Contents:
BadUSB vulnerability is considered one of the worst IT vulnerabilities ever found.
To remove BadUSB vulnerability, first you need to create a blacklist. After that, avoid automatic USB installation and disable inactive USB ports. But let’s see what is BadUSB and how it works.
Discovered a few months ago, this big security hole affects the way USB devices communicate with an operating system.
BadUSB is a major security flaw that allows online criminals turn a simple USB device, for example a keyboard, into a means of sending malicious commands from the user’s computer to trigger an action or contact a server controlled by hackers. To be able to do this, the firmware in the USB controller chip is reprogrammed. Protection against this type of threat is difficult to secure, since there are no means available against this type of threat.
Using this flaw, cyber-criminals can obtain important details on exploiting vulnerabilities in USB controllers, present in many types of USB devices. Since USB devices are used on a regular basis and are part of our systems, we need to know how to stay safe from this vulnerability.
Our security researchers have now come up with a few simple steps you can follow in your Windows operating system to stay safe:
Create a Blacklist
There are several ways we can limit our exposure to this vulnerability, and one of these methods is by creating a blacklist.
Follow the steps below:
- Go to Start – > Run and type in gpedit.msc to reach Local Group Policy Editor.
- Access the following: Computer Configuration > Administrative Templates > System > Device Installation > Device Installation Restrictions. You should arrive in the location from the image below:
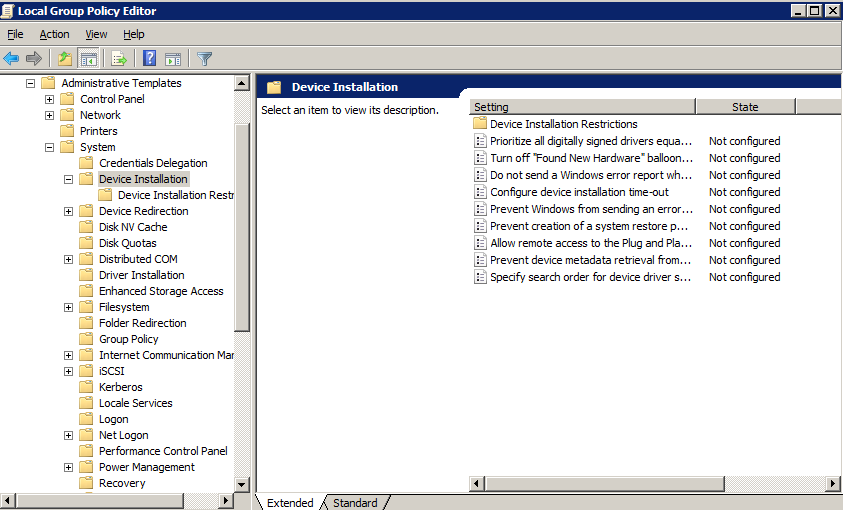
- Double click Prevent installation of devices using drivers that match these device setup classes and choose Enable.
- In the same location, click Show to create a blacklist of USB devices via their GUID.
You have a few examples below:
4d36e96b-E325-11CE-BFC1-08402BE10318 – this one controls the automatic installation of USB keyboards.
4D36E972-E325-11CE-BFC1-08012BE10318 – this one corresponds to the NIC (network interface controller)
e0cbf06c-cd8b-4647-bb8a-263b45f0f974 – this one is for bluetooth.
For more information about GUID numbers, check this quick guide.
Avoid automatic USB installation
Another option to keep your system safe from the BadUSB vulnerability is to disable the automatic installation of new USB devices.
Therefore, go to the same location as above and follow these steps:
- Double click Prevent installation of removable devices and Enable it.
- Double click Allow administrators to override Device Installation Restrictions policies and Enable it.
In this case, we need to underline that if you want to install a removable device in the future, you will need to do it with Administrative rights.
Disable inactive USB ports
Though it is not a very popular method, our security researchers suggest that you should disable those inactive USB ports.
We also need to emphasize that unknown USB devices from uncertain sources should not be installed on the system.
Conclusion
When we think of system vulnerabilities and malware, we naturally imagine an operating system connected to the Internet, that needs to protect valuable data and private information from all sorts of online threats.
But malware and security flaws can be spread and addressed also through a USB device. Using a USB device for this malicious purpose has now become a favorite tool for online criminals’ actions. For this reason, we advise caution when using an unknown USB device or one that comes from an unknown location or source.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








