Contents:
A cybercriminal group called Daixin Team is actively launching ransomware attacks against the U.S. healthcare sector. CISA, the FBI, and the Department of Health and Human Services (HHS) issued an advisory to help security professionals stop attacks using this strain of ransomware.
The Daixin Team is a ransomware and data extortion group that has targeted the HPH Sector with ransomware and data extortion operations since at least June 2022.
Daixin Team Is Targeting Healthcare Services
According to Bleeping Computer, since June, attackers from Daixin Team have been linked to multiple ransomware attacks in the health sector. In these attacks, they have encrypted systems that are used for a wide range of healthcare services, such as storing electronic health records, diagnostics, imaging services, and intranet services.
They are also acknowledged for stealing patient health information (PHI) and personally identifiable information (PII) and using it to threaten victims into paying ransom by placing the stolen information online. The ransomware gang gets access to victims’ networks by abusing known vulnerabilities in VPN servers or by using compromised VPN credentials for accounts that have multi-factor authentication (MFA) disabled.
After gaining access to the system, they move laterally through the victim’s networks by using the Remote Desktop Protocol (RDP) and the Secure Shell (SSH).
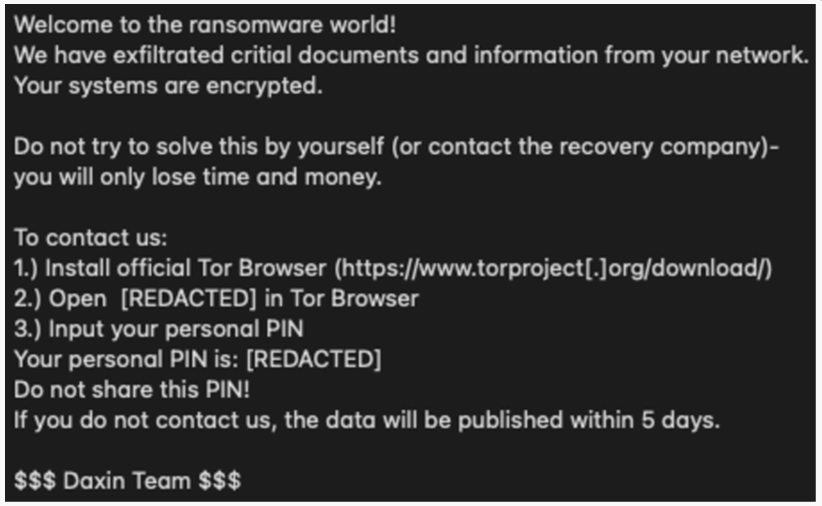
The Ransom Note
They elevate their privileges in order to deploy the ransomware payloads by using a variety of methods, including credential dumping. Before encrypting their targets’ machines, they use Rclone or Ngrok to send stolen data to dedicated virtual private servers (VPS).
With the intention of encrypting the systems using ransomware, this privileged access is also used to “gain access to VMware vCenter Server and reset account passwords for ESXi servers in the environment.”
According to third-party reporting, the Daixin Team’s ransomware is based on leaked Babuk Locker source code. This third-party reporting as well as FBI analysis show that the ransomware targets ESXi servers and encrypts files located in /vmfs/volumes/ with the following extensions: .vmdk, .vmem, .vswp, .vmsd, .vmx, and .vmsn. A ransom note is also written to /vmfs/volumes/.
CISA’s Advice
To protect against Daixin Team’s attacks, as stated in the alert published by CISA, U.S. health organizations are instructed to do the following:
- Install updates for operating systems, software, and firmware as soon as they are released.
- Enable phishing-resistant MFA for as many services as possible.
- Train employees to recognize and report phishing attempts.
It is worth mentioning that CISA and FBI issued, earlier this year, a warning that attackers known for primarily targeting the healthcare and medical industries with Zeppelin ransomware might encrypt files multiple times, making it more difficult to recover them.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










