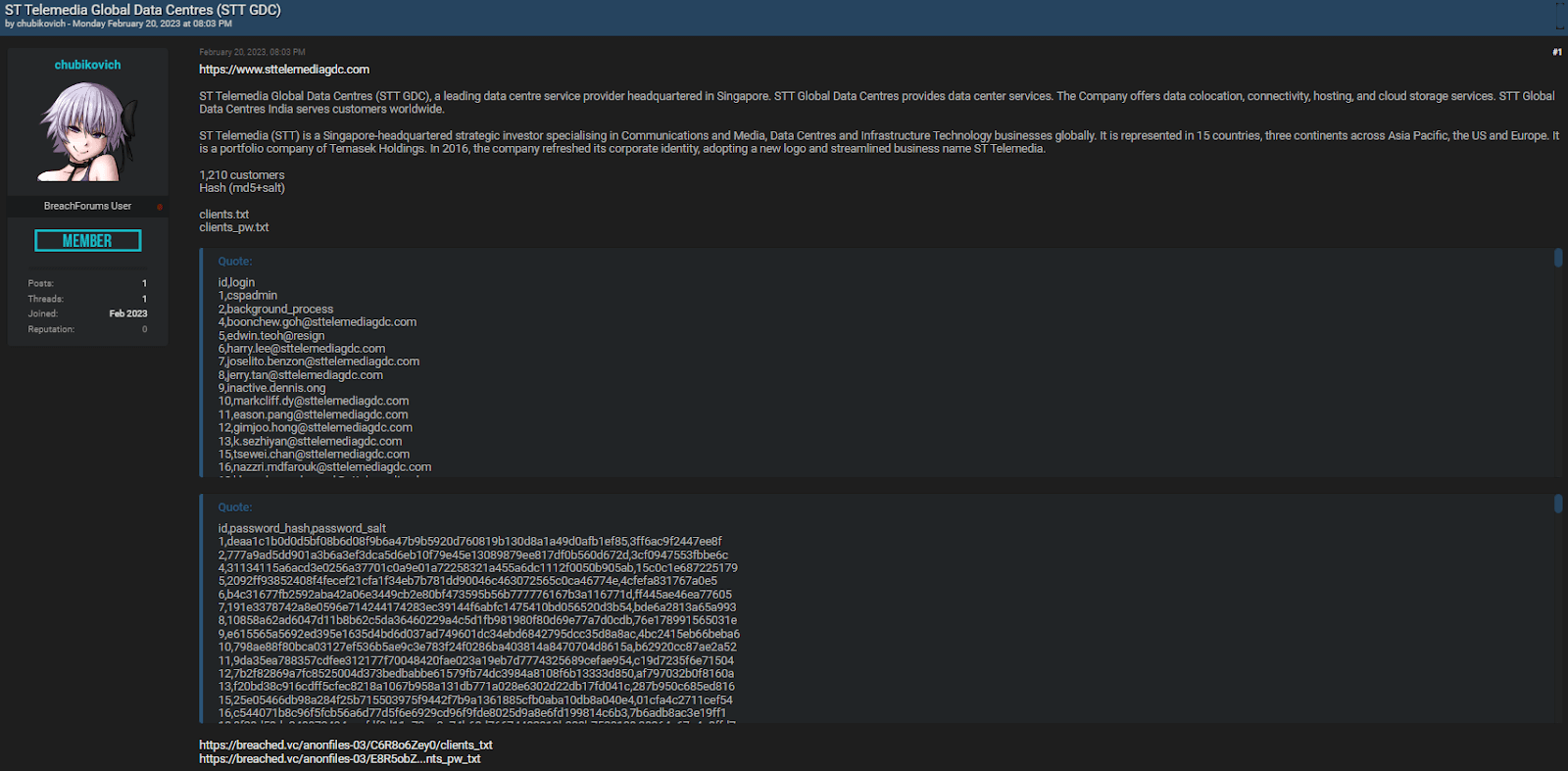
According to CSN, it has come to light that the login credentials for certain data center organizations have been posted on an underground forum called Breached[.]to.
As a result of the significant number of Fortune 500 companies represented in the data sets obtained during the investigation, the information has been shared with US law enforcement agencies.
Further Analysis
The cybersecurity experts at Resecurity have identified various threat actors on the Dark Web, with indications that they may have Asian origins.
The majority of forum sections have Chinese translation, and it is there where we could identify multiple actors originating from China and countries based in South-East Asia.
The actor extracted a list of CCTV cameras used in data centers as a means of monitoring the environment. It was also found that they extracted credential information pertaining areas such as IT staff and customers.
Furthermore, the APT performed active probing of the panels of the customers after they had gathered the credentials of the customers in order to collect information such as:
- Data center operations managers for enterprise customers
- List of purchased services
- Deployed equipment
There are a number of financial institutions from around the world that have been identified in the leaked data sets:
- Investment funds
- Biomedical research companies
- Technology vendors
- E-commerce
- Online marketplaces
- Cloud services
- ISPs
- CDN providers
While most of the organizations are located in countries as:
- The U.S.
- The U.K.
- Canada
- Australia
- Switzerland
- New Zealand
- China
In order to increase their effectiveness, security professionals should step up evaluations and mitigation efforts related to both OT and IT supply chain security. Communication with suppliers is also essential if a cyberattack compromises the data of clients and their accounts.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security