Contents:
Threat actors are trying to capitalize on the Kaseya ransomware attack by targeting potential victims in spam campaigns that are pushing Cobalt Strike payloads disguised as Kaseya VSA security updates in what seems to be a Kaseya malspam campaign.
Cobalt Strike is a commercial, full-featured, remote access tool that bills itself as “adversary simulation software designed to execute targeted attacks and emulate the post-exploitation actions of advanced threat actors”.
Cobalt Strike’s interactive post-exploit capabilities cover the full range of ATT&CK tactics, all executed within a single, integrated system, therefore in short Cobalt Strike is a legitimate penetration testing tool and threat emulation software.
Unfortunately, the threat actors are also using this tool for post-exploitation tasks and the deployment of so-called beacons that can allow them to gain remote access to compromised systems.
These attacks have as final goal to either harvest and exfiltrate sensitive data or to deliver second-stage malware payloads.
Interestingly, 66 percent of all ransomware attacks this quarter involved red-teaming framework Cobalt Strike, suggesting that ransomware actors are increasingly relying on the tool as they abandon commodity trojans.
How Does the Malspam Campaign Operate?
This malspam campaign was discovered by the researchers at Malwarebytes Threat Intelligence and it seems to be using two different tactics to deploy the Cobalt Strike payloads.
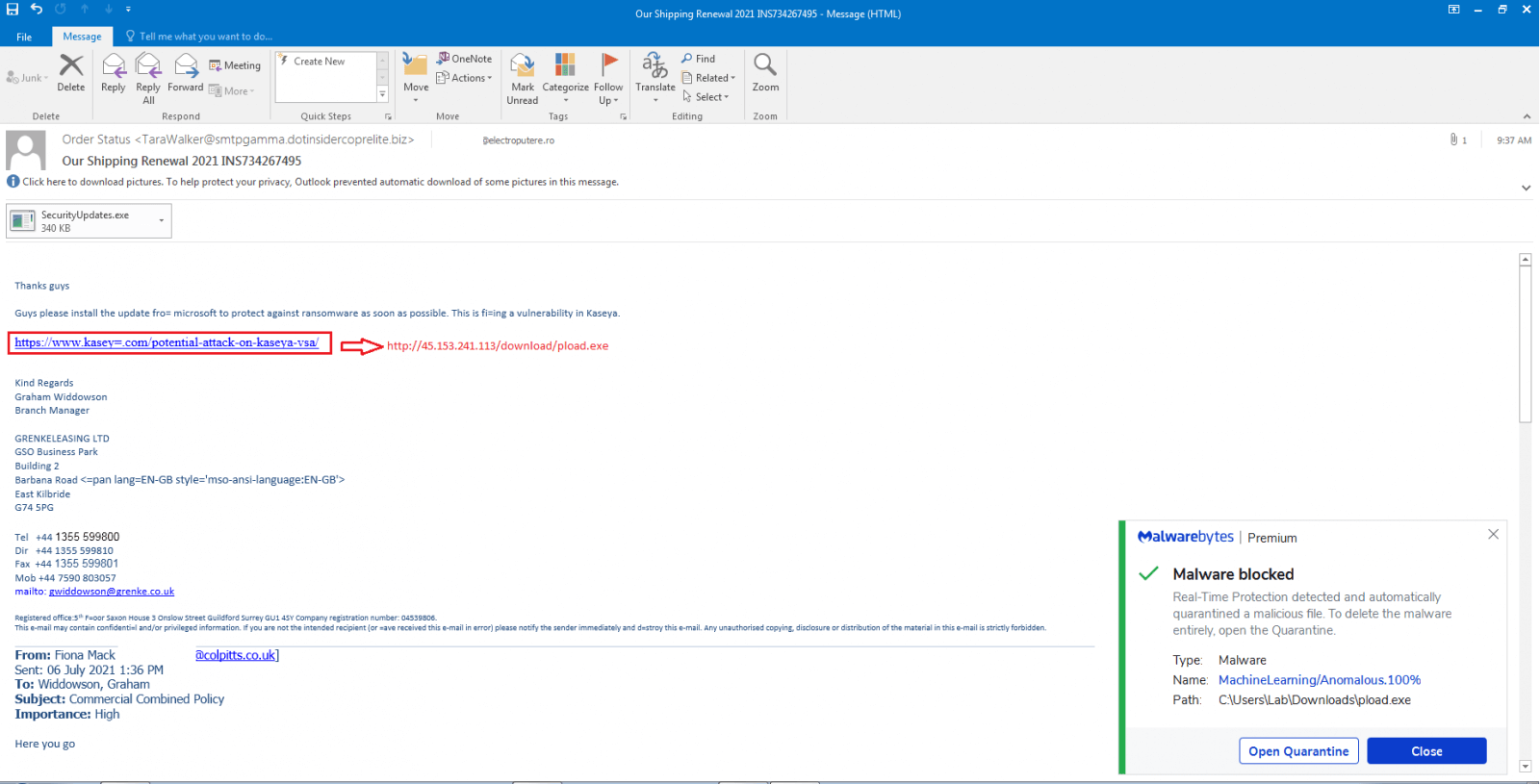
The emails that get sent as part of this type of campaign are coming loaded with a malicious attachment and contain an embedded link designed to look like a Microsoft patch for the Kaseya VSA zero-day vulnerability that got exploited in the REvil ransomware attack.
A malspam campaign is taking advantage of Kaseya VSA ransomware attack to drop CobaltStrike.
It contains an attachment named ‘SecurityUpdates.exe’ as well as a link pretending to be a security update from Microsoft to patch Kaseya vulnerability!
The purpose of this campaign is for the attackers to gain persistent remote access to the target’s systems once the malicious attachment has been executed or at least to download and launch a fake Microsoft update on the victim’s device.
This phishing campaign comes soon after the REvil ransomware gang, also known as Sodinokibi, targeted MSPs with thousands of customers. The attack was highly publicized therefore a large number of Kaseya’s direct customers and downstream businesses became the perfect lure.
Kaseya has been at working hard in trying to fix the vulnerability in its VSA software, but it seems that the company has run into some glitches.
Cybercriminals routinely capitalize on panic stemming from newsworthy events. We saw it with COVID stimulus checks, vaccine availability and now with the Kaseya supply chain attack.
Even the best anti-malware solutions can be deceived by clever binary obfuscation techniques. As such, it’s critical to have layers of controls that anticipate failures of other controls. This is where continuous monitoring and proactive threat hunting really shine by providing the capability to identify potentially suspicious activities that manage to evade primary defenses.
Organizations need help to protect themselves against these types of scams, therefore it’s quite important for users as well to properly verify any sources of information and make sure they’re accurate before opening any attachments or sharing sensitive information.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










