Contents:
China might be behind a malicious campaign targeting Middle Eastern countries linked to BackdoorDiplomacy, an advanced persistent (APT) threat group.
The espionage campaign against a telecom in the region is believed to have started on August 19th, 2021, by exploiting flaws in the Microsoft Exchange Server.
The attackers went after the binaries by loading them onto the system, using legitimate and bespoke tools to gain data about the environment, move laterally, and evade detection.
Researchers shared with The Hacker News a report that outlines the malicious tools used by the threat actors. One of the first tools deployed was the NPS proxy tool, similar to the IRAFAU backdoor.
“Starting in February of 2022, the threat actors used another tool – the Quarian backdoor. They also used many other scanners and proxy/tunneling tools.”
ESET was first documented BackdoorDiplomacy in June 2021, with intrusions primarily aimed at diplomatic entities and telecommunications companies in Africa and the Middle East to deploy Quarian (aka Turian).
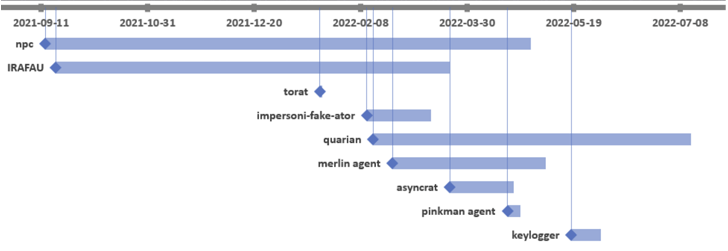
The investigation showed that the motive stemmed from espionage, evidenced by using a keylogger and PowerShell scripts to collect email content. The IRAFAU malware was delivered after gaining a foothold and used for information discovery and lateral movement.
Sometimes more sophisticated malware activity is facilitated by downloading and uploading files from and to a command-and-control (C2) server, launching a remote shell, and executing arbitrary files.
The second tool used in the operation was a modified version of Quarian, which contains a broader range of capabilities to control the compromised host.
The Impersoni-fake-ator tool is also used, which is embedded in legitimate utilities like DebugView and Putty. The Impersoni-fake-ator tool captures system metadata and executes a decrypted payload received from the C2 server.
The use of open-source software such as ToRat, an administration tool for Go, and AsyncRAT characterizes the intrusion. The latter is likely dropped via Quarian.
Bitdefender attributed the attack to BackdoorDiplomacy because of C2 overlaps observed in previous campaigns conducted by the group.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








