Contents:
Many machines all around the world are at a halt. A faulty component in the latest CrowdStrike Falcon update is crashing Windows systems.
The mass outage causes worldwide chaos, with major banks, healthcare companies, media outlets, logistic companies, and even airlines among the victims. Many flights have been grounded, with queues and delays at airports, while shops and communications have also been hit.
This is affecting Windows workstations and servers, causing companies to go offline. Emergency services in the U.S. and Canada have also been affected, according to some reports.
What Caused the Outage?
CrowdStrike released an update on Friday to their threat feed, which was automatically applied by the software on users’ systems. However, the problem occurred when the update wrongly identified an important Windows process as harmful and blocked it.
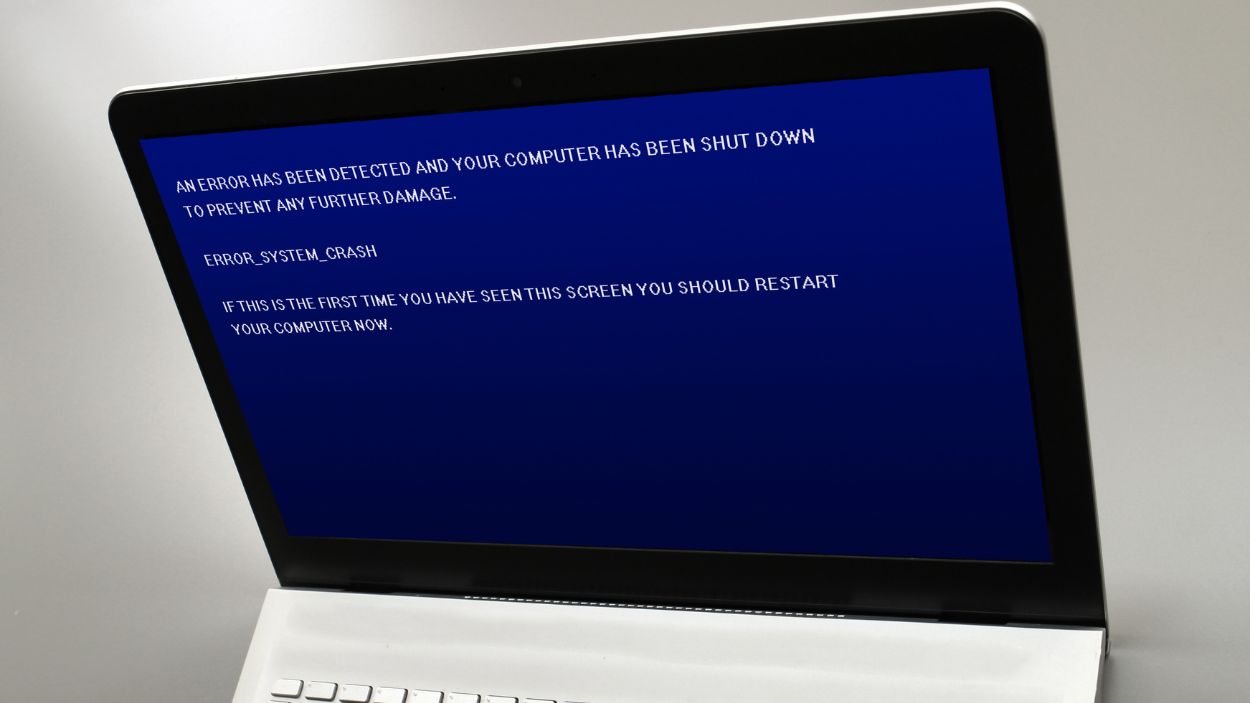
This caused Windows to crash and show a Blue Screen of Death (BSOD), leading to an endless reboot cycle. Each time Windows rebooted, CrowdStrike’s engine would block the critical process again, causing another crash.
The CEO of CrowdStrike, George Kurtz, took to his socials to address the cause.
He assured his followers that besides Mac and Linux hosts not being impacted, this was not a cyberattack or security incident.
The issue has been identified, isolated and a fix has been deployed. We refer customers to the support portal for the latest updates and will continue to provide complete and continuous updates on our website.
George Kurtz, CEO of CrowdStrike (Source)
The CrowdStrike team is fully mobilized to ensure the stability of their customers. Kurtz recommended organizations to ensure they’re communicating with CrowdStrike representatives through official channels.
