Contents:
Hamas-linked cybercrime organization dubbed ‘APT-C-23’ was noticed catfishing Israeli officials working in defense, law, enforcement, and government institutions, resulting in the deployment of new malware.
The operation employs high-level social engineering tactics, including setting up bogus social media accounts and maintaining a long-term relationship with the targets prior to the spyware delivery.
Experts at security technology company Cybereason, who have dubbed this recent campaign “Operation Bearded Barbie,” stated that the APT-C-23 hacking gang is also deploying new tailored backdoors for Windows and Android devices aimed at espionage.
The Process
Hackers have created multiple fictitious Facebook profiles using made-up personas and stolen or AI-generated photos of beautiful women then contacted the victims via these fake accounts. They have spent months organizing these profiles in order to make them look realistic, writing posts in Hebrew and liking groups and famous pages in Israel.
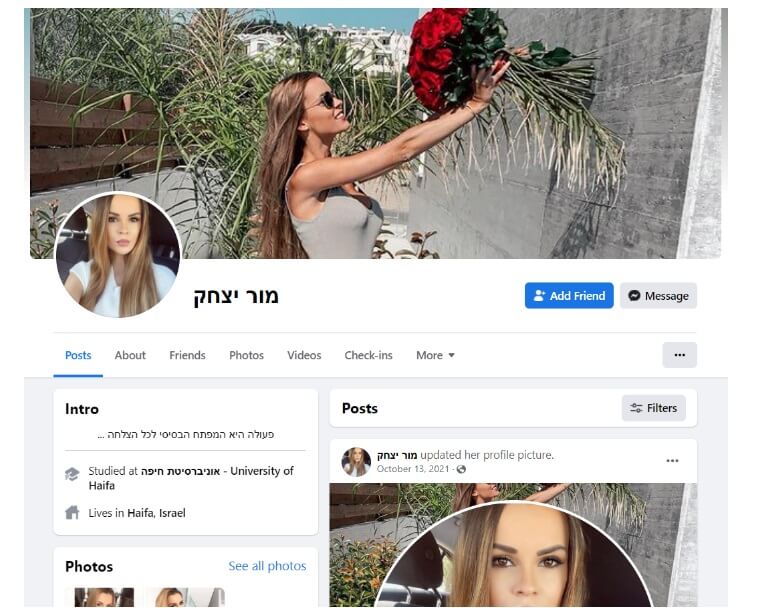
After building trust in the relationships with the victims by establishing a connection with them for a while, the malicious actors suggest moving the conversation to WhatsApp, allegedly for better privacy.
The hackers now propose a new change to a presumably more discrete Android IM app, which is in fact the VolatileVenom backdoor.
At the same, the operative transmits a link to a RAR file that appears to contain a sexual movie but is actually a downloader for the BarbWire backdoor.
Starting with VolatileVenom, this Android malware masquerades as a messaging app, most commonly Wink Chat.
As explained by BleepingComputer, during the initial launch and sign-up process, the app shows a false error and announces that it will automatically delete itself from the device, but it actually continues to run in the background and:
- Steal SMS messages
- Read contact list information
- Use the camera of the device to take pictures
- Steal files with the following extensions: pdf, doc, docs, ppt, pptx, xls, xlsx, txt, text
- Steal images with the following extensions: jpg, jpeg, png
- Record audio
- Use phishing to steal login info to Facebook and Twitter
- Remove system notifications
- Get installed applications
- Restart Wi-Fi
- Record regular calls and WhatsApp calls
- Extract call logs
- Download files to the infected device
- Take screenshots
- Read notifications on WhatsApp, Facebook, Telegram, Instagram, Skype, IMO, Viber
- Get rid of any notifications raised by the system
If the target’s device is running Android 10 or later, the app will use a Google Play, Chrome, or Google Maps icon. It completely conceals its app icon on earlier Android versions.
The hackers will eventually send the victim a RAR file containing supposedly nude pictures or videos but this file actually holds the Barb(ie) downloader malware, which installs the BarbWire backdoor.
Barb(ie) then connects to the command and control servers (C2) and transmits a system ID profile, and it also generates two scheduled tasks to ensure persistence. Eventually, the BarbWire backdoor is downloaded and installed on the device.
Among others, the BarbWire backdoor includes features like persistence, OS reconnaissance, data encryption, keylogging, screen capturing, and audio recording.
APT-C-23 employs several methods that have been used in previous operations against Israeli targets, but it is constantly evolving, adding new tools and more sophisticated social engineering efforts.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








