Contents:
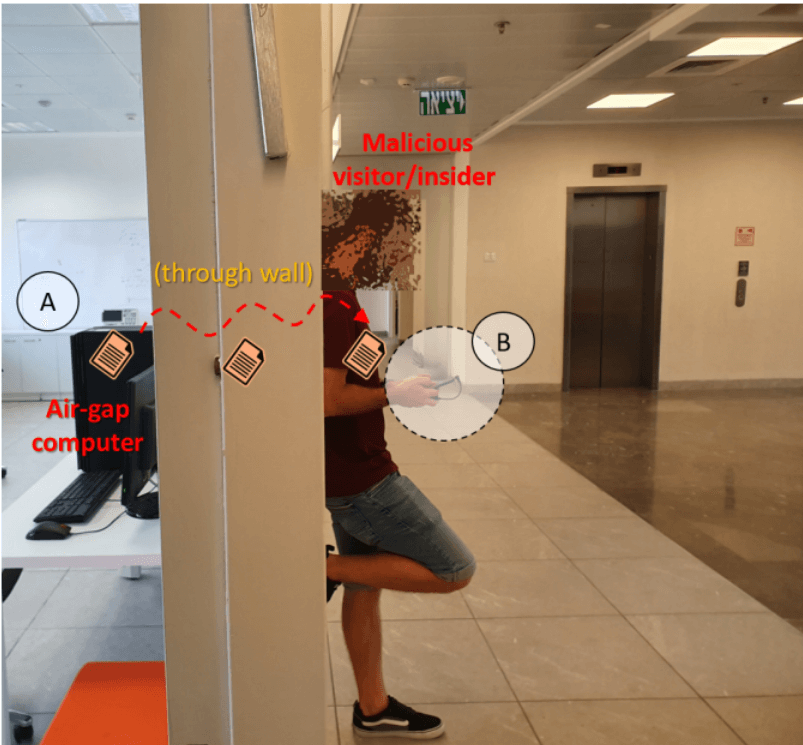
COVID-bit is a new assault strategy that uses electromagnetic waves to breach air-gapped computers, and it has a data transmission range of at least two meters (6.5 ft).
The exfiltrated data can be received by a close by smartphone or laptop, even when the two devices are separated by a wall.
This attack method has been discovered by Mordechai Guri, a researcher at Ben-Gurion University.
Details About the COVID-bit Method
Air-gapped computers are isolated from the Internet or any other network for security reasons. These are typically used in energy infrastructures, government agencies, military sites, and other sensitive environments.
For a cyberattack to succeed on such systems, physical access to the air-gapped device or network is first needed. An intruder can plant malware on the targeted computers.
And we know that such events had happened in the past: an Iranian uranium enrichment facility has been breached, and a U.S. military base was infected with the Agent.BTZ.
For the COVID-bit attack method, researchers designed a software that “regulates CPU load and core frequency in a particular manner to make the power supplies on air-gapped computers emanate electromagnetic radiation on a low-frequency band (0 – 48 kHz)”, according to Bleeping Computer.
The primary source of electromagnetic radiation in SMPS is because of their internal design and switching characteristics. In the conversion from AC-DC and DC-DC, the MOSFET switching components turning on or off at specific frequencies create a square wave.
These electromagnetic waves can transmit raw data to a receiver which can be a laptop or a smartphone. The receiver device needs a loop antenna connected to the 3.5mm audio jack, like headphones/earphones to capture the transmission. Then, a noise reduction filter is applied, raw data is demodulated, and the content is decoded.
Testing Results
The COVID-bit method was tested “with three types of systems: PC workstations, laptops, and embedded devices.” During testing, the zero-bit error rate was kept on PCs and embedded devices for up to 200 bps and on laptops for up to 100 bps.
Desktop PCs had the best transmission rate, up to 500bps for a bit error rate between 0.01% and 0.8%, laptops performed worse because of their energy-saving profiles and not strong enough signals, and the embedded devices had a limited distance caused by their weak power supply.
At the maximum tested transmission rate (1,000 bps), a 10KB file would be transmitted in 80 seconds, a 4096-bit RSA encryption key could be transmitted in as little as 4 seconds or as much as ten minutes, and the raw data from one hour of keylogging would be sent to the receiver in 20 seconds.
Live keylogging would work in real-time, even for transmission rates as low as five bits per second.
How to Stay Safe of the COVID-bit Method
Although these safety measures have disadvantages too, they can offer you a base for your protection strategy.
To keep your devices and network safe from this attack method you should strictly restrict access to the devices to prevent the installation of any malware, even if this does not clear the inside threats.
Monitoring the CPU core usage and the computer’s behavior for any suspicious patterns can also help. This security measure requires analyzing big loads of data and creates many false alarms.
Or you can lock the CPU core frequency at a certain number, with the goal of making the creation of the data-carrying signal more difficult, if not altogether preventing it. This approach has the disadvantage of reducing processor performance or wasting a lot of energy, depending on the lock frequency.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