At the time of writing this piece, a fix has been deployed by the CrowdStrike team. The only problem? It needs to be implemented manually on each machine.
The Fix And Why Is It Taking Time
For most systems, someone needs to physically go to each affected computer, start it in safe mode, and fix the issue manually.
For cloud systems, the process is more complicated. It involves shutting down virtual servers, copying their disks, and editing them to remove the problematic files.
If the data is encrypted, it must be decrypted first, which could be difficult if the decryption key is on one of the affected servers.
Outages Worldwide: Who Was Affected?
The impact is felt all around the world. The first reports came from Australia, where payment systems went down at Australian stores including Woolworths. The National Australia Bank, as well as other local financial institutions, were affected.
In the U.S., some 911 emergency service agencies were impacted, including the states of New York (EMS, police, and fire department), Alaska, Arizona, and Illinois. 911 services in parts of Canada have also been affected.
In Catalonia, Spain, the 061 emergency health hotline has been impacted, with authorities asking the citizens not to call the service unless there is an emergency.
Airports all around the world have been affected as well. According to the Dutch broadcaster NOS, the glitch created disruptions at Schiphol Airport and several flights operated by KLM and Transavia have been grounded.
The Melbourne Airport stated that it was experiencing a ‘global technology issue which is impacting check-in procedures for some airlines’.
In the U.S., the Federal Aviation Administration received requests to assist multiple airlines, including American Airlines, United, and Delta, with ground stops until ‘a technical issues impacting IT systems’ is resolved.
Other airports affected are in Tokyo, Delhi, Berlin, Barcelona, Brisbane, Edinburgh, Amsterdam, and London.
The healthcare systems were impacted as well, including hospitals in the Netherlands (Scheper, Slingeland Hospital) and Spain (the Terrassa University Hospital and the Catalan Oncology Institute in Barcelona). In Spain, fortunately, it was reported that they are starting to return to normal activity.
A Workaround to the Problem
The NCSC (National Cyber Security Centre) released an advisory on the CrowdStrike BSOD.
According to the institutions, symptoms include hosts experiencing a bugcheck or bluescreen error (also known as Blue Screen of Death or BSOD) related to the Falcon Sensor.
As per CrowdStrike, if hosts are still crashing and unable to stay online to receive the Channel File Changes, the following steps can be used to workaround this issue.
Workaround Steps
If your systems are still loop crashing, they might need manual intervention:
- Boot Windows into Safe Mode
- Navigate to the ‘C:\Windows\System32\drivers\CrowdStrike’ directory in Explorer
- Locate the ‘C-00000291*.sys’ file, right click and rename it to ‘C-00000291*.renamed’
- Boot the host normally
What Does Reddit Say?
Many professionals across multiple industries took to Reddit to share their thoughts on the situation.
Tens of thousands of endpoints have been affected and need to be checked. A Redditor commented in a threat that out of his company’s 350 thousand endpoints, 170 thousand devices were affected.
Another Australian Redditor mentioned that 50 thousand endpoints were affected at his company.
A Redditor from Malaysia stated that 70% of the laptops of the organizations he’s working for are down and stuck. The company received an order from HQ to shut down.
These are just a few glimpses.
A CrowdStrike Alternative? Yes, There Is!
If you are looking for a CrowdStrike alternative, why don’t you check out Heimdal®?
