Contents:
You might be tempted to think that you’ve seen it all before as far as cyberattacks are concerned. Enter Ako ransomware, a strain discovered at the beginning of 2020 that is bound to take even the most seasoned experts by surprise. Although the infection starts with a pretty standard malspam campaign, it soon becomes clear that the way it spreads is unlike that of its predecessors. In this article, I will explain what Ako ransomware is, as well as how it encrypts your device. As always, stay tuned until the end for some actionable advice on how to protect your enterprise from a potential attack and what to do if it ends up happening anyway.
What Is Ako Ransomware?
Ako is a ransomware strain that was discovered on the 8th of January, 2020, when a user named Josh-SafeStorz posted on the BleepingComputer forum asking for technical assistance. According to the victim, both their Windows SBS 2011 server and their Windows 10 desktop were encrypted as a consequence of the attack. Just like other ransomware strains with higher media visibility, Ako spreads through malspam campaigns. The emails contain a deceptive text claiming that the attachment is “an agreement for you, as you requested” with an encrypted and password-protected .zip file attachment. The password is specified in the body of the message, and utilizing it pretty much opens Pandora’s box within your systems. The file within the .zip archive is one entitled “agreement” with a .scr extension, which pertains to screensavers and is widely used by cyberattackers. Scanning the file more thoroughly reveals that its extension is actually .exe, meaning that it is an executable file. Ako ransomware operates within two variants that are vastly alike. The only difference between them seems to be found in the imbursement instructions. While version 1 tells users to contact the attackers via an email address, version 2 directs them towards a Tor payment site.
Is Ako Ransomware MedusaLocker?
Bleeping Computer creator and owner Lawrence Abrams uncovered an older sample of Ako ransomware, which was subsequently analyzed by ethical hacker Vitali Kremez. As per the latter’s findings, the Ako strain was similar to MedusaLocker, a ransomware family discovered a few months before in September 2019. Comparably to MedusaLocker, Ako has “anti-Windows behavior”, targeting registry mapped drives and encrypting machines. This led the public to dub it MedusaReborn. However, it was soon clarified that was not the case and the two are not connected in any way. In an email message sent to BleepingComputer, Ako’s creators and operators confirmed that Ako ransomware had nothing to do with the infamous Medusa gang. In their words:
We see news about us. But that is wrong. About MedusaReborn. We have nothing to do with Medusa or anything else. This is our own product – Ako Ransomware, well, this is if you are of course interested.
During the brief exchange that followed, they called stealing user data before encrypting their “job”, which implies that they’re not in it solely for the ransom money.
How Ako Ransomware Encrypts Your Device
Now that you know what Ako ransomware is, let’s see what goes down when it encrypts your device. When it first infects a machine, it will execute the following three commands:
- It deletes shadow volume copies.
- It clears recent backups
- It disables Windows recovery.
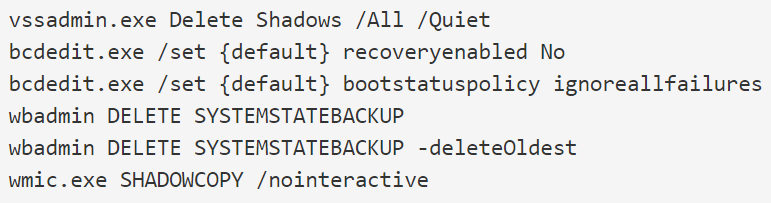
Image Source: BleepingComputer
Next, Ako will ensure that it can access mapped drives even in a User Account Control (UAC) process. This is achieved by creating the EnableLinkedConnections registry value and setting it to 1 under the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System key. After completing these steps, the ransomware starts encrypting your device. It is programmed to target all files that DO NOT contain the following extensions:
- .exe
- .dll
- .rdp
- .key
- .sys
- .ini
- .lnk
Besides fishing for extensions, Ako ransomware also encrypts files whose pathways DO NOT have the following strings:
- Program Files
- Program Files (x86)
- ProgramData
- AppData
- PerfLogs
- Boot
- Windows
- Intel
- Microsoft
- Tor Browser
Once a file is encrypted, it will be easy to detect since a randomly generated extension will be attached to its name. For instance, gerbil.jpg will become gerbil.jpg.XiQni6, which is a dead giveaway that someone has messed with your data. In addition to this, files will also have a CECAEFBE file marker as another indicator of encryption. As Ako ransomware encrypts the data stored on your machine, it will also ping scan the network for responsive machines, then target those as well. In this way, it manages to infect an entire online network perimeter at superspeed instead of focusing on individual workstations. After encryption, users will also find a text document on their desktops named “ako-readme”. In it are the instructions on how to reach the Tor website where the payment will be made or the contact email address. However, I do not recommend paying the requested amount of money. Not only should you never put money in the pockets of cybercriminals, but you don’t have any true guarantee that you will get your data back.
