Contents:
New Ring doorbell encryption solution has been provided by Amazon for video and audio traffic security. So, from now on, if you have a Ring camera that records who enters your place or who’s near your home, this data is not so easily made available to law enforcement or anyone.
What’s Ring Doorbell?
Amazon owns Ring, a company that offers smart security for your home. The Ring doorbell is basically a home-security device that monitors (video and audio) who is at your door every time it detects motion. So, even if you are not at home, the Ring doorbell will record everything and you can see the video through your Ring app.
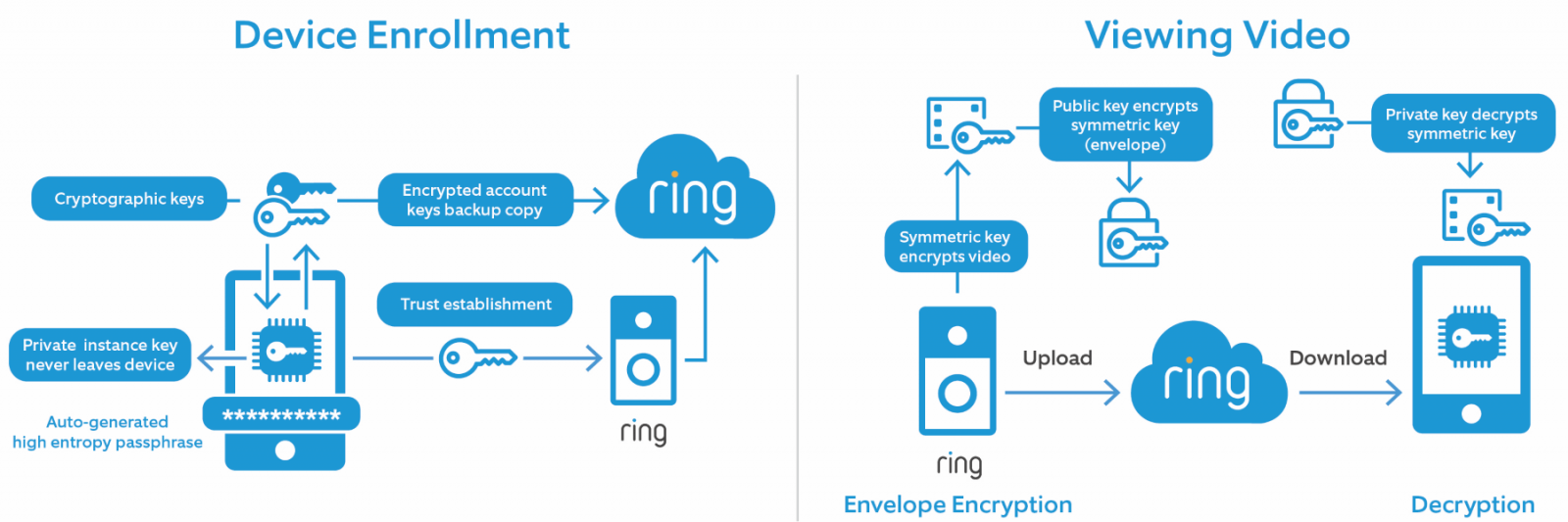
Now, customers around the world, with eligible Ring devices, can opt into video End-to-End Encryption, to add an extra layer of security that only allows their videos to be viewed on their chosen mobile device. This advanced security option is simple to set up via the Ring app, and offers additional peace of mind and protection.
What Does This New Ring Doorbell Encryption Do?
If until now, the videos recorded by your Ring doorbell could be easily accessed by a malicious hacker or the police, now the new E2EE (End-to-End Encryption) provided by Amazon makes video private by encrypting them.
Here’s how it works:
- Keep in mind that this E2EE is not automatically enabled, so you’ll have to select the feature in your privacy app setting.
- In order to do this, you should install a new Ring application version on your smartphone.
- This will use a security system named PKI (Public Key Infrastructure) that is based upon RSA 2048-bit asymmetric account signing.
- Now, only you have access to your videos, the decryption keys can be found only on the user’s mobile device: even the company itself cannot pass the encryption feature.
The company has had in plan earlier this year to perform a technical preview of the End-to-End Encryption. If Ring encrypted videos uploaded to cloud or servers in the past by default, now, with the new E2EE extra feature, nobody has access to the decryption key and video recording unless the owner of the device. So, law enforcement will not have automated access to your private data, you should provide it if required.
This measure comes as a result of the request made by The Electronic Frontier Foundation who asked Ring to work on this feature, stated BBC:
Consumers’ choice to buy a camera cannot and should not be a way to launder mass surveillance and streamline digital racial profiling.
Other Specifications
Following the new Ring doorbell encryption, you should also know, as ZDNet mentions:
- Besides opting for the E2EE feature, make sure you also use a passphrase. That’s because the Amazon Web Service Cloud (AWS) where recordings are stored does not make copies of the videos.
- E2EE is not implemented in all Ring doorbell features such as video sharing, Windows desktop app, Mac desktop app, and so on. Since they are not compatible with this new encryption, the features won’t work once enabling it.
- It also does not function together with a lot of Ring products. So, if you own a cheap ring doorbell, E2EE won’t run on it.
- Ring software versions 5.34.0 and higher, as well as Android 3.34.0 and higher, support Video E2EE.
Even if the police have no access to the video because of the ring doorbell encryption, they can post their request to users to Ring’s Neighbors App. Matthew Guariglia, an EFF analyst, also mentioned:
If your town’s police department has a partnership with Ring, you can also anticipate getting email requests from them asking for footage from your camera any time a suspected crime occurs nearby.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










