Contents:
Imagine the scenario: an employee at your company has innocently decided to install an add-on to their browser to help with time management.
Except there’s a catch.
The browser extension has been hacked by cybercriminals, who can exploit it as a backdoor into your company’s systems.
However, if your organization uses application allowlisting – also known as ‘whitelisting’- the add-on would have been automatically blocked before the employee could install it. Since the extension wasn’t on the approved list of safe apps, employees are barred from downloading dangerous code.
Application allowlisting has been around for many years. Nevertheless, one 2021 survey found that less than a third of organizations use allowlisting – even though security authorities like the United States NIST recommend it.
If you aren’t yet using application allowlisting, this article will get you up to speed on:
- What application allowlisting is
- Why application allowlisting is important
- How it works
- How to implement application allowlisting
- Challenges of application whitelisting/allowlisting
What is application allowlisting?
Application allowlisting has been described by one expert as: “arguably, the most effective first line of defense against initial endpoint compromise”.
The principle is simple: only pre-approved apps can be installed and run on your company’s endpoints, devices and networks. Since many kinds of breach happen when employees unintentionally download or install problematic code, application allowlisting stops this from happening. Application allowlisting typically forms part of an organization’s Privileged Access Management policy.
Any app (or code, script, library etc.) that they try to install that hasn’t been previously approved is immediately blocked. As a result, only apps that are trusted can run on your systems.
You can think of application allowlisting as a little like the guestlist at a party. There is a queue of people waiting to get into the party, but at the door, there is a bouncer, who has a very strict guestlist. If someone’s name isn’t on the guestlist, they can’t enter the event.
In this analogy, the party is your network, the people queuing are apps, and the bouncer’s guestlist is like an application allowlist. If an app’s name is not on the list, it cannot get in.
Learn more: Complete overview of application control
Application allowlisting vs blocklisting
Application allowlisting is often seen as an alternative to application blocklisting (or ‘blacklisting’), although the two approaches can be used simultaneously.
A blocklist is usually included with antivirus software. It contains a list of all known dangerous apps or code. If an employee tries to download an app/code on the blocklist, it is immediately blocked. Users are, however, free to download any other software that isn’t on the blocklist.
The problem with blocklisting is that it depends on your antivirus being up to date and ‘knowing’ about all possible kinds of malicious code. But given the ever-growing number of ‘zero day’ exploits, where hackers exploit previously unknown loopholes in software, blocklisting cannot cover every possible risk.
On the other hand, application allowlisting is much stricter. Only known, approved apps or code can be installed on your endpoints.
Suggested: What is privileged access management?
Why is application allowlisting important in cybersecurity?
Using application allowlisting provides several key benefits:
Reduces the attack surface
Having an allowlist significantly reduces your organization’s attack surface. For example, one of the most common ways criminals get into company systems is by using phishing emails. One method they use is to share links that download keylogging software (which lets attackers steal usernames and passwords). But if you are using an allowlist, employees won’t be able to download that code – and the breach is prevented.
Mitigates remote work risks and ‘bad’ behavior
When people are working from home, they’re more likely to take part in risky behavior while using company devices. At the office, users are simply less likely to visit dangerous websites (e.g. pirated sports websites) and accidentally download malicious code. Similarly, people working in cafes might use unsecured Wi-Fi. Staff should be educated about these risks, but if your devices have application allowlists on them, you have an extra defense layer. Even cybersecurity conscious employees will drop the ball sometimes, and so allowlisting reduces the risk further.
Ensures IT ‘hygiene’
Having an application allowlist prevents employees from downloading large numbers of apps and tools to your environment. This helps with security, control and general information management. It’s not good practice for different employees to be using dozens of apps – an allowlist means everyone is ‘on the same page’ when it comes to the tools you use. More generally, it forms part of privileged access management best practices.
Supports compliance
Application allowlisting helps you to comply with many cybersecurity and data management regulations.
Does application allowlisting really work? Cybersecurity professionals say it does:
We had two virus infections in six months a couple years ago. One of them was cryptolocker and took down a server half a day while I restored backups. Anyway, I then implemented [application allowlisting] and we haven’t had a single virus on a PC since.
Source – ‘turkeytipper’ on Reddit
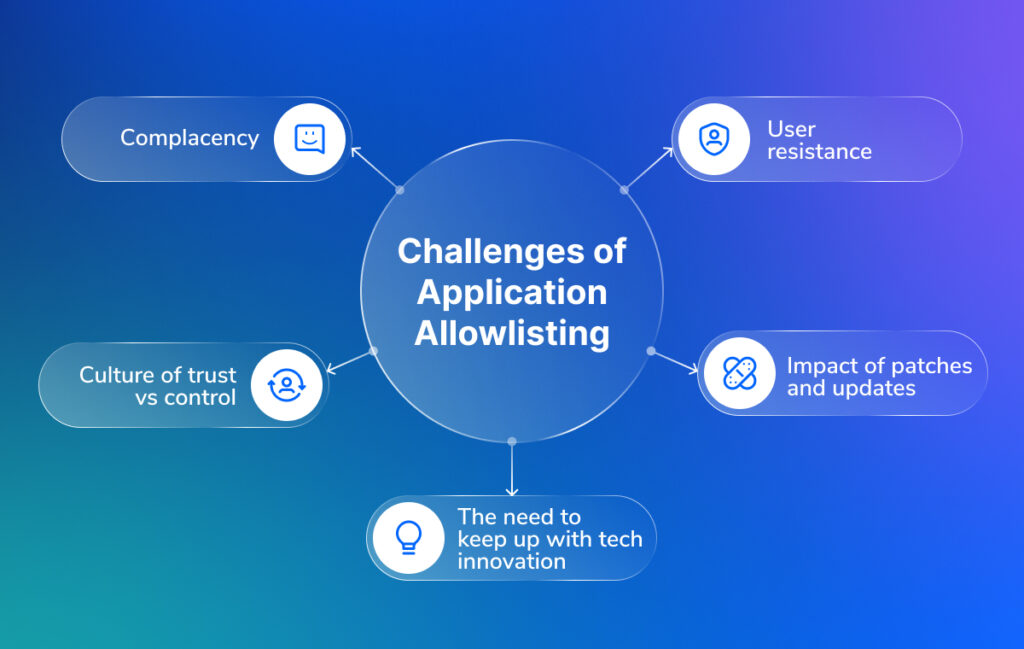
Challenges of application allowlisting
Despite its many benefits, application allowlisting can be very challenging to implement.
