Contents:
67,995 customers of the sports betting company DraftKings had their personal data exposed in a credential stuffing attack.
The incident occurred in November 2022, and it seems that the threat actors got the customers’ account credentials from a source outside the organization.
Details About the DraftKings Attack
The data exposed in this data breach includes the name of the account holder, the user’s address, phone number, email, the last four digits of card details, profile photo, data about prior transactions, account balance, and the data of the last new password.
At this time, there is currently no evidence that the attackers accessed your Social Security number, driver’s license number, or financial account number.
While bad actors may have viewed the last four digits of your payment card, your full payment card number, expiration date, and your CVV are not stored in your account.
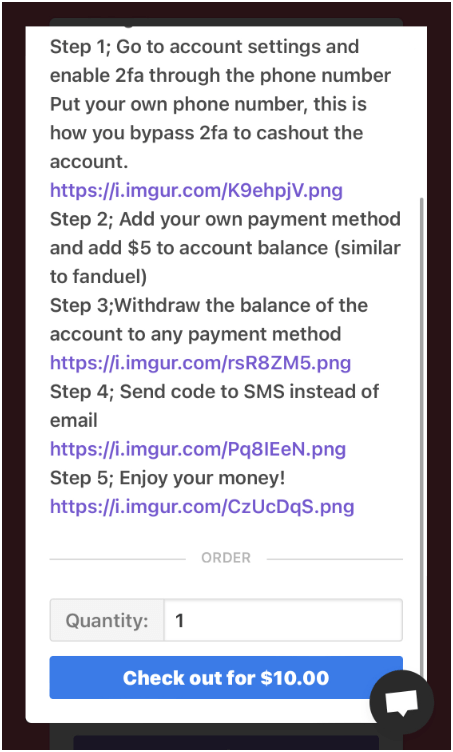
The accounts that got hijacked received a $5 deposit and a new password changed by the cybercriminals who then were enabling two-factor authentication (2FA) on a different phone number to be able to take as much money as possible from the victim’s linked bank account.
Stolen credentials were sold on the dark web for $10 to $35 and they came with instructions about how to withdraw the money from the bank accounts linked to them.
DraftKings reset the passwords for all the accounts that were affected by the attack and implemented new anti-fraud measures. The company also refunded up to $300,000 that was stolen by hackers from its clients.
What Is a Credential Stuffing Attack?
A credential stuffing attack means that a great number of sign-in attempts (even millions of them) to an account are made using automated tools. These attempts are using stolen credentials and the success of the attack resides in the habit of reusing login information on multiple platforms.
After compromising an account, threat actors steal personal and financial information that they later sell on the dark web or used in identity theft scams that can result in unauthorized purchases or empty banking accounts.
To stay safe from such attacks, DraftKings advises customers to avoid using the same credentials for different accounts, not to share them with third-party platforms, to use 2FA whenever possible, and to remove banking details from online platforms.
Credential stuffing attacks are more and more used by threat actors who can conduct such actions by purchasing ready-made tools and credentials lists.
In September, identity and access management company Okta also reported that the situation has drastically worsened this year since it recorded over 10 billion credential-stuffing events during the first three months of 2022.
This amounts to roughly 34% of the overall authentication traffic tracked by Okta, which means that one in three sign-in attempts are malicious and fraudulent.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









