Contents:
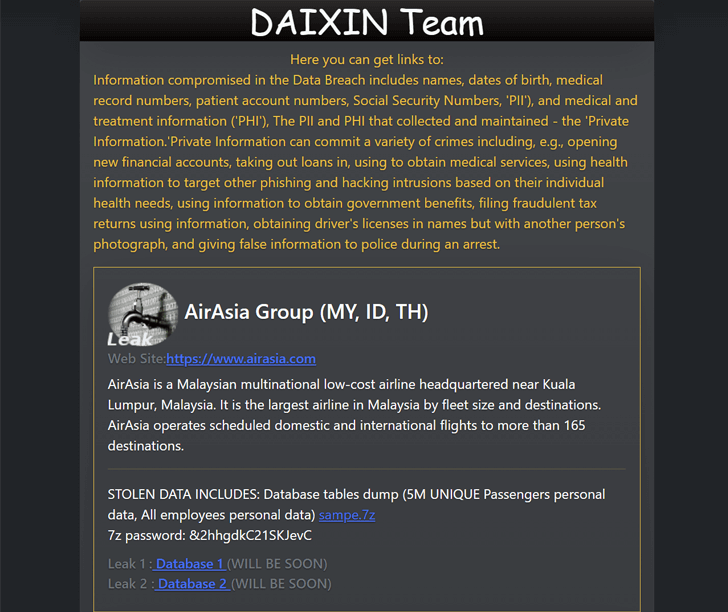
The Malaysian low-cost airline belonging to AirAsia had some of its data leaked by the cybercrime group known as Daixin Team, following a ransomware attack earlier this month.
The leaked data represents only a sample, as per the threat actors` claims, when in fact the stolen information belongs to five million unique passengers and all of the company`s employees. The published samples seem to confirm these allegations, as they include passenger information and the booking IDs as well as personal data related to the company’s staff, which further.
Irritating the Attackers
According to Daixin’s spokesperson, AirAsia had a rather quick response to the attack, asking the Daixin negotiator for an example of the stolen data and asked in great detail how it would be deleted in case of payment. AirAsia apparently did not try to negotiate the amount, which may, in fact, mean they had no intention of paying the ransom.
The actual amount demanded in exchange for the decryption key and deletion of all exfiltrated data is not known.
The same spokesperson claimed that further attacks were not pursued due to AirAsia’s poor security measures and chaotic organization of the network.
The chaotic organization of the network, the absence of any standards, caused the irritation of the group and a complete unwillingness to repeat the attack. […] The group refused to pick through the garbage for a long time. As our pentester said, “Let the newcomers sort this trash, they have a lot of time.”
Previous Mentions
Daixin Team was recently the subject of an advisory from the U.S. cybersecurity and intelligence agencies, which warned of attacks mainly targeting the healthcare sector, with victims such as Fitzgibbon Hospital, Trib Total Media and OakBend Medical among others.
When it comes to airlines being victims of cyberattacks, AirAsia Group is not the only Malaysian air carrier to suffer a breach. A security breach occurred via a third-party IT service provider exposing data of the Malaysia Airlines Enrich program between March 2010 and June 2019.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