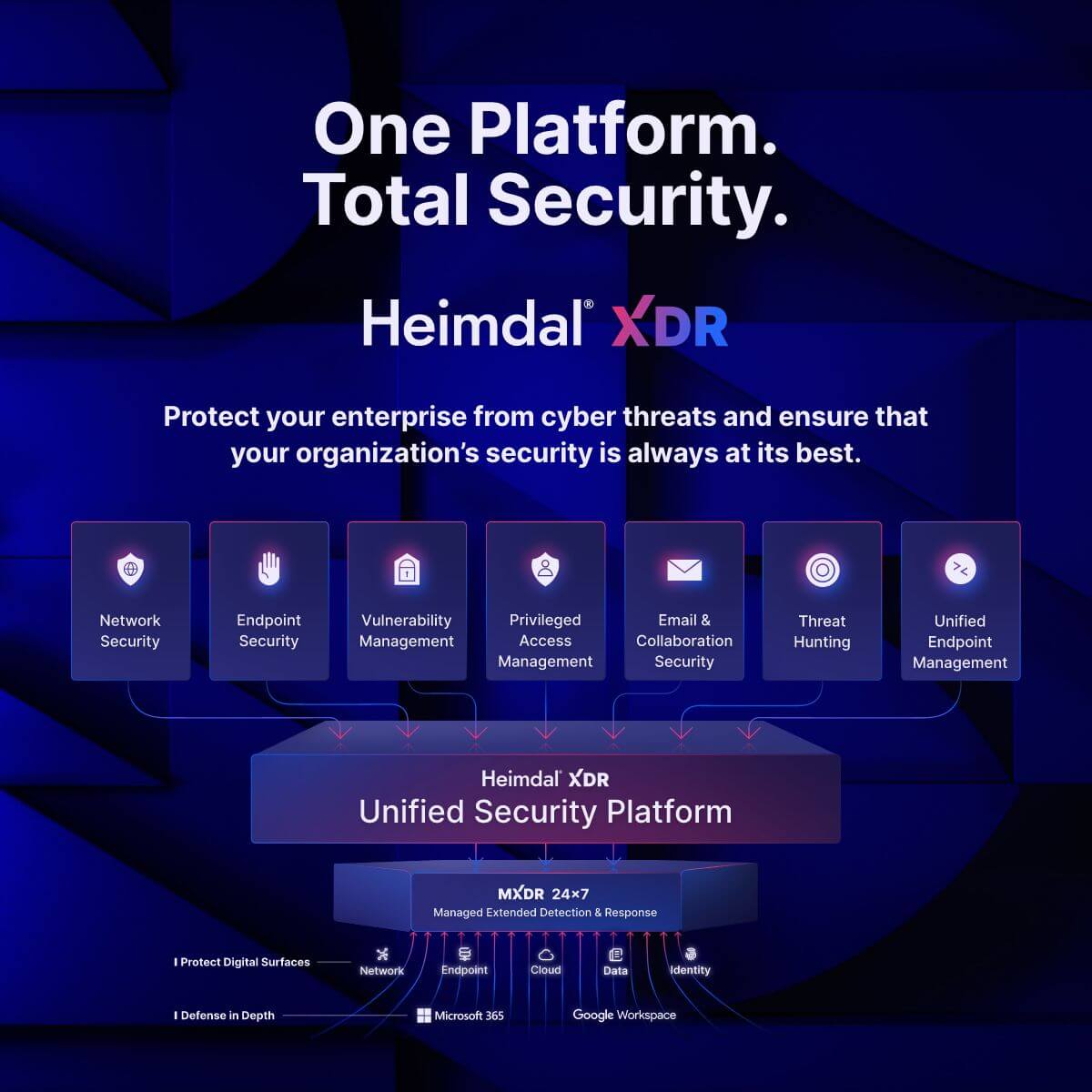
Heimdal® XDR (Extended Detection and Response), our Unified Security Platform, will help you eliminate the complexity of managing multiple security solutions and gain the peace of mind that comes with having a comprehensive, integrated approach to cybersecurity.
How Can Heimdal® Help You?
We are confident that our platform is the most comprehensive on the market, and here is why:
- All major cybersecurity solutions in one place;
- AI and ML threat intelligence;
- Instant, unified intelligence;
- Automated threat response and task management;
- APIs to most third-party point solution vendors;
- World-class, 24/7, global support;
- Continually evolving.
Our platform is the widest on the market with over 10 solutions included. Here is what you can find:
- Network security: A range of market-leading DNS security tools to help monitor, manage, and secure network-based connections.
- Endpoint security: Secure remote devices of all shapes and sizes through endpoint DNS security, next-gen antivirus, firewalls, and ransomware encryption protection.
- Vulnerability management: Create policies to automatically install patches and updates, so you can take the admin out of vulnerability management.
- Privileged access management: Define granular policies to govern who has access to what files, applications, and other devices. This includes tools to dynamically accept or deny access based on contextual signals – eliminating the need for standing privileges.
- Email and collaboration security: Detect and prevent incoming email-based threats, with advanced anomaly analysis to detect and repel even the most convincing phishing attempts.
- Threat hunting: Our threat detection platform allows IT teams to quickly detect and track anomalous behavior, together with risk scores and a forensic breakdown of the event, device, and associated applications. This makes effective and targeted responses much easier.
- Unified endpoint management: Manage devices of all shapes and sizes from one simple dashboard. No more clicking between disconnected apps to manage laptops, mobile devices, or BYOD devices.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security