Contents:
A ransomware gang targeting an Israeli company allowed security specialists to trace a portion of a ransom payment to the website of a sensual massage parlor, BleepingComputer reports.
Who Was Behind the Attack?
Dubbed Ever101, the ransomware operation compromised an Israeli computer farm and moved forward to encrypting its devices. Profero and Security Joes researchers, who performed incident response on the attack, believe that the Ever101 is a variant of the Everbe or Paymen45 ransomware.
We were able to establish that the EVER101 ransomware is almost identical to a number of ransomware families, such as CURATOR and Paymen45, both of which are believed to be developed by the EverBe group. Our hypothesis is that this ransomware was built through a “Ransomware-as-a-Service” builder, rather than being fully developed by the threat actor or group, whose identity and location remain unknown.
When encrypting files, the ransomware will attach the .ever101 extension and add a !=READMY=!.txt ransom note in each folder on the computer.
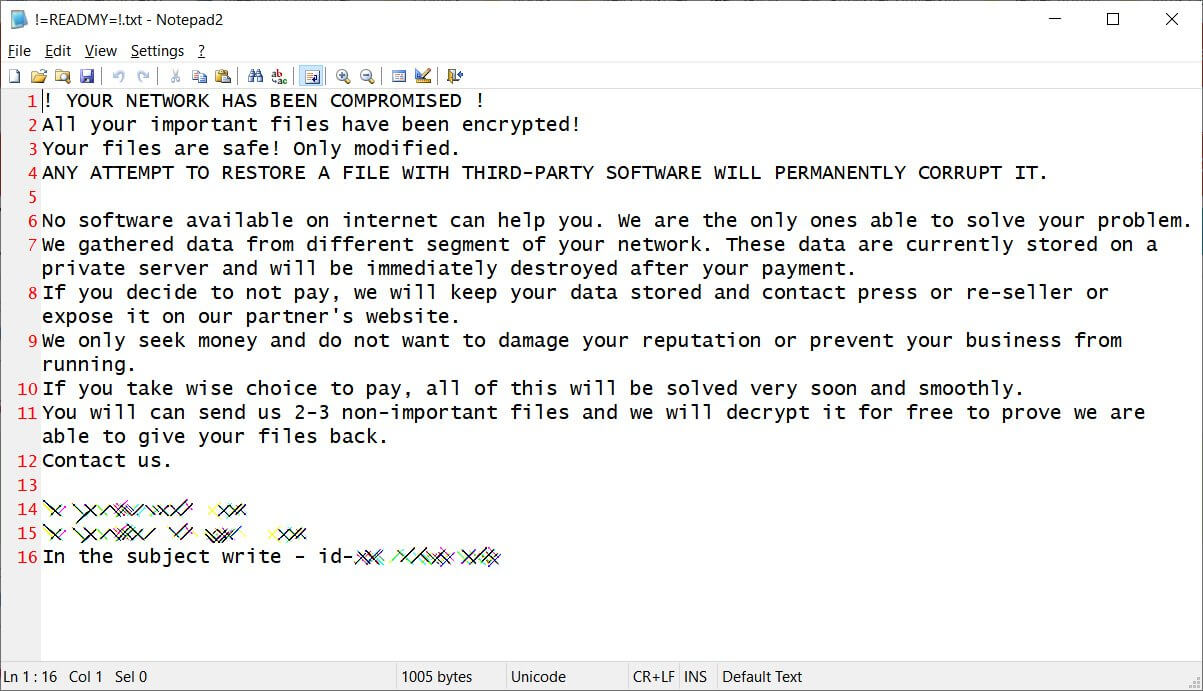
Image Source: BleepingComputer
A ‘Music’ folder that contained various tools used during the attack was discovered by the researchers during their investigation. This shed some light on the attacker’s techniques.
During our investigation of the infected machines, we came across what seemed to be a treasure trove of information stored in the Music folder. It consisted of the ransomware binary itself, along with several other files—some encrypted, some not—that we believe the threat actors used to gather intelligence and propagate through the network.
How Did They Do It?
Among the tools used by the Ever101 ransomware gang, the researchers found:
- xDedicLogCleaner.exe – used to clear any logs on the system, something that commonly occurs during ransomware attacks;
- PH64.exe – is a copy of the ProcessHacker binary;
- Cobalt Strike – a “go-to” tool for ransomware operators;
- SystemBC7 – a well-known proxy malware used to hide communications between a malware implant and a command and control server.
Based on the names and other characteristics, the researchers believe the ransomware gang used the following tools as well:
- SoftPerfect Network Scanner – because a large majority of the attacker’s tools were encrypted with the ransomware, this tool is considered unconfirmed;
- shadow.bat – this file was discovered in an encrypted state on one of the infected machines;
- NetworkShare_pre2.exe – this tool is commonly used by threat actors to enumerate a network for shared folders and connected devices.
Since the ransom payment flowed through different bitcoin wallets, the researchers used CipherTrace to track it down. This way, they found out that a small portion, 0.01378880 BTC ($590), was sent to a ‘Tip Jar’ on the RubRatings website.
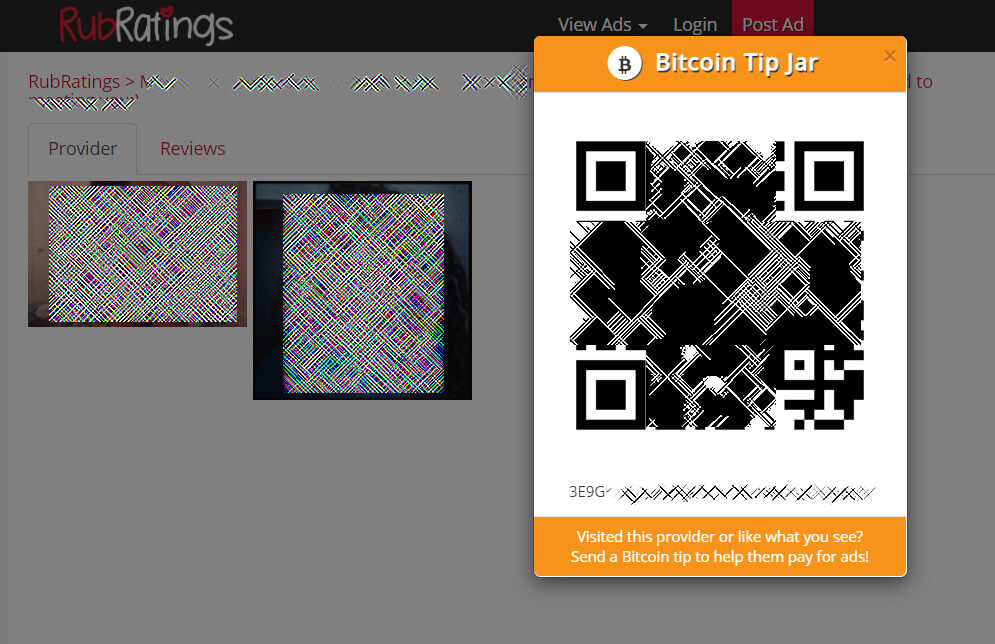
Image Source: BleepingComputer
Most likely, the threat actors created a fake account on RubRatings and used the Tip Jar feature as a way to launder the ransom by making it look like a tip to a masseuse.
The second possibility is that the provider on the site was used as another method of obfuscating the bitcoin movement. It could be that the provider who possesses the bitcoin wallet in question was working with the threat actor(s), but more likely, it is a fake account set up to enable money transfers. The bitcoin in the wallet linked to RubRatings received the payment around 15:48 UTC, and it left the wallet just a few minutes later, at 15:51 UTC.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










