Contents:
Experts have discovered a phishing campaign that has been going on for over a year. Its target? The German automotive industry. What threat actors are trying to do is to infiltrate password-stealing malware into the victims’ systems.
More Details on the Malware Campaign Focused on German Automakers
According to the researchers at Checkpoint, who published a report on this topic, the phishing campaign under discussion became active around July 2021 with its activity still being carried out at the present moment.
Its targets are car manufacturers and dealers in Germany, the threat actors behind it managing to duplicate genuine sites belonging to various companies for the purpose of registering lookalike domains. This technique is known as domain squatting.
These spoof websites are employed to distribute phishing emails in German and to serve as a host for malicious payloads.
The campaign also leveraged various MaaS info-stealers according to researchers, these involving BitRAT, Raccoon Stealer as well as AZORult. It seems that all three malware are put for sale on cybercrime markets.
Most of the targets are related to the German auto-industry sector and the attacks were designed to deploy various types of info-stealing malware. The threat actors behind the operation registered multiple lookalike domains, all imitating existing German auto businesses that they later used to send phishing emails and to host the malware infrastructure.
How Does the Infection Chain Unfold?
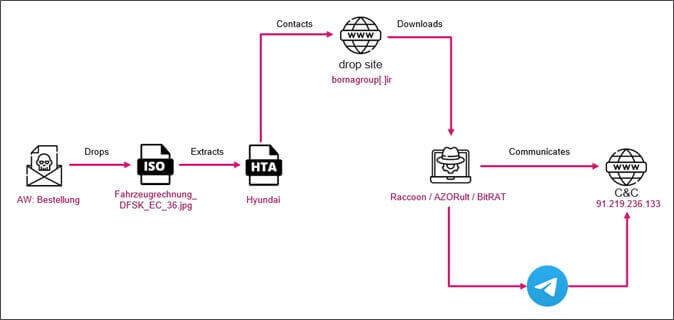
The infection process begins with an email that appears as if it comes from a car dealership. The subject of the email is “re: order” and its content is written in the German language. It also includes an ISO file attachment dubbed “vehicle invoice”. So basically, the email appears to be an automobile transfer receipt.
If the user who receives it doubles click on the ISO attachment, a warning message will pop up, followed by a request to the recipient to open an .HTA (HTML Applications) file.
This .HTA file encompasses JavaScript or VBScript code execution by means of HTML smuggling.
What the targeted user actually sees is a decoy document, but the problem lies in what happens meanwhile in the background: malicious code collects malware payloads that will be then executed.
The experts explain that the reason why ISO disk image archives are employed by threat actors is that this is a popular technique that can help them evade the NTFS Mark-of-the-Web trust control (MOTW).
Below there is a representation of the infection chain the experts depicted in their report:
What’s the Goal of This Malware Campaign?
According to the same researchers, the goal of this malware campaign seems to be industrial espionage or BEC (Business Email Compromise) cyberattacks. 14 targeted entities were discovered, all of them being German companies related to the auto-making industry, but no particular name is revealed.
We discovered a targeted attack being aimed at German businesses, mainly car dealers. The threat actors are using a vast infrastructure designed to mimic existing German companies. The attackers used phishing emails, with a combination of ISO\HTA payloads that, if opened, would infect victims with various info stealing malware. (…) The targets are carefully selected and the way the phishing emails were sent would allow correspondence between the victims and attackers. One possibility is that the attackers were trying to compromise car dealerships and use their infrastructure and data to gain access to secondary targets like larger suppliers and manufacturers. That would be useful for BEC (Business, Email Compromise) frauds or industrial espionage.
How Can Heimdal™ Help?
Get full protection against Business Email Compromise with Heimdal Fraud Prevention, a solution that uses 125 vectors of analysis to keep your critical business assets safe and sound!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










