Contents:
One shady app is all it takes for hackers to slip into your system. It could be something you clicked on in a phishing email, a sketchy YouTube-to-MP4 converter, or a fake version of expensive software that you thought you could download for free.
Application control keeps you safe from such bad decisions. As an endpoint security tool, it decides what software can execute or not while also helping your company to stay compliant with zero-trust policies.
In this article, I will discuss how application control works, its key features, and core benefits. Find out more about how app control relates to the broader concept of privileged access management and how Heimdal can assist you. To get more useful tips on safeguarding access to your company’s sensitive data, also read this PAM best practices checklist.
How Application Control Works
Application Control acts like a guardian for your endpoints. It monitors every process initiated on a device and cross-references them against a set of rules.
These rules are based on factors like:
- software name
- file path
- publisher
- digital signature
If a process isn’t on the approved list, it’s blocked almost instantly. Thus, it prevents harmful or unauthorized software from executing.

Application Whitelisting vs. Application Blacklisting
Apps of all sorts help people do their jobs easier and faster. They improve connectivity and help streamline the workflow of thousands of employees worldwide. Yet, they can also turn into an attack vector if you disregard security best practices.
Application control solutions have two main strategies against malicious software: whitelisting or blacklisting.
Application whitelisting allows a number of pre-approved programs to run while blocking all others without requiring user permission. It is the strictest form of app control. You can set it up so that you don’t necessarily need to update it each time an employee needs to use new software. Analyse your working environment and its needs thoroughly and build up the allowlist so that it has minimum impact on the workflow without damaging your security posture.
Application blacklisting works by blocking specific unwanted software and allows any other app you can find. This security method is easier and faster to apply. It’s less restrictive, so it has a lower impact on the workflow, but it can be less safe than whitelisting.
Application Control Features
There are seven main application control features to consider. Three of them are related to user accounts, while the remaining four deal with data handling. Here’s a brief explanation for each:
- Identification, which ensures user account credentials are accurate and distinct.
- Authentication, which consists of verification system controls for all applications.
- Authorization, which certifies that approved users only have access to the company network of applications.
- Completeness checks, which confirm that traffic flow records are processed from start to finish.
- Validity checks, which warrant that only valid data inputs are processed by the application control technology.
- Input controls, which guarantee the integrity of the data feeds that are fed into the system.
- Forensic controls, which check that the data is mathematically and scientifically correct.
Application Control Benefits
Application control helps you see and decide which software runs in your network—and how it behaves. It’s especially useful if your team uses their own devices (BYOD). Here’s how it strengthens your security and improves operations:
Custom rules for every app
Application control helps with policy creation. It lets you set rules for specific apps—allowing, blocking, or limiting what they can do. This isn’t just about blacklists or whitelists. You can filter based on app name, file path, certificate, publisher, or hash. It gives you stronger control over what’s allowed to run, and helps you stop unknown or risky software before it causes problems.
Smarter access controls
You can also use application control to decide who can use certain apps. This supports identity-based policies, a core part of the Zero Trust model. In Zero Trust, no one is trusted by default – not even inside your network. Application control helps you enforce that by ensuring only the right people can access sensitive apps or sensitive data.
See what’s really happening in your network
Application control makes app activity visible. It doesn’t just track network traffic – it identifies apps by behavior or signature, even if they hide in normal web traffic. Through application control the security team can:
- spot unauthorized software
- see what applications are running and who’s using them
- catch suspicious behavior early
It’s especially helpful for monitoring users with elevated access, reducing the risk of insider threats.
Make the most of your bandwidth
By setting different rules for different apps, you can give priority to the tools that matter most. Think: boosting bandwidth for video calls or business-critical apps, while limiting social media or background updates. That means smoother performance where it counts.
Stronger admin control with PAM
When paired with Privileged Access Management (PAM), application control adds another layer of protection. PAM limits admin rights to only what’s needed – a core security best practice. Together, they make sure only approved users can run sensitive apps, and that elevated sessions stay secure from misuse.
Built-in audit trails
If something goes wrong, application control helps you look back and understand what happened. It keeps detailed logs of user actions, which makes it easier to investigate incidents and work with regulators or law enforcement if needed.
Helps you stay compliant
Application control also supports compliance with standards like NIST AC-1.6 and other global security frameworks, like NIS2. That’s not just a box to check – it shows your business takes cybersecurity seriously, and it helps protect you from fines, breaches, and reputational damage.
Application Control Best Practices
Securing your perimeter today means more than just blocking applications. It’s about finding the right mix of privilege management and granular control.
To build smart, flexible policies that keep out unwanted applications and stop malicious software before it causes harm, you need to understand what application types your people use. Equally important, you need to monitor and anticipate how they use them. Solid policy creation and well-placed security controls at the endpoint level ensure your team gets the access they need – nothing more, nothing less – so application usage stays both secure and streamlined.
So, here’s a list of best practices I advise you to use for your application control strategy.