User resistance
One of the most common challenges with whitelisting your apps is user resistance. Employees get frustrated when they are unable to install software or run code that they need/want to do their jobs. In some cases, they might try to evade restrictions, thus exposing devices to security risks.
Patches and updates
Software updates can play havoc with more simplistic allowlists. New versions can change the applications, meaning they get blocked when users try to update them.
Tech and innovation
Companies often want to use new technologies to boost productivity or efficiency. Having an allowlist can slow them down if they wish to trial new apps and tools.
Culture of trust vs control
Many organizations want to give employees a degree of trust to make decisions about the apps and tools they use – they are adults, after all! An overly strict allowlist can undermine this sense of autonomy.
Complacency
Having an application allowlist may breed complacency. There are still other ways hackers can ‘get in’ – not least by finding loopholes into the backend of ‘trusted’ apps that are on your allowlist.
Make it comprehensive: Discover the platform approach to cybersecurity
How do application allowlisting solutions work?
While it is possible to create your own application allowlist, most companies use a third-party solution to do it instead. Creating your own allowlist can be very time-consuming and unwieldy.
Application allowlist software works as follows:
Audit
The tech will audit all apps, code and libraries currently on your network and produce a list.
Compiling the allowlists
You then specify exactly which software is and isn’t allowed on your network and endpoints. Depending on your security posture, permission might be given based on:
- Software name (e.g. Microsoft Office, Mozilla Firefox)
- File name
- Vendor/software publisher (e.g. Adobe, Salesforce)
- Cryptographic hash (a unique value for an application file)
Define exceptions
Most application allowlisting tools will let you create various exceptions and rules. For example, people with certain job titles may be permitted to bypass the allowlist. You might also wish to provide time-limited exceptions, that let people download certain apps for a specific purpose so long as IT gives their approval.
Operation
Once the allowlist is configured, it acts like a filter on every endpoint in your network. The moment someone tries to download a non-approved app, the allowlist blocks it. Typically, a message will be shown to the user explaining why they can’t download a file/app.
How to implement application allowlisting
Many companies use Heimdal’s Application Control solution to implement allowlisting. Here is our recommended approach to application allowlisting.
Initiate discovery
Using Extended Detection & Response, you can carry out a complete audit of all apps and code on devices in your network.
Design your application allowlist
Create a detailed list of applications that will be allowed to run on your systems. For all but the smallest organizations, this will usually be relatively complex. You want your allowlist to be nuanced – it should facilitate work for people who need to download apps frequently (e.g. software developers), while being more restrictive for others (e.g. admin staff).
Our Application Control technology lets you:
- Define privileged access so certain users can bypass settings
- Connect with our Patch and Asset Management tools, so all allowlisted apps can be updated without then becoming blocked
- Control how apps operate on endpoints
Test, test and test again
We strongly recommend you thoroughly test the allowlist on a wide variety of users before rolling it out to the entire organization. There can be many unforeseen consequences of barring certain apps or code. By thoroughly testing the allowlist, it’s more likely the rollout will be a success.
Monitor the allowlist
As with any technology process, it’s important to continually monitor the allowlist, ensure new threats aren’t being let in through the allowed apps, gathering user feedback, and adjusting settings as appropriate.
Close down security risks with application allowlisting
Application allowlisting is one of the most effective methods of narrowing your organization’s attack surface. While it does have challenges – particularly around user acceptance and rollout – the benefits mean it really is worth investing in.
Ready to introduce application allowlisting at your organization? Discover Heimdal’s easy-to-use Application Control solution and start your journey today.
Frequently asked questions
We answer your FAQs about application allowlisting.
Is it better to use my operating system’s whitelisting tools or a third party solution?
Many OSs have their own in-built application whitelisting/allowlisting tools where you can set rules about what apps can be downloaded. Using the OS’s inbuilt tools is usually enough for individual users or very small businesses. But for larger companies with many apps and users, a third party solution makes the process much faster. Equally, if you’re using more than one OS, it is much easier to manage the allowlist when using a third party tool.
I have an EDR tool. Do I also need an application allowlist?
If you have installed an EDR tool, this is a great way of monitoring devices on your network. However, this won’t prevent people from downloading risky apps or code. If you also have an application allowlist, it will further reduce your attack surface.
Why is it important to test an application allowlist?
Implementing an application allowlist or whitelist can have unintended consequences. It might stop people from using apps that are vital to their productivity, losing the business money and creating distrust towards IT. Extensive testing will help you understand what apps and processes should be permitted and make the implementation of the allowlist much smoother.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security