Contents:
Zyxel urges users to apply patches for three critical vulnerabilities impacting two of its end-of-life NAS products
Security researcher Timothy Hjort reported 5 vulnerabilities in Zyxel products:
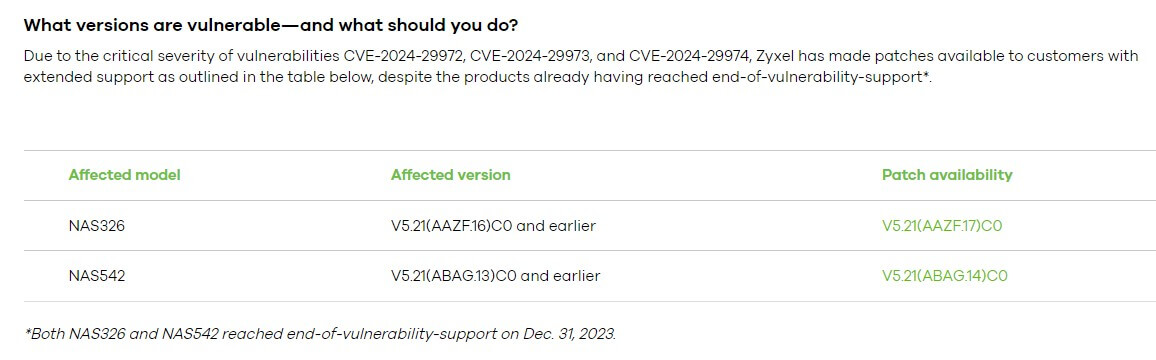
- NAS326, version V5.21(AAZF.16)C0 and earlier
- NAS542, version V5.21(ABAG.13)C0 and earlier
Three of the flaws are critical and enable command injection and remote code execution (RCE) attacks.
End-of-life means that the vendor no longer supports the product, but due to these three critical vulnerabilities, Zyxel announced making an exception.
What are the five Zyxel vulnerabilities?
For the moment, Zyxel says there is no proof of hackers exploiting the vulnerabilities in the wild. But there’s already an available proof-of-concept available on the Internet. So, users should apply the available patches as soon as possible.
According to BleepingComputer.com, Zyxel only released fixes for CVE-2024-29972, CVE-2024-29973, and CVE-2024-29974. You can download patches here.
Here’s a list and description of all 5 Zyxel vulnerabilities:
CVE-2024-29972
CVE-2024-29972 is a command injection vulnerability in the CGI program “remote_help-cgi”. An unauthenticated attacker can exploit it to run commands on some operating system (OS), by sending a crafted HTTP POST request.
CVE-2024-29973
This is also a command injection flaw. CVE-2024-29973 resides in the “setCookie” parameter of Zyxel NAS326 and NAS542 devices. Just like CVE-2024-29972, CVE-2024-29973 can enable unauthenticated hackers to run OS commands through crafted HTTP POST requests.
CVE-2024-29974
This remote code execution vulnerability was found in the CGI program “file_upload-cgi” in Zyxel NAS326 and NAS542. Hackers can use CVE-2024-29974 to execute arbitrary code by uploading a crafted configuration file to a compromised device.
CVE-2024-29975
CVE-2024-29975 is an improper privilege management vulnerability in the SUID executable binary in Zyxel NAS326 and NAS542. Hackers can exploit it to get administrator privileges and run system commands as the “root” user on an already compromised device.
CVE-2024-29976
This is another privilege management flaw, found in the command “show_allsessions” in Zyxel NAS326 and NAS542 devices. Once the attacker succeeds authenticating, they can exploit CVE-2024-29976 to gain a logged-in administrator’s session information containing cookies on a vulnerable device.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







