Contents:
Threat actors found a new method to inject malicious code into websites. They are now using an abandoned WordPress plugin, Eval PHP.
The plugin is still available in the WordPress plugins repository and had approximately 4,000 malicious installations per day this month.
The Abandoned Plugin
Eval PHP enables site administrators to embed PHP code in WordPress site pages and posts. The embedded code will then run when the user opens the page in a browser.
This plugin was last updated a decade ago, but it is still available through the WordPress plugins repository.
Researchers at Sucuri spotted this malicious trend in April 2023. Cybercriminals discovered that through this plugin they can inject secretive backdoors into websites. And the trend is growing as the Eval PHP has now around 4,000 malicious downloads daily.
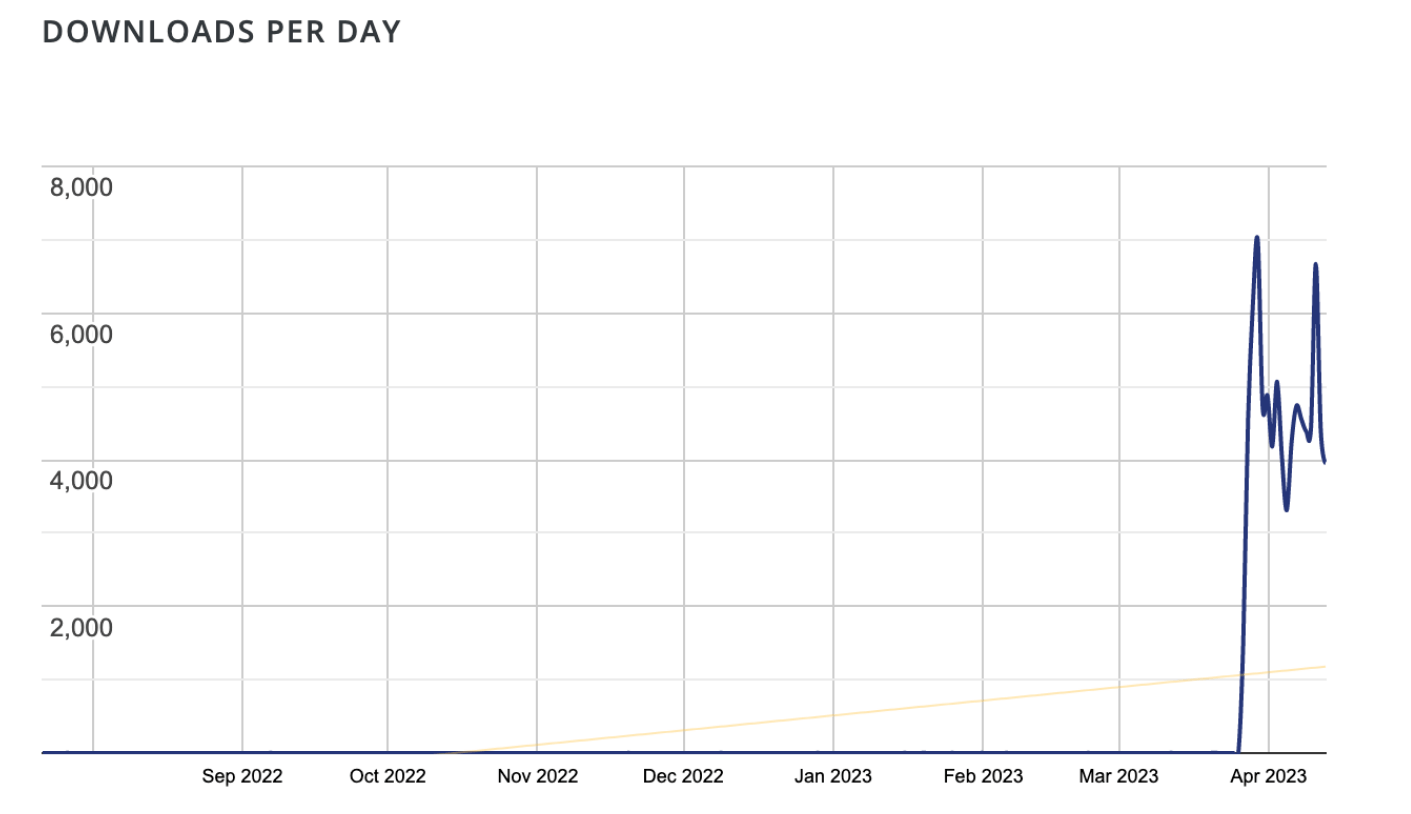
Using this method for code injection has a major advantage for hackers: they can use the plugin again and again. Threat actors can reinfect cleaned sites while the backdoor remains concealed.
The Malicious Code Injection
Threat actors deploy an already-known payload that enables attackers to remotely execute code over the hacked site.
The code injection goes into the database, specifically into the ‘wp_posts’ table. In consequence, the attack is harder to detect, evading file integrity monitoring, server-side scans, etc.
To do that, the threat actors use a compromised or newly created administrator account to install Eval PHP, allowing them to insert PHP code into pages and posts of the breached site using [evalphp] shortcodes.
When the cod runs, the backdoor is dropped in the site root. The name of the backdoor can be “3e9c0ca6bbe9.php” or any other name, depending on the attack.
Several different IP addresses cause the malicious Eval PHP plugin installations: 91.193.43.151, 79.137.206.177, 212.113.119.6.
To further evade detection, the code injection uses cookies and GET requests for C2 communication, instead of POST.
Moreover, the malicious [evalphp] shortcodes are planted in saved drafts hidden in the SQL dump of the “wp_posts” table and not on published posts. This is still enough to execute the code that injects the backdoor into the website’s database.
Protection Measures
Eval PHP is not the only old plugin that hackers can abuse. So, website owners are advised to remove outdated and neglected plugins that can become a security risk.
Further protection measures include employing a web application firewall, protecting admin panels, and maintaining a current WordPress installation. All these pieces of advice are met to enhance cybersecurity until the individuals in charge of overseeing the WordPress plugin repository remove the plugin.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









