Contents:
A researcher wanted to prove that a hacker could hijack a home network with ease by exploiting their lack of security, so he cracked 70% of a 5,000 WiFi network sample. This happened in Tel Aviv when he did the WiFi network cracking experiment, Tel Aviv being his hometown.
How Did the Researcher Do His Experiment?
The whole process unfolded as described below, according to the report this researcher published.
The researcher under discussion, by his name Ido Hoorvitch, took a walk in the center of the city and brought with him WiFi sniffing equipment. The intention was the collection of 5,000 network hashes that would help him carry out his research. The next step he followed was to exploit a vulnerability with the role to permit PMKID hash retrieval. This kind of hash is normally useful for roaming purposes.
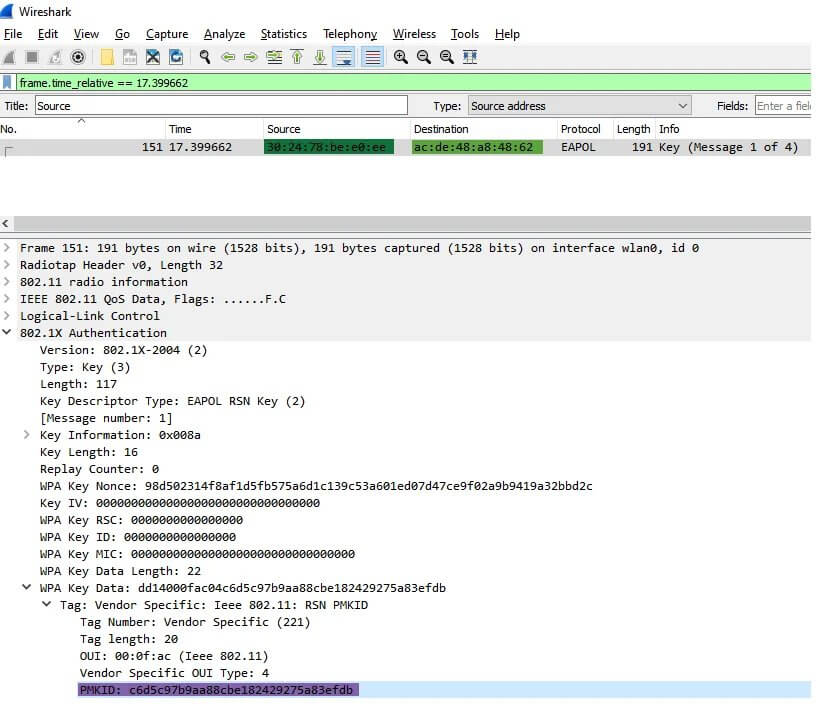
How PMKID hashes can be gathered? Well, he made use of two things: a network card to the tune of $50 and the tool that allows packet injection. Then, next, he used the free software WireShark for sniffing purposes. In that PMKID hash, one can find 4 things: the passphrase, the MAC address, the SSID of the network, and last, but not least a static integer.
The researcher made use of the Jens “atom” Steube’s method that already existed and belonged to the lead developer of Hashcat. What he managed through the mentioned method was to collect PMKIDs. These would be then useful to be cracked in order to get the password.
The next thing he did was to launch “Mask attacks”. This would help him discover if the users’ wifi passwords corresponded with their cellphone numbers, which is said to be a common practice in Israel. To get the password right, a calculation of the numbers’ options associated with phone numbers from Israel should be made. The researcher managed to crack no less than 2,200 passwords by means of a standard laptop. The average speed per password raised up to 9 minutes.
Then he used ‘Rockyou.txt’, a dictionary that allowed him to crack more passwords, more specifically 1,359, and most of those passwords contained lower-case characters.
All these supported his WiFi network cracking experiment.
The Reason Behind Weak Passwords
There are still users who do not implement the best cybersecurity practices, this leading to them being exposed to various cyber threats, and WiFi network cracking is just one of so many threats out there. From this research, it only comes out that people do not use strong passwords on their WiFi networks.
Tips for a strong password could be:
- Make sure it is long enough, about 10 characters, and that it does not contain merely lowercase letters or even short words with meaning. The password should be long enough, with all kinds of symbols, combining upper and lower case ones and also mixing letters and numbers.
- You can also try the Bruce Schneier method, think about a personal phrase, and change it into a password by using some of the phrase sequences. Like in his example from 2008: “This little piggy went to market might become tlpWENT2m.”
- Use a password manager that will generate strong passwords for you.
How to Stay Safe?
Cybersecurity has evolved and we at Heimdal™ know how to keep up with the latest cybersecurity trends. You can give it a try to our awarded Threat Prevention working on prevention rather than mitigation. It has a mind-blowing accuracy in preventing upcoming threats. However, our solutions work better together based on the concept of unified cybersecurity. Interesting? Take a look at our website!
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










