Contents:
Blind Eagle, a financially-motivated threat actor previously observed launching operations against organizations in Colombia and Ecuador, has reemerged with a sophisticated toolset and a complex infection chain.
The latest findings from Check Point shed light on the group’s methods, such as the employment of upgraded tools and government-themed baits to trigger the kill chain. Blind Eagle, also known as APT-C-36, is a cyber threat group that has been targeting mainly South American countries with widespread attacks since 2018.
In September 2021, Trend Micro discovered Blind Eagle’s operations, which included a spear-phishing campaign aimed primarily at Colombian entities and designed to deliver a commodity malware known as BitRAT. The campaign also targeted individuals or organizations in Ecuador, Spain, and Panama.
A Multi-Step Approach that Exploits Mshta.exe
The first step in a series of attacks is sending phishing emails with a malicious link that, when clicked, installs an open-source trojan called Quasar RAT and attempts to obtain access to the victim’s bank accounts.
Some of the banks that have been a focus include Banco AV Villas, Banco Caja Social, Banco de Bogotá, Banco Popular, Bancoomeva, BBVA, Colpatria, Davivienda, and TransUnion, explains The Hacker News.
Blind Eagle is a strange bird among APT groups. (…) Judging by its toolset and usual operations, it is clearly more interested in cybercrime and monetary gain than in espionage.
If the recipient of the email is situated in a country other than Colombia, the attack is stopped and the user is taken to the Migración Colombia website. As with the Colombian campaign, the Ecuadorian campaign uses geo-blocking technology to restrict access from outside the country.
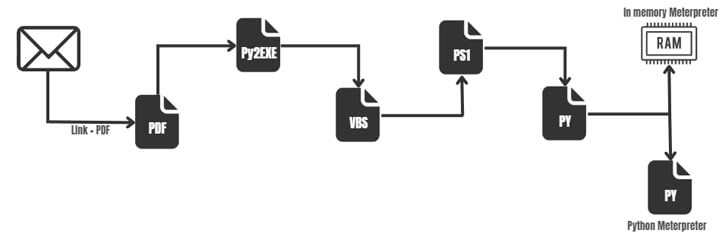
Instead of just downloading a RAT malware, this attack uses a multi-step approach that exploits the legitimate mshta.exe binary to run VBScript within an HTML file, which then downloads two Python scripts.
The first one, ByAV2.py, is an in-memory loader designed to run a Meterpreter payload in DLL format. mp.py is also a Meterpreter artifact, but it’s written in Python. This suggests that the threat actor could be using one of them as a backup method to keep a backdoor open to the host.
This news comes just days after it Qualys revealed that an unknown threat actor is using data stolen from a Colombian cooperative bank to send out phishing emails that ultimately lead to the installation of the BitRAT malware.
CheckPoint researchers’ complete report is available here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










