Contents:
Reports show that a recently found backdoor dubbed ‘Aclip’ that exploits the Slack API for covert communications is being used by an alleged Iranian state-sponsored cybercriminal.
The malicious actor began operating in 2019 by stealing airline reservations information from an unidentified Asian airline.
As per a report by IBM Security X-Force, the hacker is probably ITG17, also dubbed ‘MuddyWater’, which is a very active cybercrime organization.
Yesterday, my colleague Dora wrote about the recent discovery of a new espionage hacking effort targeting Middle Eastern and Asian telecommunications and IT service companies. The operation has been running for six months, and it may have connections to the same Iranian-backed actor, also known as MERCURY SeedWorm, or TEMP.Zagros.
What Is Slack?
According to Wikipedia, Slack is a proprietary business communication platform developed by American technology firm Slack Technologies and now owned by Salesforce.
Slack has several IRC-style functionalities, such as persistent chat rooms (channels) organized by topic, private groups, and direct messaging.
This kind of abuse has been used by other malicious actors before, so it’s not a new tactic. Slack isn’t the only genuine chat app that has been hacked to send data and commands privately.
In this instance, the Aclip malware uses the Slack API to transmit system information, documents, and screenshots to the C2 in, while receiving commands in return.
In March 2021, security researchers at IBM noticed the hackers exploiting this communication channel and immediately informed Slack.
Slack declared:
As detailed in this post, IBM X-Force has discovered and is actively tracking a third party that is attempting to use targeted malware leveraging free workspaces in Slack. As part of the X-Force investigation, we were made aware of free workspaces being used in this manner.
We investigated and immediately shut down the reported Slack Workspaces as a violation of our terms of service. We confirmed that Slack was not compromised in any way as part of this incident, and no Slack customer data was exposed or at risk. We are committed to preventing the misuse of our platform, and we take action against anyone who violates our terms of service.
Slack encourages people to be vigilant and to review and enforce basic security measures, including the use of two-factor authentication, ensuring that their computer software and anti-virus software is up to date, creating new and unique passwords for every service they use, and exercising caution when interacting with people they don’t know.
What Is Aclip Backdoor and How It Operates?
As explained by BleepingComputer, Aclip is a recently found backdoor that is launched by running a Windows batch script called ‘aclip.bat’.
Aclip is a recently found backdoor that is launched by running a Windows batch script called ‘aclip.bat’. The backdoor establishes persistence on a compromised machine by adding a registry key and launches automatically upon system startup.
Aclip gets PowerShell commands from the C2 server through Slack API functions and can then be used to perform additional commands, send screenshots of the active Windows desktop, and steal documents.
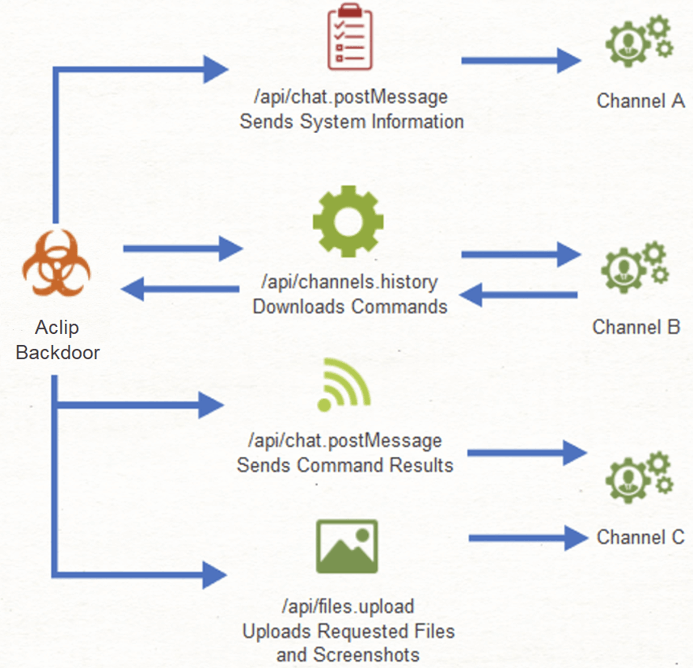
When the backdoor is first executed, it gathers basic system data such as the hostname, username, and external IP address. This information is encrypted with Base64 and sent to the attacker.
The command execution query stage then starts, with the malware connecting to a separate channel on the hacker-controlled Slack workspace.
PowerShell’s graphic library is used to capture screenshots, which are then saved to % TEMP % until exfiltration. The pictures are erased after they have been transferred to the C2.
IBM associated the attack to MuddyWaters/ITG17 after discovering two custom malware samples linked to the hacking group.
The investigation yielded two custom tools that correspond to malware previously attributed to ITG17, a backdoor ‘Win32Drv.exe,’ and the web shell ‘OutlookTR.aspx’.
Within the configuration of Win32Drv.exe, is the C2 IP address 46.166.176[.]210, which has previously been used to host a C2 domain associated with the Forelord DNS tunneling malware publicly attributed to MuddyWater.
How to Stay Safe?
- Frequently check PowerShell logs and module logging records;
- Limit PowerShell access to only specific commands and functions for each user;
- Disable or restrict Windows Remote Management Service;
- Create and use YARA rules to detect malicious PowerShell scripts.
Nevertheless, IBM warns that abuse of messaging apps will constantly evolve as organizations increasingly implement these solutions.
With a wave of businesses shifting to a permanent or wide adoption of a remote workforce, continuing to implement messaging applications as a form of group production and chat, X-Force assesses that these applications will continue to be used by malicious actors to control and distribute malware undetected.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










