Contents:
A new malware has been discovered in the wild by security researchers. Called CosmicEnergy, the malware is designed to disrupt industrial systems. Sources say that the Russian cybersecurity group Rostelecom-Solar (fka Solar Security) is behind the malware.
IEC-104-compliant remote terminal units (RTUs), which are widely utilized in electric transmission and distribution operations throughout Europe, the Middle East, and Asia, are the precise targets of the malware.
What We Know About CosmicEnergy So Far
CosmicEnergy was found after a sample with a Russian IP address was uploaded to the VirusTotal malware analysis portal in December 2021. The analysis conducted on the leaked malware sample revealed several noteworthy aspects regarding CosmicEnergy and its functionality.
The malware shares similarities with previous OT malware like Industroyer and Industroyer.V2, both used in attacks targeting Ukrainian energy providers. Similar to Industroyer, CosmicEnergy likely gains access to target OT systems via compromised MSSQL servers using the Piehop disruption tool. CosmicEnergy and its operation include several remarkable characteristics that have been discovered through analysis of the released malware sample.
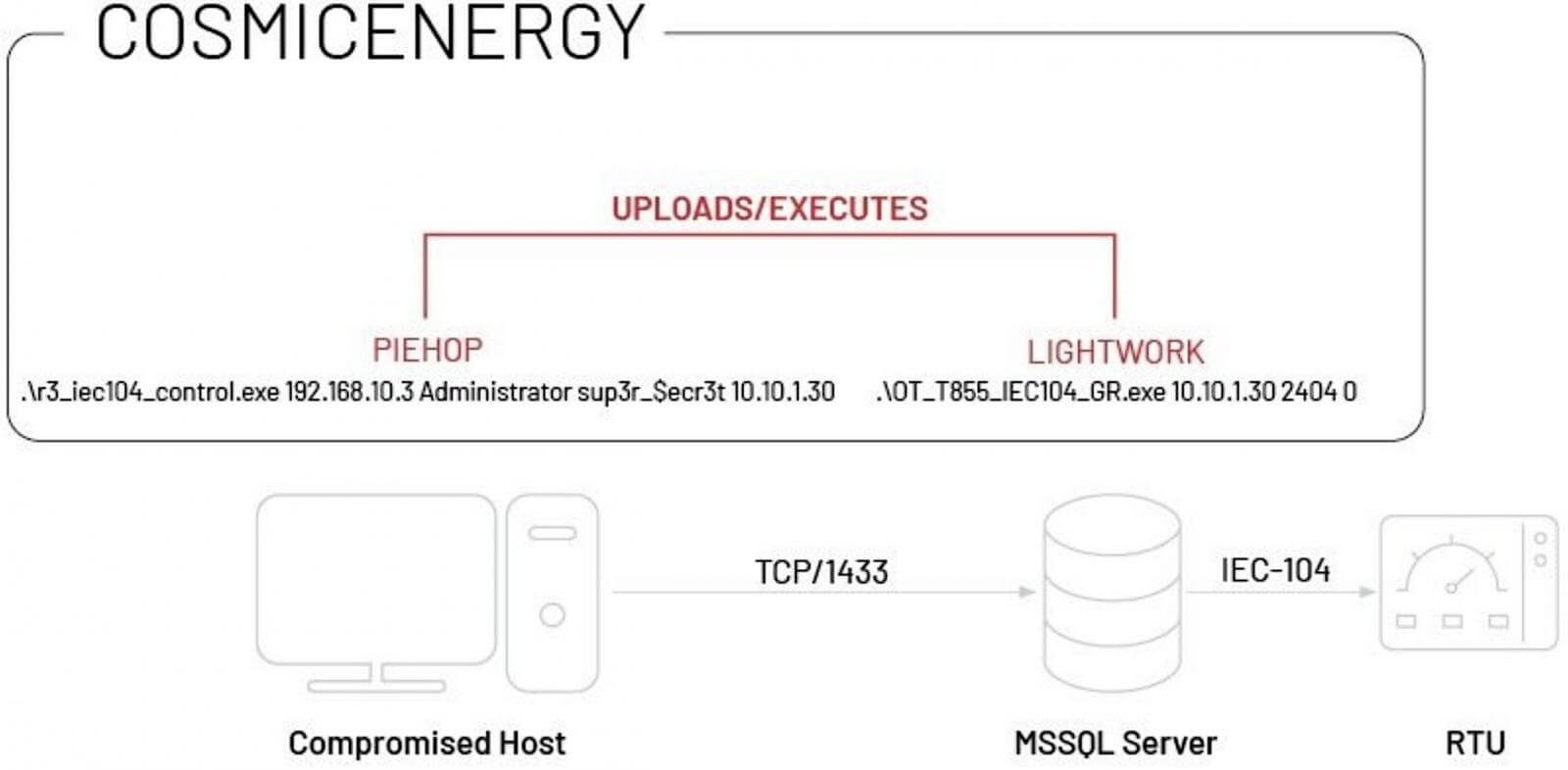
Execution Chain of CosmicEnergy (Source)
Security researchers believe that the newly discovered malware may have been developed by Rostelecom-Solar, a Russian cybersecurity company, to be a red teaming tool designed to simulate disruption exercises.
As reported by BleepingComputer, it is believed that CosmicEnergy may also be used by Russian threat actors in disruptive cyberattacks targeting critical infrastructure, similar to how other red team tools are used. This suspicion is based on information that is publicly available and demonstrates that Rostelecom-Solar received funding from the Russian government for cybersecurity training and simulating electric power disruption.
A comment in the code of the malware indicated that the sample uses a module associated with a project named “Solar Polygon”, which was identified to be developed by Rostelecom-Solar. Even if the information is not sufficient as of now to draw a concrete conclusion, it is very likely that the malware was developed by the Russian group or an associate of theirs.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