Implement whitelisting as the primary control
Application whitelisting is a proactive security measure that permits only authorized applications to execute on a system, effectively blocking unauthorized software and malware. This approach is recommended by NIST as it focuses on allowing known good applications rather than trying to block known bad ones.
Use blacklisting to complement whitelisting
While whitelisting is more effective, blacklisting can serve as a supplementary control by blocking known malicious applications. However, relying solely on blacklisting is less secure, as it cannot prevent the execution of unknown or new malicious software.
Tailor policies to specific users and departments
Develop application control policies based on the principle of least privilege, ensuring that users have access only to the applications necessary for their roles. This reduces the attack surface and minimizes the risk of unauthorized software execution.
Plan and deploy strategically
According to NIST, implementing application control should involve thorough planning and analysis. A phased deployment allows for testing and adjustment, ensuring minimal disruption. Consider the operational environment; for instance, whitelisting is particularly effective for centrally managed hosts with consistent workloads.
Maintain regular software updates
Regularly update and patch all authorized applications to address newly discovered vulnerabilities. Use automated patch management tools to ensure consistency and reliability in the update process.
Heimdal® Application Control
How to Implement Application Control with Heimdal®
Until this point of this article, you’ve gained proper knowledge surrounding this cybersecurity strategy called “application control”. Now, moving on to a more practical part, I want to highlight what Heimdal has to offer and how easily you can gain control over your applications with the Heimdal Application Control software.
Our product works on two aspects: the what and the how, being designed to control what processes will be executed on the client machine and how this is going to happen. You can utilize Application Control to speed up the approval or denial process for files with default rulings, as well as establish or alter flows for specific users or AD groups.
This product stands for a module under the Heimdal Agent, being managed by the Heimdal’s ProcessLock service. This service has the role to make sure every started process is captured and verify if it can or cannot be allowed to run. In the context of Application Control, we are talking about two types of processes: blocked processed and allowed processes. The first category involves the creation of a block rule in the Dashboard in order to stop a process from running. This rule can be created on the basis of software name, paths, publisher, MD5, signature, or wildcard path. In the second case, an “allow rule” should be created in the Dashboard to allow a process to run. The same ruling as mentioned above considering name path etc. can be followed.
What’s interesting to mention here is that App Control blocks a process, as it is intercepted by our product and stopped in a matter of 5-seconds. On the other hand, the allowance of a process execution happens as App control intercepts it and checks the process status through the blocking repository.
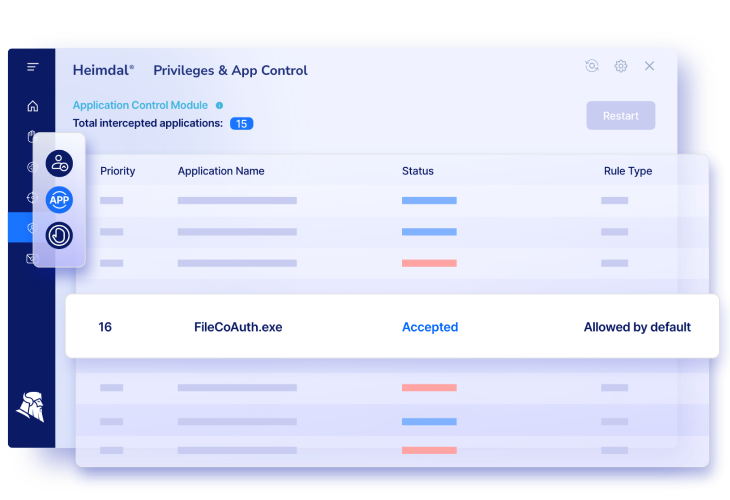
On the Heimdal Agent, the App control module will display data about the configured rule’s priority along with the name of the application, its rule type, and also the elevation status.
Application Control Settings
Among our general Application Control Settings, some important ones could be mentioned:
- The Full Logging Mode by means of which the Heimdal Agent is able to intercept any process executing on those endpoints that apply that group policy;
- The Zero – Trust Execution process protects against zero-hour threats by checking the unsigned executable files and stopping them to run if they are found untrusted;
- The reporting mode – all processes are scanned and logged with Zero-Trust Execution Protection.
Application Control Rules
You can set App Control Rules by taking into account various conditions like
- Rule value and rule type that allow you to set rules by their type: Software name, Path, Publisher, Signature or Wildcard path;
- Priority: the priority value and the priority level being interlinked;
- Action–defined processes can be allowed or blocked.
This is a basic presentation of our product to give you a general picture of its characteristics and its operability. However, if you want to learn more you can find here all the technical aspects of the Heimdal Application control module.
Wrap Up
Most organizations rely too much on traditional antivirus in their fight against cyber threats. But application usage is not something to ignore. Application control is essential, especially if you run a BYOD environment. This security tool helps protect sensitive data, enforces privilege management, and gives you granular control over what runs in your system.
Heimdal takes that application control even further – offering a higher level of visibility, policy flexibility, and security.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security