Contents:
French insurance company AXA confirmed on Sunday that it has become a victim of a ransomware attack. The incident comes days after the company officially announced that it would stop bearing the cost of ransomware crime payments.
The group said the threat actors had targeted its Asia Assistance division, impacting IT operations in Thailand, Malaysia, Hong Kong, and the Philippines, adding that “there is no evidence that any more data has been accessed.”
It was later confirmed that the infamous Avaddon ransomware gang has claimed responsibility for the attack. The group said on Saturday that they had hacked the AXA’s Asia operations and stolen three terabytes of data, in a dark web post seen by Hackread.
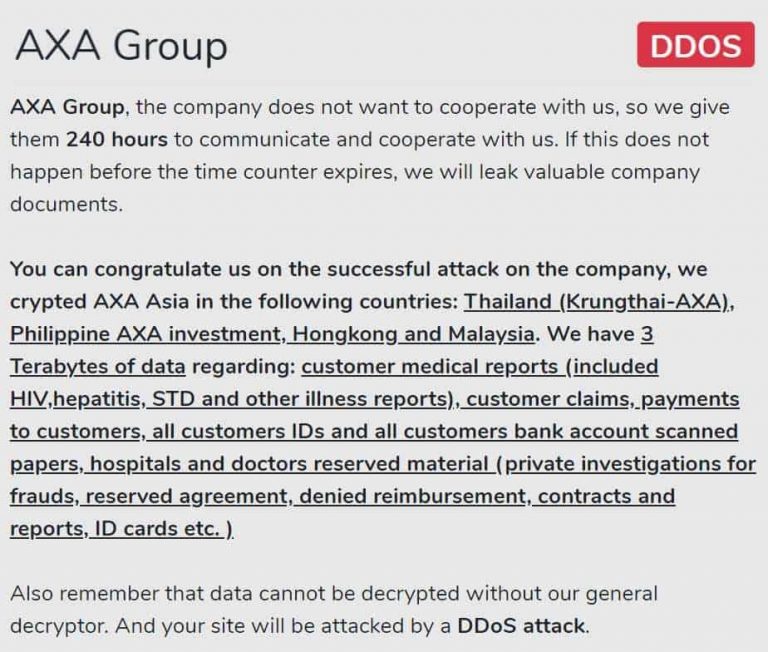
Image source: Hackread.com
Avaddon is a Ransomware as a Service (RaaS) operation that asks affiliates to follow certain rules and pays each one of them with 65% of the ransom payments they bring in, with the operators getting a 35% share, with the average ransom payment demanded by Avaddon affiliates being roughly 0.73 for a decryption tool.
The ransomware gang’s dark web post mentioned that the data exfiltrated from the AXA Group includes:
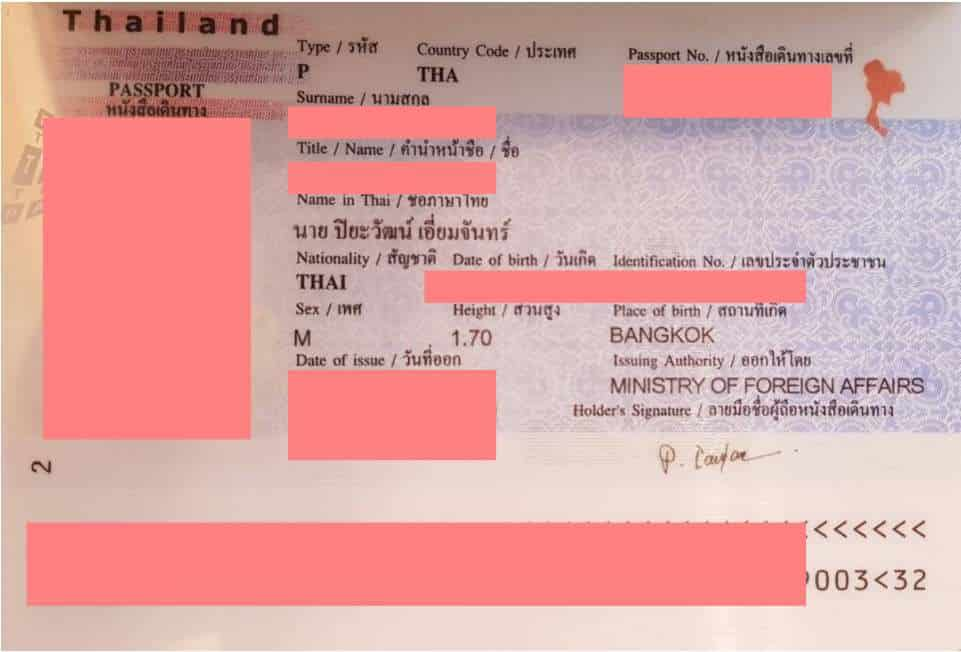
- ID cards;
- Passport copies;
- Customer claims;
- Reserved agreements;
- Denied reimbursements;
- Payments to customers;
- Contracts and reports;
- All customers IDs and all customers bank account scanned papers;
- Hospitals and doctors reserved material (private investigations for frauds);
- Customer medical reports (included HIV, hepatitis, STD, and other illness reports).

Images source: Hackread.com
The Avaddon ransomware gang follows the same MO as other ransomware groups such as breaching the security of its target, exfiltrating data and locking the files on the victim’s system, and demand ransom payment for a decryption key.
However, if the ransom is not paid, Avaddon carries out DDoS attacks on the network of its victim in an attempt to force them to pay the ransom. This threat coming in addition to leaking stolen data and encrypting their target’s system.
Avaddon ransomware samples were first found and identified in February 2019, with Avaddon starting the recruitment of affiliates in June 2020 after the launch of a massive spam campaign that was targeting users worldwide.
Unlike the DarkSide group that was responsible for the attack on Colonial Pipeline, but ended up quitting its operation, the Avaddon ransomware gang is on the lookout for new targets.
As we always say, the best way to stay safe from damage regarding ransomware infections is to maintain regularly updated backups. It is also advised to use a powerful anti-malware tool in order to get protection in real-time.
If your network gets infected with Avaddon ransomware, make sure you check out our list of Free Ransomware Decryption Tools and download the Avaddon ransom decryption tool.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