Quick Detection: Ako Ransomware IOCs
Indicators of compromise, or IOCs for short, are pieces of forensic cyber-data such as log entries or files that allow IT professionals to detect data breaches or malware infections faster. For your convenience, I have listed below the Ako ransomware IOCs that have been identified thus far, so you know what to watch out for from now on:
Main Object
- agreement.scr (.exe)
Associated Files
- ako-readme.txt
- id.key
Associated Registry Key
- HKEY_CURRENT_USER\Software\akocfg
Attacker Login IP
- 85.173.126.136
Email Sender IP
- 89.191.227.53
Hashes
- sha256 – c817a576455e0534b2500e57ec5c473febe6ca3c0211fe5a1cd96a619508d348
- sha1 – 6127f590e040902e820fbcebc2387fa9450e7ed2
- md5 – fd5ce9e0ebad9cca91399311b012063b
5 Ako Ransomware Protection Tips
1. Train Your Employees on Social Engineering Practices
Did you know that improperly trained employees are still the number one facilitating factor when it comes to cyberattacks? According to research authorized by the UK Information Commissioner’s Office (ICO), 90% of security breaches in the countries are caused by human error. This happens because, more often than not, people aren’t able to recognize the telltale signs of a ransomware attack. Let’s take the case of Ako to illustrate this. After a short analysis of its body and contents, there are several red flags in the malicious spam emails that spell out phishing:
- an encrypted .zip archive file,
- password protection on an attachment,
- and an unarchived file with a .scr extension.
What is more, the message itself was heavily reliant on social engineering practices. Its text mimicked common workplace conversations and even contained the “as you requested” meant to trick the user into ascribing legitimacy to the claim. For this reason, cyber education is the number one step towards a holistic online security approach. My advice: organize at least a few seminars, maybe even bring in an expert. In this way, you will minimize the risk of your employees getting tricked by (actually not so) clever social engineering.
2. Block File Extensions Associated with Ako Ransomware
As I previously mentioned, Ako ransomware is delivered in a .exe file that masquerades for a .scr one. One way to ensure that it doesn’t infect your network is by blocking these specific extensions, as well as other extensions that are commonly associated with malware, on company emails. Examples include .vbs, .js, .jar, .dll, and .tmp. However, it’s no secret that ransomware is delivered in file types that are usually circulated within a workplace, such as Microsoft Office and Adobe Reader files (.doc, .docx, .pdf, and so on). What do you do then? How do you prevent an Ako ransomware infection while at the same time not missing any important documents being sent? My recommendation is to strengthen your email service’s traditional filtering capabilities with an advanced solution such as our Heimdal™ Email Security. Not only does it stop spam, but it also detects malware and malicious phishing URLs, keeping your internal and external communication channels safe.
3. Always Update and Patch Your Software
Ransomware actors such as Ako and many others before (and after) it gains unlawful access into a network by exploiting system vulnerabilities. In turn, these weak spots are often created by unpatched and outdated software or applications. Therefore, I cannot stress enough how important it is to apply updates on all machines in your company as soon as they are released by their respective developers. This is where Heimdal’s Heimdal™ Threat Prevention enters the scene. Unless you create a custom schedule for it, our core offering will deploy any relevant patches within 72 hours of their release. Not only that, but it will also stop ransomware at the DNS-level with its DarkLayer Guard™ & VectorN Detection modules.
4. Install a Next-Generation Antivirus Solution
Ako ransomware gained notoriety by infecting entire networks at a time. Lately, it seems that hackers are abiding by the universal motto of go big or go home. To defend your business, your goal should be to go even bigger. Stay ahead of the curve with a full endpoint detection and response solution that will protect your enterprise against the cheekiest of attacks. Our Heimdal™ Next-Gen Antivirus & MDM has an integrated signature-based code scanning function that detects and prevents ransomware, as well as a multitude of other malicious threats. When merged with Foresight’s advanced DNS threat hunting capabilities, Vigilance becomes a complete cybersecurity resource. By their powers combined, the two form our Endpoint Security Suite of products that acts as your company’s watchtower and turret alike, all under one accessible roof.
5. Find an Ako Ransomware Decryptor (If You Can)
Has your enterprise already been infected by Ako ransomware? After the fact mitigation comes at a cost, which is why you should always check and see if an online decryption tool has been published first. Unfortunately, an Ako ransomware decryptor is not available as of yet. I recommend checking back to our article on ransomware decryption tools, where we constantly keep our readers updated with the latest releases. If one will be released into the wild in the future, you will definitely find it there.
To Sum It Up…
When it comes to dealing with Ako ransomware, prevention is your best bet. However, if you’ve had the misfortune of already being infected, do not pay the ransom. Back your data up offline, shut systems down within seconds of the first IOC and keep your eyes peeled for decryption tools. Mitigation costs might end up being higher than what hackers expect you to pay, but it’s not worth it in the long run. Trust me on this one.
Heimdal™ Ransomware Encryption Protection
Have you ever been infected by Ako ransomware? Do you have any tips? As always, feel free to leave your comments, questions, and concerns in the comments section below!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











