Contents:
Researchers warn that BlastRADIUS, a flaw in the RADIUS network authentication protocol helps hackers conduct Man-in-the-middle (MitM) attacks.
RADIUS is short for Remote Authentication Dial-In User Service. It is a client/server protocol for authenticating users and devices. Various networked devices like switches, routers, access points, and other routing infrastructure rely on it.
RADIUS runs in the application layer and can use Transmission Control Protocol (TCP) or User Datagram Protocol (UDP).
More about the BlastRADIUS flaw
Blast-RADIUS uses protocol vulnerability CVE-2024-3596 and the MD5 hashing algorithm. Thus, they enable attackers to access the RADIUS traffic. Further on, hackers will be able to:
- manipulate server responses
- add arbitrary protocol attributes
- gain admin privileges on RADIUS devices
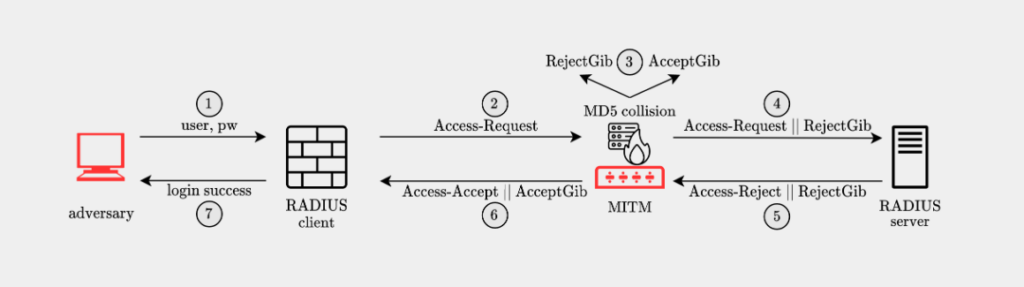
Source – Blast-RADIUS research team
How can they authenticate as admins without requiring brute force or stealing credentials?
Researchers explained that once they get access to a network that uses RADIUS, the attacker can craft a response to the RADIUS server to change the response to any of the valid responses. There are 4 possible types or response:
- Access-Accept
- Access-Reject
- Access-Challenge
- Protocol-Error
But in this case, the type doesn’t matter.
This ability allows the attacker to change the Reject response to an Accept or the other way around.
If the attacker intercepts an Access-Challenge response, which is typically used in Multi-Factor Authentication (MFA), they can change it into an Access-Accept response. This will allow them to bypass the MFA used within RADIUS.
The researchers also said that
Due to the flexible, proxied nature of the RADIUS protocol, any server in the chain of proxied RADIUS servers can be targeted to succeed in the attack.
Source – Carnegie Mellon University, Vulnerability Note VU#456537
Prevention measures against BlastRADIUS attacks
Security specialists found the exploitation possibility for the RADIUS flaw concerning. They say that the MD5 hashing algorithm is not considered reliable in this case.
The recent publication of the “Blast RADIUS” exploit has shown that RADIUS needs to be updated. It is no longer acceptable for RADIUS to rely on MD5 for security. It is no longer acceptable to send device or location information in clear text across the wider Internet.
Source – IETF
For the moment, researchers urge network admins to enforce the following prevention measures:
- upgrade to RADIUS over TLS (RADSEC)
- start using “multihop” RADIUS deployments
- use restricted-access management VLANs or TLS/ IPsec tunneling to isolate RADIUS traffic from internet access
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







