Contents:
Trezor is a hardware cryptocurrency wallet that offers advanced security for storing and managing private keys for Bitcoin and other cryptocurrencies. Trezor allows users to conduct safe payments without exposing their private keys to a possibly hacked computer.
What Happened?
In order to steal cryptocurrency wallets and the assets kept inside them, a stolen Trezor hardware wallet mailing list was used to send bogus data breach alerts to the recipients.
When you click on the link in the phishing email you are directed to download a Trezor Suite lookalike app, that will ask you to connect your wallet and enter your seed. The seed is compromised once you enter it into the app, and your funds will then be immediately transferred to the attackers wallet.
This attack is exceptional in its sophistication and was clearly planned to a high level of detail. The phishing application is a cloned version of Trezor Suite with very realistic functionality, and also included a web version of the app.
When setting up a new Trezor, a 12- to 24-word recovery seed will be presented, which will enable users to retrieve their wallets in the event that their device is stolen or otherwise lost.
Anyone who knows the recovery seed, on the other hand, has the ability to obtain access to the wallet and the cryptocurrency it contains, making it critical to keep the recovery seed in a secure location.
The Trezor wallet users started getting data breach warnings, which instructed them to download a bogus version of the Trezor Suite software, which would steal their recovery seeds in exchange for their personal information.
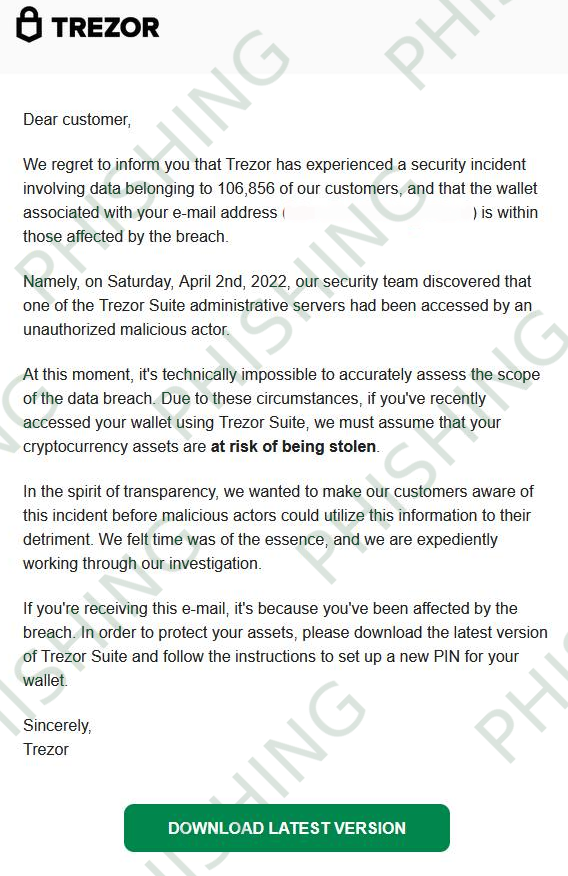
Trezor acknowledged that the emails in question were a phishing assault sent via one of their opt-in newsletters hosted by MailChimp, and that the company was not responsible for them.
We immediately took steps to disable phishing sites and are taking further steps to stop the continuation of this phishing attack.
As explained by BleepingComputer, because the Trezor Suite is open source, the threat actors were able to get the source code and develop their own modified version of the program that seems to be similar to the original, genuine application.
How Can Trezor Owners Remain Safe?
You should never input your recovery seed into any program or on any online page. The seed should only be put in once, on the Trezor device that you are attempting to recover from, and then deleted.
Another important action that users can take is to not respond to any emails purporting to be from Trezor and inform you that you have been the victim of a recent data breach.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










